
Published on April 28th, 2024 | by admin
iSpeech.org Apr 28, 2024NewsroomCredential Stuffing / Data Breach Identity and access management (IAM) services provider Okta has warned of a spike in the "frequency and scale" of credential stuffing attacks aimed at online services. These unprecedented... Read More →

Published on April 27th, 2024 | by admin
https://www.ispeech.org/text.to.speech Apr 27, 2024NewsroomCyber Attack / Malware Cybersecurity researchers have discovered a targeted operation against Ukraine that has been found leveraging a nearly seven-year-old flaw in Microsoft Office to deliver Cobalt Strike on compromised systems. The... Read More →
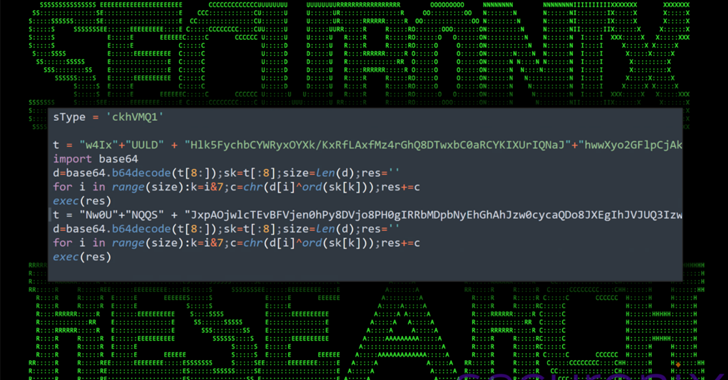
Published on April 27th, 2024 | by admin
iSpeech.org Apr 27, 2024NewsroomMalware / Software Security An ongoing social engineering campaign is targeting software developers with bogus npm packages under the guise of a job interview to trick them into downloading a Python backdoor. Cybersecurity... Read More →

Published on April 26th, 2024 | by admin
Text to Speech Voices Apr 26, 2024NewsroomSupply Chain Attack / Software Security Several security vulnerabilities disclosed in Brocade SANnav storage area network (SAN) management application could be exploited to compromise susceptible appliances. The 18 flaws impact... Read More →

Published on April 26th, 2024 | by admin
iSpeech Apr 26, 2024NewsroomSupply Chain Attack / Software Security Several security vulnerabilities disclosed in Brocade SANnav storage area network (SAN) management application could be exploited to compromise susceptible appliances. The 18 flaws impact all versions up... Read More →

Published on April 26th, 2024 | by admin
iSpeech.org Apr 26, 2024NewsroomSupply Chain Attack / Software Security Several security vulnerabilities disclosed in Brocade SANnav storage area network (SAN) management application could be exploited to compromise susceptible appliances. The 18 flaws impact all versions up... Read More →

Published on April 26th, 2024 | by admin
iSpeech.org Apr 26, 2024NewsroomSupply Chain Attack / Software Security Several security vulnerabilities disclosed in Brocade SANnav storage area network (SAN) management application could be exploited to compromise susceptible appliances. The 18 flaws impact all versions up... Read More →

Published on April 26th, 2024 | by admin
iSpeech In today's digital world, where connectivity is rules all, endpoints serve as the gateway to a business's digital kingdom. And because of this, endpoints are one of hackers' favorite targets. According to the IDC, 70%... Read More →

Published on April 26th, 2024 | by admin
iSpeech.org In today's digital world, where connectivity is rules all, endpoints serve as the gateway to a business's digital kingdom. And because of this, endpoints are one of hackers' favorite targets. According to the IDC, 70%... Read More →

Published on April 26th, 2024 | by admin
Text to Speech Apr 26, 2024NewsroomThreat Intelligence / Cyber Attack Threat actors are attempting to actively exploit a critical security flaw in the WP‑Automatic plugin for WordPress that could allow site takeovers. The shortcoming, tracked as... Read More →

Published on April 25th, 2024 | by admin
https://www.ispeech.org Apr 25, 2024NewsroomMalware / Cyber Threat The North Korea-linked threat actor known as Lazarus Group employed its time-tested fabricated job lures to deliver a new remote access trojan called Kaolin RAT. The malware could, "aside... Read More →

Published on April 25th, 2024 | by admin
Text to Voice While the major generative AI service providers depend on the cloud to power their large language models, Apple will be taking a different tack with the next version of its mobile operating system,... Read More →

Published on April 25th, 2024 | by admin
iSpeech Follow this real-life network attack simulation, covering 6 steps from Initial Access to Data Exfiltration. See how attackers remain undetected with the simplest tools and why you need multiple choke points in your defense strategy.... Read More →

Published on April 25th, 2024 | by admin
https://www.ispeech.org Apr 25, 2024NewsroomCryptocurrency / Cybercrime The U.S. Department of Justice (DoJ) on Wednesday announced the arrest of two co-founders of a cryptocurrency mixer called Samourai and seized the service for allegedly facilitating over $2 billion... Read More →


















Gloss