April 22nd, 2024 | 🕒
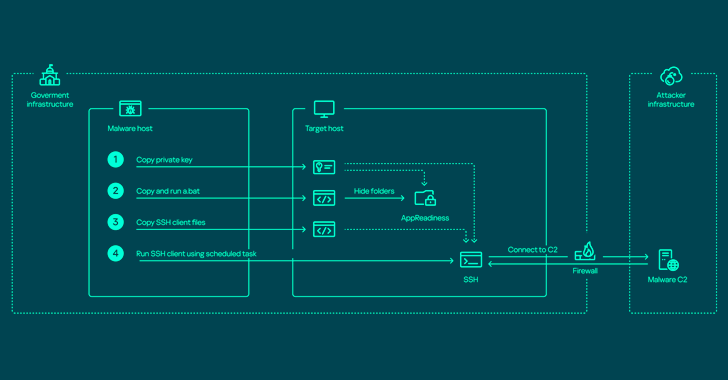
https://www.ispeech.org Apr 22, 2024NewsroomNetwork Security / Endpoint Security The threat actor known as ToddyCat has been observed using a wide
April 22nd, 2024 | 🕒
iSpeech.org Selecting the best computer for your business can be a straightforward process if you plan ahead. Check out these
April 22nd, 2024 | 🕒
iSpeech.org Over the past two years, a shocking 51% of organizations surveyed in a leading industry report have been compromised
April 22nd, 2024 | 🕒
iSpeech Between crossovers - Do threat actors play dirty or desperate? In our dataset of over 11,000 victim organizations that
April 22nd, 2024 | 🕒
iSpeech Apr 22, 2024NewsroomRootkit / Software Security New research has found that the DOS-to-NT path conversion process could be exploited
April 22nd, 2024 | 🕒
iSpeech.org Apr 22, 2024NewsroomCryptocurrency / Artificial Intelligence Microsoft has revealed that North Korea-linked state-sponsored cyber actors has begun to use












Gloss