What is Relected XSS And How to Use This.
TTS
What is Reflected XSS And How to Protect Attack
What is Reflected XSS
Reflected Xss are the most frequent type of Xss attacks found in the wild. Reflected Xss attacks are also known as non persistent Xss attacks and, since the attack payload is delivered and executed via a single request and response they are also referred to as first-order or type Xss.
Reflected XSS Using
By Using a Reflected or persistent XSS attack beef hooks into the given web site and allows the attacker control over the browser on the given page.BeeF integrates with Metasploit which allows an attacker to send browser exploits etc.To the users browser.You can steal data steal sessions etc.
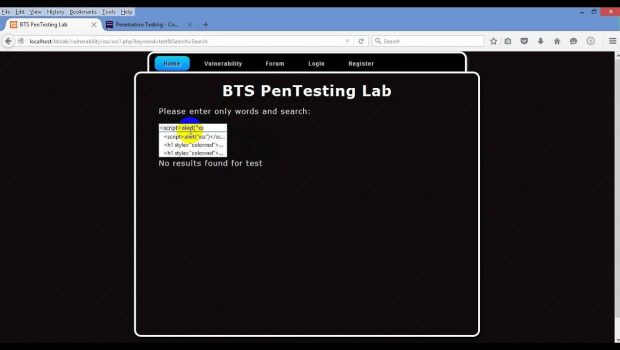
How To Test Reflected XSS
1 Detect input vectors. For each web page the tester must determine all the web applications user defined variables and how to input them.This includes hidden or non obvious inputs such as HTTP parameters POST data hidden form field values and predefined radio or selection values.Typically in browser HTML editors or web proxies are used to view these hidden variables. See the example below
2 Analyze each input vector to detect potential vulnerabilities.To detect an XSS vulnerability the tester will typically use specially crafted input data with each input vector.Such input data is typically harmless but trigger responses from the web browser that manifests the vulnerability.Testing data can be generated by using a web application fuzzer an automated predefined list of known attack strings, or manually.
I am Teaching in this video
cross site scripting xss learn reflected css complete xss reflected easy xss reflected xss reflected payloads easy to xss reflected reflected xss xss reflected how to reflected xss how to xss reflected
2015-11-10 16:38:16
source







Gloss