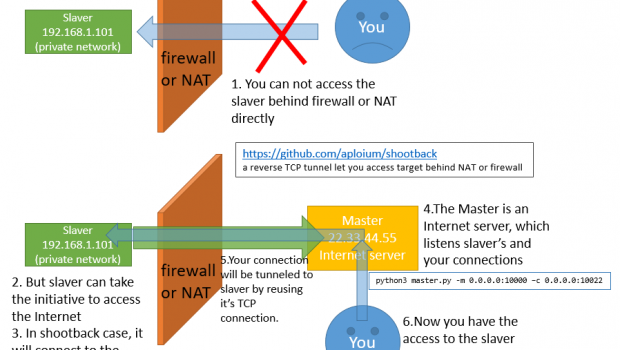
shootback: a reverse TCP tunnel let you access target behind NAT or firewall
https://www.ispeech.org/text.to.speech
shootback is a reverse TCP tunnel let you access target behind NAT or firewall
Typical Scene
- Access company/school computer(no internet IP) from home
- Make private network/site public.
- Help private network penetration.
- Help CTF offline competitions.
- Connect to device with dynamic IP, such as ADSL
Getting started
- requirement:
- Master: Python3.4+, OS independent
- Slaver: Python2.7/3.4+, OS independent
- no external dependencies, only python std lib
- download git clone https://github.com/aploium/shootback
- (optional) if you need a single-file slaver.py, run python3 build_singlefile_slaver.py
- run these command
- a more reality example:
assume your master is 22.33.44.55 (just like the graph above)[adsense size='1' ]
- for more help, please see python3 master.py –help and python3 slaver.py –help
Tips
- run in daemon:
nohup python(or python3) slaver.py -m host:port -t host:port -q &
or
- ANY service using TCP is shootback-able. HTTP/FTP/Proxy/SSH/VNC/…
- shootback itself just do the transmission job, do not handle encrypt or proxy.
however you can use a 3rd party proxy (eg: shadowsocks) as slaver target.
for example:
shadowsocks_server<–>shootback_slaver<–>shootback_master<–>shadowsocks_client(socks5)
- run in daemon:
Warning
- in windows, due to the limit of CPython
select.select(), shootback can NOT handle more than 512 concurrency, you may meet
ValueError: too many file descriptors in select()
- If you have to handle such high concurrency in windows, Anaconda-Python3 is recommend, it’s limit in windows is 2048







Gloss