Security Summary: In Development Heropoint Ransomware
iSpeech.org
This is a quick analysis of the in development infection called Heropoint Ransomware. This article will contain technical information related to how it infects a computer, how it is distributed, and whether it can be decrypted.
Heropoint Ransomware Summary
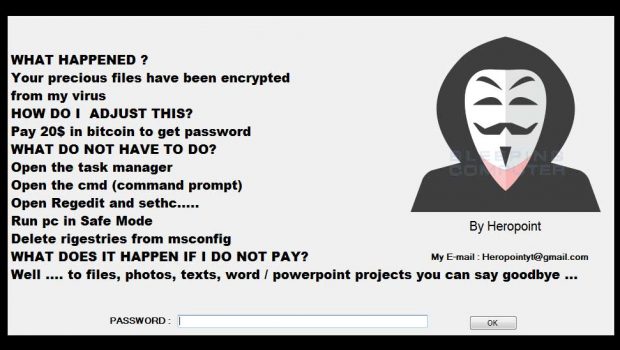
The Heropoint Ransomware is currently in development and at this point does not actually encrypt any files and just displays the following lock screen.

It does, though, contain a XOR routine, which is used to encrypt the files, but is overloaded by a function of the same name that returns a NotImplementedException. This causes the ransomware to skip the encryption of any files.

If it was to encrypt files, it would be currently targeting files that contain the following extensions:
.txt, .png, .ico, .mp3, .exe, .jpg, .pptx, .xlsx, .htlm, and .mp4 When encrypting a file it would then append a random numeric extension to the filename.

Method of Distribution
As this ransomware is currently in development, it is not being distributed at this time.
Can Heropoint Ransomware be decrypted?
As this ransomware is current in development, it is unknown if the final version will be decryptable.
How to protect yourself from Heropoint Ransomware
In order to protect yourself from the Heropoint Ransomware you should use standard security practices. This includes using good computing habits and security software. First and foremost, you should always have a reliable and tested backup of your data that can be restored in the case of an emergency, such as a ransomware attack.
[adsense size='1' ]
You should also have security software that incorporates behavioral detections to combat ransomware and not just signature detections or heuristics. For example, Emsisoft Anti-Malware and Malwarebytes Anti-Malware both contain behavioral detection that can prevent many, if not most, ransomware infections from encrypting a computer.
Last, but not least, make sure you practice the following security habits, which in many cases are the most important steps of all:
- Backup, Backup, Backup!
- Do not open attachments if you do not know who sent them.
- Do not open attachments until you confirm that the person actually sent you them,
- Scan attachments with tools like VirusTotal.
- Make sure all Windows updates are installed as soon as they come out! Also make sure you update all programs, especially Java, Flash, and Adobe Reader. Older programs contain security vulnerabilities that are commonly exploited by malware distributors. Therefore it is important to keep them updated.
- Make sure you use have some sort of security software installed that uses behavioral detections or white list technology. White listing can be a pain to train, but if your willing to stock with it, could have the biggest payoffs.
- Use hard passwords and never reuse the same password at multiple sites.
IOCs
Heropoint Ransomware Hashes:
SHA256: 07d467c5c0f8f0131294ff65afd1d5911169c73821753c7807d2de9c61c9d7eaHeropoint Ransomware Ransom Note:
WHAT HAPPENED ?
Your precious files have been encrypted
from my virus
HOW DO I ADJUST THIS?
Pay 20$ in bitcoin to get password
WHAT DO NOT HAVE TO DO?
Open the task manager
Open the cmd (command prompt)
Open Regedit and sethc.....
Run pc in Safe Mode
Delete rigestries from msconfig
WHAT DOES IT HAPPEN IF I DO NOT PAY?
Well .... to files, photos, texts, word / powerpoint projects you can say goodbye ...Targeted File Extensions:
.txt, .png, .ico, .mp3, .exe, .jpg, .pptx, .xlsx, .htlm, and .mp4Associated Email Addresses:
Heropointyt@gmail.com






Gloss