RIPS – A static source code analyser for vulnerabilities in PHP scripts
The amount of websites has increased rapidly during the last years. While websites consisted mostly of static HTML files in the last decade, more and more webapplications with dynamic content appeared as a result of easy to learn scripting languages such as PHP and other new technologies. In fact, PHP is the most popular scripting language on the world wide web today. Besides a huge amount of new possibilities, the new web 2.0 also brings a lot of security risks when data supplied by a user are not handled carefully enough by the application. Different types of vulnerabilities can lead to data leakage, modification or even server compromise. In the last year, 30% of all vulnerabilities found in computer software were PHP-related 1.
In order to contain the risks of vulnerable webapplications penetration testers are hired to review the source code. Given the fact that large applications can have thousands of codelines and time is limited by costs, a manual source code review might be incomplete. Tools can help penetration testers to minimize time and costs by automating time intense processes while reviewing a source code.
In this submission a tool named RIPS is introduced which automates the process of identifying potential security flaws in PHP source code by using static source code analysis
Features:
detect XSS, SQLi, File disclosure, LFI/RFI, RCE vulnerabilities and more
5 verbosity levels for debugging your scan results
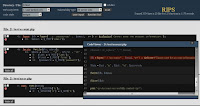
mark vulnerable lines in source code viewer
user-defined function code by mouse-over on detected call
list of all user-defined functions and program entry points (user input) connected to the source code viewer
create CURL exploits for detected vulnerabilties with few clicks
7 different syntax highlighting colour schemata
only minimal requirement is a local webserver with PHP and a browser
Download: https://sourceforge.net








Gloss