Networks Take Center Stage in OT Cybersecurity| ARC Advisory
Summary
Industrial companies need strong cybersecurity programs to deal with today’s sophisticated threat environment. They have become prime targets for ransomware and sophisticated nation-state attacks. Digital transformation efforts are also expanding attack pathways with unmanageable IoT devices, as well as an explosion in external connections to cloud services, vendors, and remote workers.
Many industrial facilities have invested in basic cybersecurity defenses but lack the resources and security management tools to sustain their effectiveness. Most facilities also lack adequate visibility into assets and system behavior to detect new vulnerabilities and system compromises before they have operational impact. Companies want to address these critical security gaps, but they are concerned about the operational disruptions that often occur when new technologies and practices are introduced into existing systems.
This Insight describes the cybersecurity capabilities needed to deal with today’s cyber threats and the major gaps in existing OT cybersecurity programs. It highlights the critical role that networks play in enabling secure facilities and the benefits of solutions that are pre-integrated with network infrastructure. A review of Belden’s security offerings shows how one industrial networking company has enhanced their product and service offerings to help companies address OT security challenges.
Today’s Threats Demand Better Industrial Cybersecurity
ARC’s Industrial/OT Cybersecurity Maturity Model provides a useful tool for understanding the status of industrial cybersecurity programs. This model provides a roadmap for implementing the security technologies, cybersecurity management solutions, and human resources needed to support the NIST cybersecurity framework recommendations. The colors in the model also distinguish basic passive defensive measures needed to protect systems against conventional hackers, from the active defense capabilities needed for today’s sophisticated attacks.
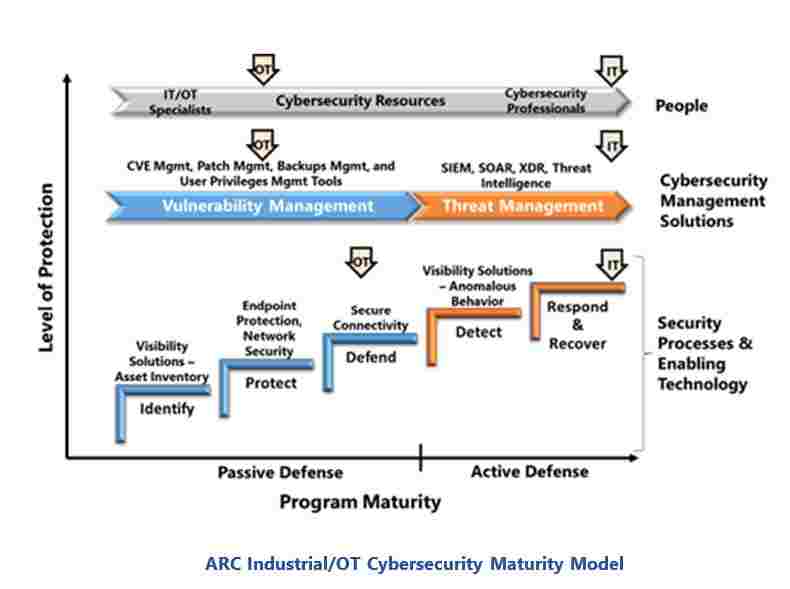
A key benefit of the ARC model is how it highlights the need to maintain alignment of people, processes, and technology capabilities. Security technologies must be maintained to be effective and security teams need the right tools to effectively perform these tasks. Likewise, cybersecurity professionals are only effective when they have good visibility of risks and the ability to rapidly isolate and remediate threats. The real effectiveness of a cybersecurity program, or its maturity, is determined by the weakest element.
As the figure shows, most industrial IT cybersecurity programs are significantly more mature than those for OT. IT security programs include passive and active defenses. They also have teams of cybersecurity professionals and advanced cybersecurity management solutions that help them maintain security posture and manage attacks. Sophisticated attackers may compromise these systems, but rapid detection, isolation, and remediation enable security teams to minimize the impact.
Typical OT cybersecurity programs only have passive defenses and many lack the people and security tools to maintain them. Few OT systems have the active defense capabilities needed to detect and manage ransomware and sophisticated attacks. They likewise lack the resources and expertise to ensure secure deployment of new digital transformation efforts.
The current state of OT cybersecurity is placing many facilities at risk of serious cyber incidents. And these risks are growing rapidly, with attackers becoming more sophisticated, companies deploying unmanageable IoT devices, and connections with external resources proliferating. Closing the maturity gaps between OT and IT cybersecurity programs is an urgent issue that every facility needs to address.
Better Cybersecurity Requires Better Networking Capabilities
Industrial companies recognize the need to close OT cybersecurity gaps. Company leaders want to minimize the risks cyberattacks pose to operations. This has driven more CISO involvement in OT cybersecurity and more convergence of IT and OT cybersecurity teams. These developments should alleviate the people and process weaknesses. But, as the ARC model illustrates, the effectiveness of these efforts will be limited unless comparable improvements are made to the OT security and security management technologies.
Industrial networks represent the biggest obstacle and the biggest opportunity for improving OT cybersecurity. Many OT systems still have legacy networks with limited capabilities for blocking attacks, isolating assets, and monitoring network activities. Updating these networks with modern security management features will give defenders the visibility and control they need to rapidly detect and manage new threats. The ultimate goal should be to achieve OT network security capabilities that are comparable to those that exist in IT networks. This includes:
- Network switches, routers, and firewalls that support today’s granular security policies and micro-segmentation that allows isolation of individual assets.
- Centralized network management that enables fast, efficient management of all system networks and networking devices.
- Automatic collection of detailed information about every connected asset and all data flows that occur within the system.
- Network access control (NAC) capabilities that automatically detect and validate new devices, as well as support convenient management of all device and user access privileges.
- Secure remote access capabilities that reflect the criticality and lack of device security capabilities in OT systems. This includes limiting pathways for external attacks on OT assets; restricting user access to specific network segments, devices, and operations; enabling by-invitation-only remote access; and the ability to continuously monitor, record, and terminate all remote sessions.
Industrial plants have been operating with inadequate cybersecurity for too long. Addressing OT system security gaps is essential to deal with today’s sophisticated threats and digital transformation risks. Upgrading legacy OT networks is recommended as the first step as this will ease integration of more cybersecurity resources and adoption of modern security practices and solutions. Most industrial networking suppliers offer products and services to help you make a painless transition to a modern secure OT networking environment.
Belden Fills Critical Security Gaps
Belden’s Industrial Automation Solutions build the foundation for real-time decisions, with a comprehensive portfolio of networking, connectivity, and network security products to support industrial networks and ensure the secure transmission of data. With a focus on key industrial verticals crossing discrete manufacturing, process facilities, energy and mass transit, Belden is focused on enabling customer outcomes and solving their biggest challenges.
Belden Cybersecurity Solutions
As Belden continues its transition from an individual product to a complete solution provider, their products are becoming more tightly integrated and sophisticated. Their broad portfolio of Cybersecurity Solutions reflects these developments. Cybersecurity has become an integral part of Belden’s Industrial Automation Solutions strategy and they address most of the critical areas in ARC’s cybersecurity maturity model. The company also offers services to ease customer efforts to take advantage of these capabilities.
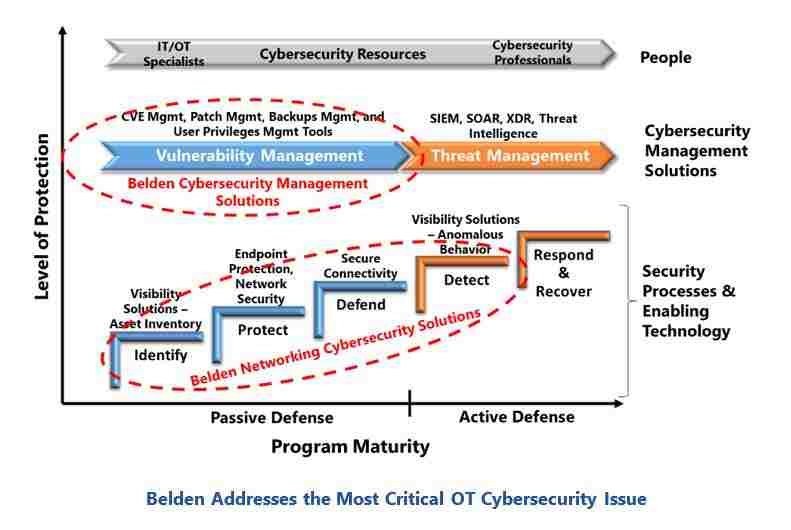
Belden’s industrial cybersecurity solutions provide the visibility and protection that companies need to defend facilities against cyberattacks that could threaten safety, product quality, and productivity. This includes industrial networking cybersecurity solutions that are fully integrated with a corresponding suite of cybersecurity management solutions that help companies maintain the security posture of their facilities.
Industrial Networking Cybersecurity Solutions
Belden’s industrial switches, routers, and gateways provide users with full control of network access and message flows. The company also offers a portfolio of cybersecurity-specific network appliances that enable development and enforcement of granular security policies within networks and connections with external resources.
This includes:
- Firewall solutions for core-to-edge protection of assets within OT networks (Hirschmann and Tofino). Ongoing developments in these product lines ensure that the company can support unique applications in any critical industrial settings, and specific automation system requirements, like Emerson, Schneider Electric, ABB, and Eaton.
- Secure, high-performance routers for WAN and industrial cellular applications.
- Secure network access (Belden macmon Network Access Control (NAC)).
- Third party visibility tools where the sensor technology integrates in Hirschman Eagle firewall hardware.
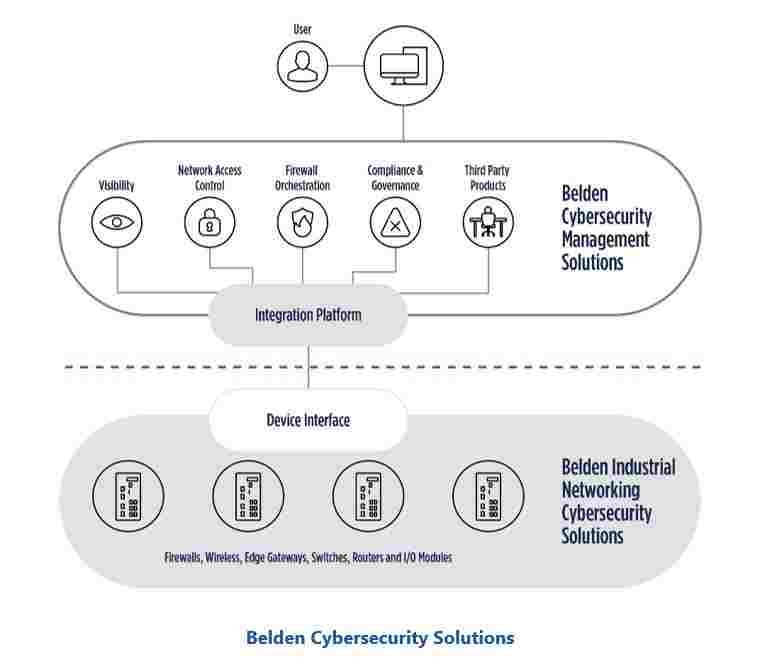
Cybersecurity Management Solutions
Belden’s cybersecurity management solutions include the tools that users need to fully leverage network cybersecurity capabilities. This includes:
- Visibility: User friendly dashboards that provide access to detailed asset inventory information and security alerts generated by Industrial Visibility tools.
- Network Access Control: macmon network access control management console that manages authentication of devices requesting system access and provides the means for users to create and enforce granular access controls through SNMP, HTTPS, or SSH/Telnet commands to network devices (Belden or others). Secure remote access capabilities are also available through macmon SDP and ProSoft Connect.
- Firewall Orchestration: HiSecOS, which powers the security features within Hirschmann firewall products; HiVision, which provides efficient mapping and management of Hirschmann and other SNMP-enabled devices within a factory’s network; and Provize, which provides a convenient topological view of all network devices as well as the ability to manage their status.
- Compliance & Governance: This solution provides an agentless solution for monitoring OT devices for changes and configuration compliance, including Windows and Linux file systems; reduces manual effort to summarize policy and compliance efforts; alerts on unexpected changes; and provides vulnerability risk scoring.
- Third Party Products: Belden’s cybersecurity management offering has pre-tested integrations with a variety of third-party products, like Rockwell FactoryTalk AssetCentre, MDT AutoSave, Kepware etc. They also offer custom integrations for other products end users may want to connect.
Belden Cybersecurity Services Reduce Upgrade Concerns
Belden offers a broad range of services through their global Customer Innovation Centers (CICs) and partner networks, including technical consulting, project management, service, and support as well as custom solutions for complex customer problems. Their global team of engineers and consultants have extensive field experience and application-specific expertise in critical industries like mass transit, discrete manufacturing, process automation, energy, and smart buildings. They simplify the complexities, and accelerate the design and implementation of robust, reliable, and secure industrial network infrastructure for customers to achieve better business performance.
Belden cybersecurity services include system assessments against industry and customer-defined security standards and recommendations as to what is needed for today and tomorrow’s cybersecurity challenges. Belden also has a global network of installers and partners with the networking knowledge to ensure that security recommendations are implemented in a way that ensures proper operation and minimal (if any) disruption to current operations.
Conclusion
Threats to industrial operations have outpaced the capabilities of most OT cybersecurity programs. Many facilities lack the security resources, technologies, and cybersecurity management tools to defend operations against ransomware and sophisticated attackers. They also lack people and expertise to ensure security of digital transformation efforts and expanded use of remote workers. Today’s OT security teams face the same security challenges as their IT counterparts, and they require comparable capabilities. No company can afford to ignore the growing risks of serious cyber incidents.
This Insight discussed the major weaknesses in OT cybersecurity people, processes, and technologies. It highlighted the critical role that industrial networks play in enabling better OT cybersecurity and outlined the improvements that most facilities require. It also notes the importance of involving a trusted network infrastructure provider in the design and implementation of network upgrades to reduce the risks of operational disruptions. The review of Belden’s products and services show that there are companies who can help you ensure a smooth transition. So, the biggest risk to OT security is users ignoring the urgency in addressing these critical issues.
This material was drawn from ARC Advisory Group’s ongoing coverage of industrial cybersecurity. Further information on the Belden Industrial Cybersecurity Solutions is available here.
ARC Advisory Group clients can view the complete report at ARC Client Portal
If you would like to buy this report or obtain information about how to become a client, please Contact Us
Keywords: OT Cybersecurity, Network Security Solutions, Belden, ARC Advisory Group.







Gloss