Microsoft warns Astaroth malware campaign is after your credentials
Microsoft announced today the discovery of many ongoing malware campaigns by the Windows Defender ATP team.
These campaigns distribute the Astaroth malware in a fileless manner, which makes it even more dangerous.
Speaking of malware campaigns, you can nip them in the bud with these antimalware tools.
Here’s how a Microsoft Defender ATP researcher described the attacks:
I was doing a standard review of telemetry when I noticed an anomaly from a detection algorithm designed to catch a specific fileless technique. Telemetry showed a sharp increase in the use of the Windows Management Instrumentation Command-line (WMIC) tool to run a script (a technique that MITRE refers to XSL Script Processing), indicating a fileless attack
What is Astaroth and how it works?
If you didn’t know, Astaroth is a well-known malware focused on stealing sensitive information like credentials and other personal data and sending it back to the attacker.
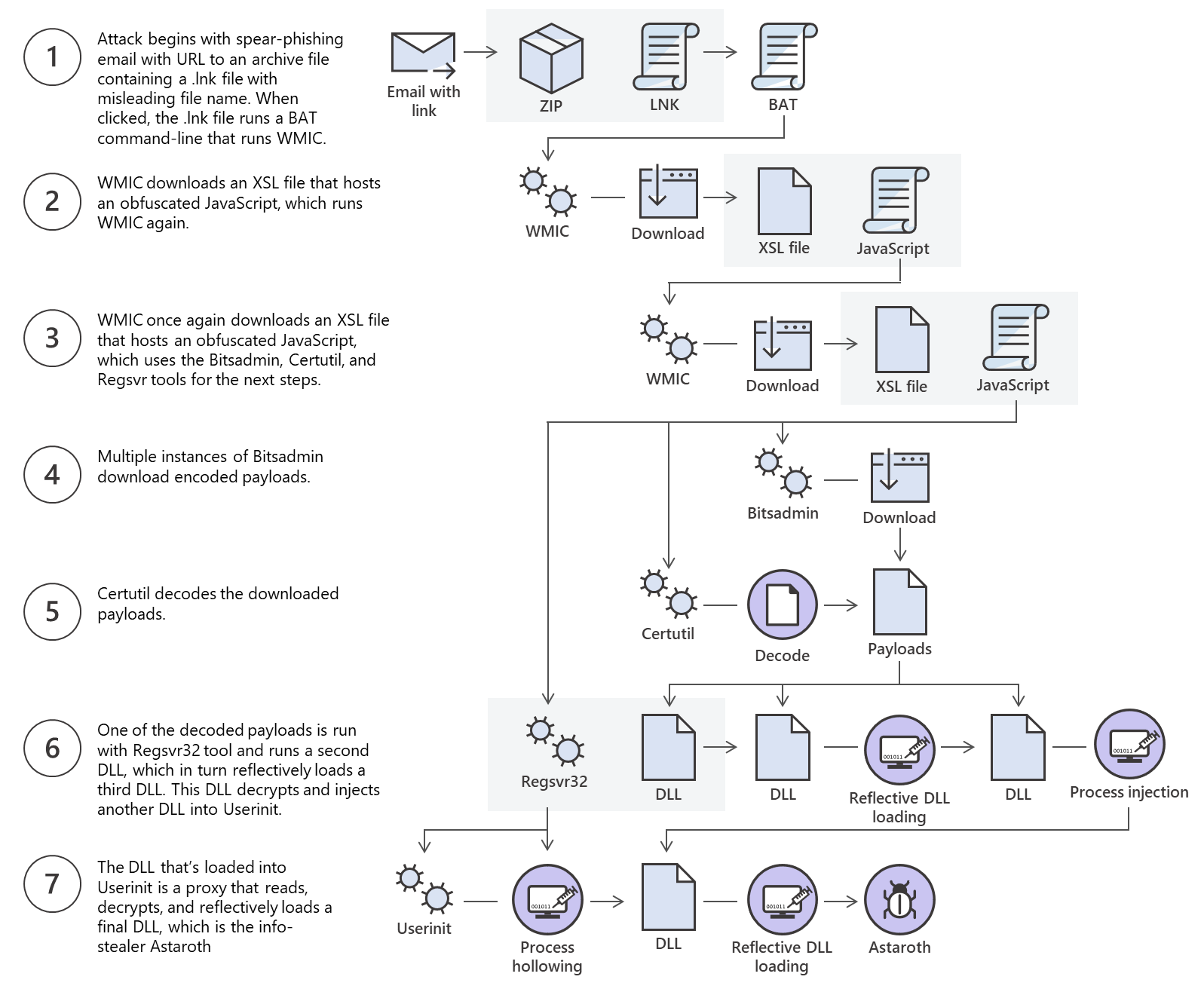
Although many Windows 10 users have an anti malware or antivirus software, the fileless technique makes the malware harder to detect. Here’s the OPs scheme on how the attack works:
A very interesting thing is that no files, except system tools, are involved in the attack process. This technique is called living off the land and it’s usually used to easily backdoor traditional antivirus solutions.
How can I protect my system against this attack?
First of all, make sure that your Windows 10 is up to date. Also, make sure that your Windows Defender Firewall is up and running and has the latest definition updates.
Don’t expose yourself to unnecessary risks. Find out why Windows Defender is the only malware barrier you need!
If you’re a Office 365 user, you’ll be happy to know that:
For this Astaroth campaign,Office 365Advanced Threat Protection (Office 365ATP) detects the emails with malicious links that start the infection chain.
As always, for more suggestions or questions, reach for the comments section below.
READ ALSO:








Gloss