Leveraging Web Application Vulnerabilities for Resourceful Intelligence Gathering
iSpeech
The talk seeks to provide the audience with a starting point for where and how resourceful information and intelligence can be found and collected, particularly, through discovery and exploitation of security flaws in web applications. The talk will provide real life examples of security flaws through which sensitive information could have been disclosed, and how at times - owing largely to the interconnected nature of such information - it could be pieced together with other data to glean useful intelligence about a particular individual or group. Lastly, the talk will touch upon how developers can avoid baking these issues into their services and applications, while also discussing protective operational security measures that end-users can adopt as a best practice.
Talk overview:
Introduction:
Intelligence and Investigations
Case Studies
Web Application Vulnerabilities and Intelligence Gathering
Scoping and Execution:
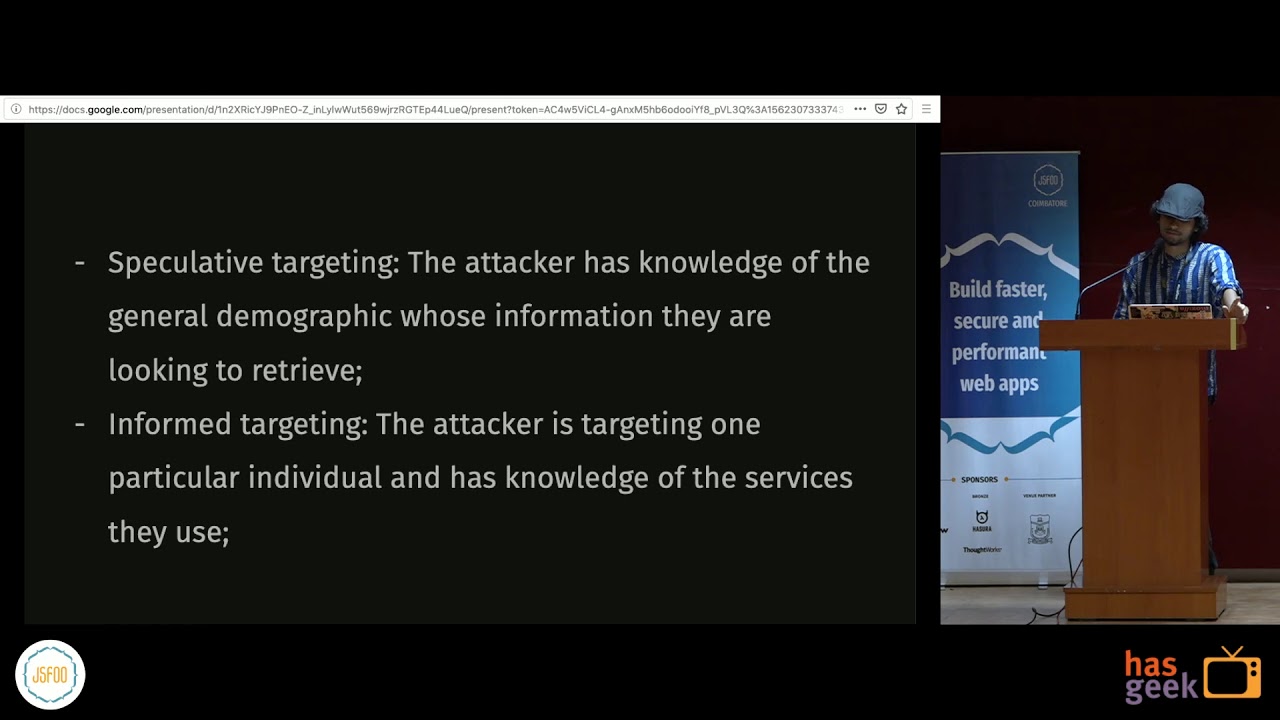
Targeting Techniques
Types of Prevalent Flaws
Attacking Techniques
Slides with Examples
Defense:
Best Practices for Developers
Operational Security for Users
source







Gloss