Hackers Can Manipulate Media Files Transferred via WhatsApp, Telegram
Hackers can manipulate media files transferred by users through the WhatsApp and Telegram messaging applications due to the way the Android operating system allows apps to access files in external storage, Symantec warned on Monday.
Android applications can store files and data on a device’s internal storage or external storage. Files in the internal storage are accessible only to their respective apps, which is why Google advises developers to use it for data that should not be accessible to the user or other apps. On the other hand, files in the external storage can be viewed and modified by the user and other apps as well.
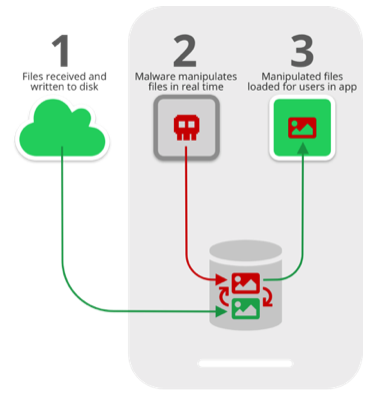
Researchers at Symantec have detailed an attack method, dubbed “Media File Jacking,” that allows a malicious Android application with “write-to-external storage” permissions to quickly modify files sent or received via WhatsApp and Telegram between the time they are written to the disk and the moment they are loaded in the app’s user interface.
The attack works against WhatsApp in its default configuration and against Telegram if the user has enabled the “Save to gallery” option.

Researchers showed how a malicious app could manipulate images, invoices and audio files by running in the background and monitoring the targeted messaging app for received files. Images can be manipulated as part of a prank, but the attack could also be used for extortion, Symantec said.
Manipulating invoices can have far more serious consequences. The attacker could programmatically swap the bank account information in a file in order to trick the victim into sending money to an account they control instead of the account in the original invoice.
“The customer receives the invoice, which they were expecting to begin with, but has no knowledge that it’s been altered. By the time the trick is exposed, the money may be long gone. To make matters worse, the invoice hack could be broadly distributed in a non-targeted way, looking for any invoices to manipulate, affecting multiple victims who use IM apps like WhatsApp to conduct business,” Symantec warned.
Manipulating audio messages can also have serious consequences for an organization. In an attack scenario described by Symantec, a company’s CEO sends the CFO an audio message via WhatsApp requesting updated slides for a board meeting. The attacker uses voice reconstruction technology to replace the original audio with a message of the CEO requesting a money transfer to a bank account controlled by the attacker.
In the case of Telegram, Media File Jacking can be used to serve fake news on a trusted news organization’s official Telegram channel, Symantec said. An attacker could replace the legitimate content pushed out by the organization with false information on the victim’s device.
While Symantec has demonstrated the attack against WhatsApp and Telegram, the risks associated with external storage on Android have been known for some time. A very similar technique was described last year by Check Point researchers, who showed that a piece of malware installed on an Android device can overwrite legitimate files with specially crafted ones to cause crashes (which could also lead to code execution with elevated privileges), and hijacking an application’s update process to install more malware. Check Point called it a “man-in-the-disk” attack.
Symantec says it has reported its findings to both WhatsApp and Telegram. WhatsApp believes the problem should be addressed by Google and pointed SecurityWeek to the tech giant’s upcoming advancements in Android Q. Telegram could not be reached for comment.
Android Q will introduce a privacy feature called Scoped Storage, which changes how applications can access files on the device’s external storage. Symantec says Scoped Storage may mitigate the Media File Jacking attack, but points out that it will take some time for the changes to be enforced due to the challenges posed for application developers. Moreover, it will take some time until Android Q is widely distributed and some devices will never run the new version of the operating system.
Symantec believes the developers of applications such as WhatsApp and Telegram should take steps to prevent potential attacks by validating the integrity of files before loading them in the app, storing files in internal storage when possible, and encrypting media files similar to how text is encrypted.
Symantec has developed proof-of-concept (PoC) exploit applications to demonstrate how images and invoices could be manipulated. The company has published videos showing how attackers could manipulate these types of files, along with how voice recordings can be tampered with.
Related: WhatsApp Vulnerability Exploited to Spy on Users
Related: Zero-Day in Telegram's Windows Client Exploited for Months



 Tags:
Tags: 





Gloss