Hack the Box (HTB) machines walkthrough series — YPuffy
Today, we will be continuing with our exploration of Hack the Box (HTB) machines as seen in previous articles. This walkthrough is of an HTB machine named YPuffy.
HTB is an excellent platform that hosts machines belonging to multiple OSes. It also has some other challenges as well. Individuals have to solve the puzzle (simple enumeration plus pentest) in order to log into the platform and download the VPN pack to connect to the machines hosted on the HTB platform.
Note: Only write-ups of retired HTB machines are allowed. The machine in this article, named YPuffy, is retired.
The walkthrough
Let’s start with this machine.
1. Download the VPN pack for the individual user and use the guidelines to log into the HTB VPN.
2. The YPuffy machine IP is 10.10.10.107.
3. We will adopt the same methodology of performing penetration testing as we have previously used. Let’s start with enumeration in order to learn as much about the machine as possible.
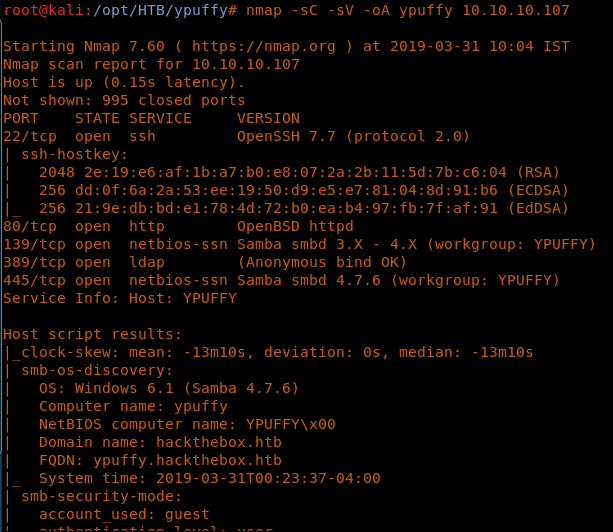
4. As usual, let’s start with the Nmap scan to gather more information about the services running on this machine. [CLICK IMAGES TO ENLARGE]
<

5. As you can see, ports 80,139, 389 and 445 are open with the initial search. Let’s target the ldap port first.
6. We’ll enumerate ldap with the utility “ldapsearch”, as below.
<

7. This extracted the following contents, including the following user (alice1978) information.

8. We’re using smbclient to connect directly, providing the hash discovered above.
<

9. Enumerating the share, we have got a private key.
10. Now we’re collecting this private key using mget to the attacking machine.
<







Gloss