Cyberthreats targeting municipalities are on the rise
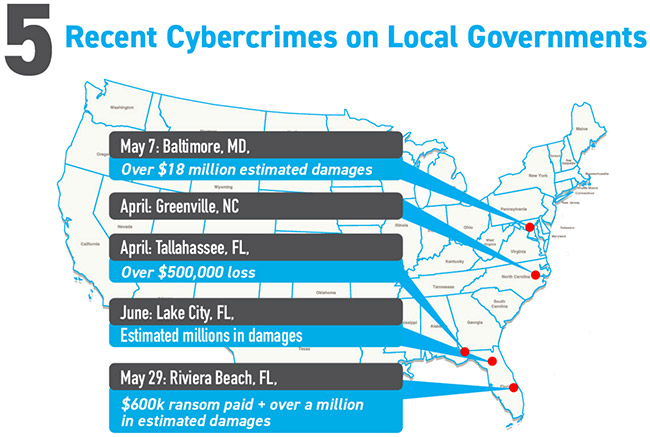
Through the first half of 2019, a growing number of municipalities across the US were hit with crippling ransomware attacks, while several large companies disclosed data breaches that exposed more than 625 million records.

A new AppRiver report also highlighted the most prevalent attacks identified by the company during the first half of the year, including chained malware attacks, Emotet, and conversation hijacking attacks.
Cities under siege
The report, based on global data compiled by AppRiver’s cybersecurity analyst team, delves into what is being considered a record year for disruptive attacks that appear to be affecting municipalities at an alarming rate.
In 2018, AppRiver analysts stated that they “expect to see more disruptive cyberattack events committed by nation states that masquerade as financially motivated attacks.”
According to the report, it is still up for debate as to who or why these attacks are being launched against local governments, but they could have widespread effects beyond financial damage. For example, malware has the potential to disrupt infrastructure, spread fear and doubt, or otherwise cause discomfort for citizens dependent on city services.
“To stay one step ahead, we must look at these attacks and question if they are more than what they seem,” said Troy Gill, senior cybersecurity analyst for AppRiver.
“Could these attacks be a dress rehearsal for larger scale, potentially more detrimental attacks? We don’t have the evidence to prove that yet, but we have to be prepared that it may well be the case either now or in the future.”
Top attacks
So far in 2019, chained malware attacks, Emotet, and conversation hijacking attacks have continued to pad cybercriminal pockets, while keeping analysts busy blocking their attempts to reach networks.
According to the report, chained malware attacks have become more prevalent this year. Profitable and successful malware attacks have been observed chaining multiple attack strategies by sharing a single foothold into a system.
As such attacks grew in popularity, Emotet, formerly classified as a bank trojan, was reclassified as a botnet early in 2019.
Emotet can spread quickly through infected devices but has recently gained the ability to scrape the past 180 days of mail from compromised accounts, including every subfolder in the client’s interpersonal message root folder.
Attackers are using this new ability to deliver malicious attachments using previous actual email conversations, a technique that unfortunately increases the perception from unknowing recipients that the message is legitimate, typically resulting in the addition of even more infected machines to the dangerous botnet.
Emotet wasn’t the only threat being seen on a large scale.
“Unfortunately, there’s also been no shortage of Conversation Hijack Attacks so far this year,” security analyst David Pickett said. “This year, encrypted ZIP files have been cyberattackers’ bread and butter.
To appear more legitimate, they frequently pivot from different iterations of the attack for maximum effectiveness. These adaptations include utilizing different languages, different passwords, different file name schemes, and verbiage.”
By the numbers
In the first six months of 2019, AppRiver quarantined:
- 4 billion spam messages
- More than 124 million emails with malware attached
- More than 20 million spear phishing attacks







Gloss