A legitimate Windows tool used for creating software packages called Advanced Installer is being abused by threat actors to drop cryptocurrency-mining malware on infected machines since at least November 2021.
"The attacker uses Advanced Installer to package other legitimate software installers, such as Adobe Illustrator, Autodesk 3ds Max, and SketchUp Pro, with malicious scripts and uses Advanced Installer's Custom Actions feature to make the software installers execute the malicious scripts," Cisco Talos researcher Chetan Raghuprasad said in a technical report.
The nature of the applications trojanized indicates that the victims likely span architecture, engineering, construction, manufacturing, and entertainment sectors. The software installers predominantly use the French language, a sign that French-speaking users are being singled out.
This campaign is strategic in that these industries rely on computers with high Graphics Processing Unit (GPU) power for their day-to-day operations, making them lucrative targets for cryptojacking.

Cisco's analysis of the DNS request data sent to the attacker's infrastructure shows that the victimology footprint spans France and Switzerland, followed by sporadic infections in the U.S., Canada, Algeria, Sweden, Germany, Tunisia, Madagascar, Singapore, and Vietnam.
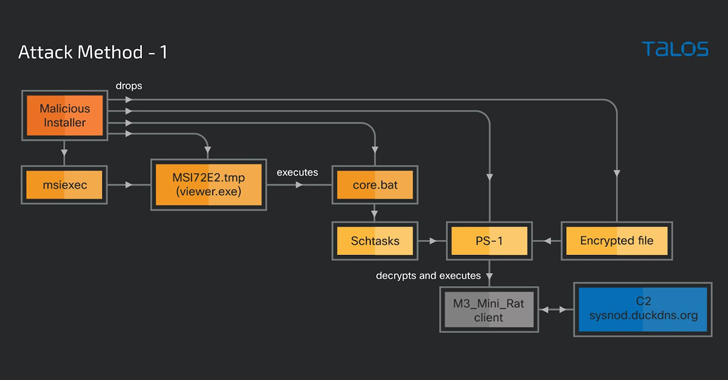
The attacks culminate in the deployment of an M3_Mini_Rat, a PowerShell script that likely acts as a backdoor to download and execute additional threats, as well as multiple cryptocurrency-mining malware families such as PhoenixMiner and lolMiner.
As for the initial access vector, it's suspected that search engine optimization (SEO) poisoning techniques may have been employed to deliver the rigged software installers to the victim's machines.

The installer, once launched, activates a multi-stage attack chain that drops the M3_Mini_Rat client stub and the miner binaries.
"M3_Mini_Rat client is a PowerShell script with remote administration capabilities that mainly focuses on performing system reconnaissance and downloading and executing other malicious binaries," Raghuprasad said.
The trojan is designed to contact a remote server, although it's currently unresponsive, making it difficult to determine the exact nature of malware that may have been distributed through this process.
Way Too Vulnerable: Uncovering the State of the Identity Attack Surface
Achieved MFA? PAM? Service account protection? Find out how well-equipped your organization truly is against identity threats
The two other malicious payloads are used to illicitly mine cryptocurrency using the machine's GPU resources. PhoenixMiner is an Ethereum cryptocurrency-mining malware, while lolMiner is an open-source mining software that can be used to mine two virtual currencies at the same time.
In yet another case of legitimate tool abuse, Check Point is warning of a new type of phishing attack that leverages Google Looker Studio to create bogus cryptocurrency phishing sites in an attempt to sidestep protections.
"Hackers are utilizing it to create fake crypto pages that are designed to steal money and credentials," security researcher Jeremy Fuchs said.
"This is a long way of saying that hackers are leveraging Google's authority. An email security service will look at all these factors and have a good deal of confidence that it is not a phishing email, and that it comes from Google."







Gloss