CompTIA Security+ Video Training by TechnologyCerts
https://www.ispeech.org
Here is the information for the Security+ Full Training Videos including info on each video. Total of 11 hours of video.
1. Mitigating Threats Part1
a. Performing Core Maintenance
b. Manage Viruses and Spyware
2. Mitigating Threats Part2
a. Secure Web Browsers
b. Identify Social Engineering Threats
3. Authentication Systems
a. Identify the Purpose of Authentication
b. Compare Hash Methods
c. Identify and Compare Authentication Systems
4. Cryptography Part1
a. Examine Symmetric Cryptography
b. Ciphers and Hash Algorithms
5. Cryptography Part2
a. Examine Asymmetric Cryptography
b. Public Key Cryptography
6. Message Security Part1
a. Secure email Services
b. Email vulnerabilities
c. SPAM
7. Message Security Part2
a. Configure Secure Messaging & Peer to Peer Communication
b. Instant Messaging Security and Vulnerabilities
c. Hosts file redirection, Intrusion Detection and Packet Sniffing
8. Access Controls
a. Use Biometric Systems
b. Establish Physical Access Security
c. Secure Peripherals and Computer Components
d. Secure Storage Devices
9. User & Role Based Security
a. Create Local Group Policies
b. Secure File and Print Resources
c. Security Templates
d. Access Control Models
10. Network Security
a. Describe Common Networking Devices
b. Consider Secure Network Design
c. Configure Internet Explorer
d. Examine the Benefits of Virtualization
11. Public Key Infrastructure
a. Examine Key Management and Certificate Lifecycles
b. Install Certificate Server
c. Enable Secure Web Communications
12. Ports & Protocols
a. Identify TCP/IP Protocols and Network Services
b. Examine IPv4 and IPv6
c. CIDR & NAT
d. Mitigate Protocol-based Attacks
13. Audit Logging & Monitoring
a. Log Server and Application Data
b. Monitor Systems and Applications
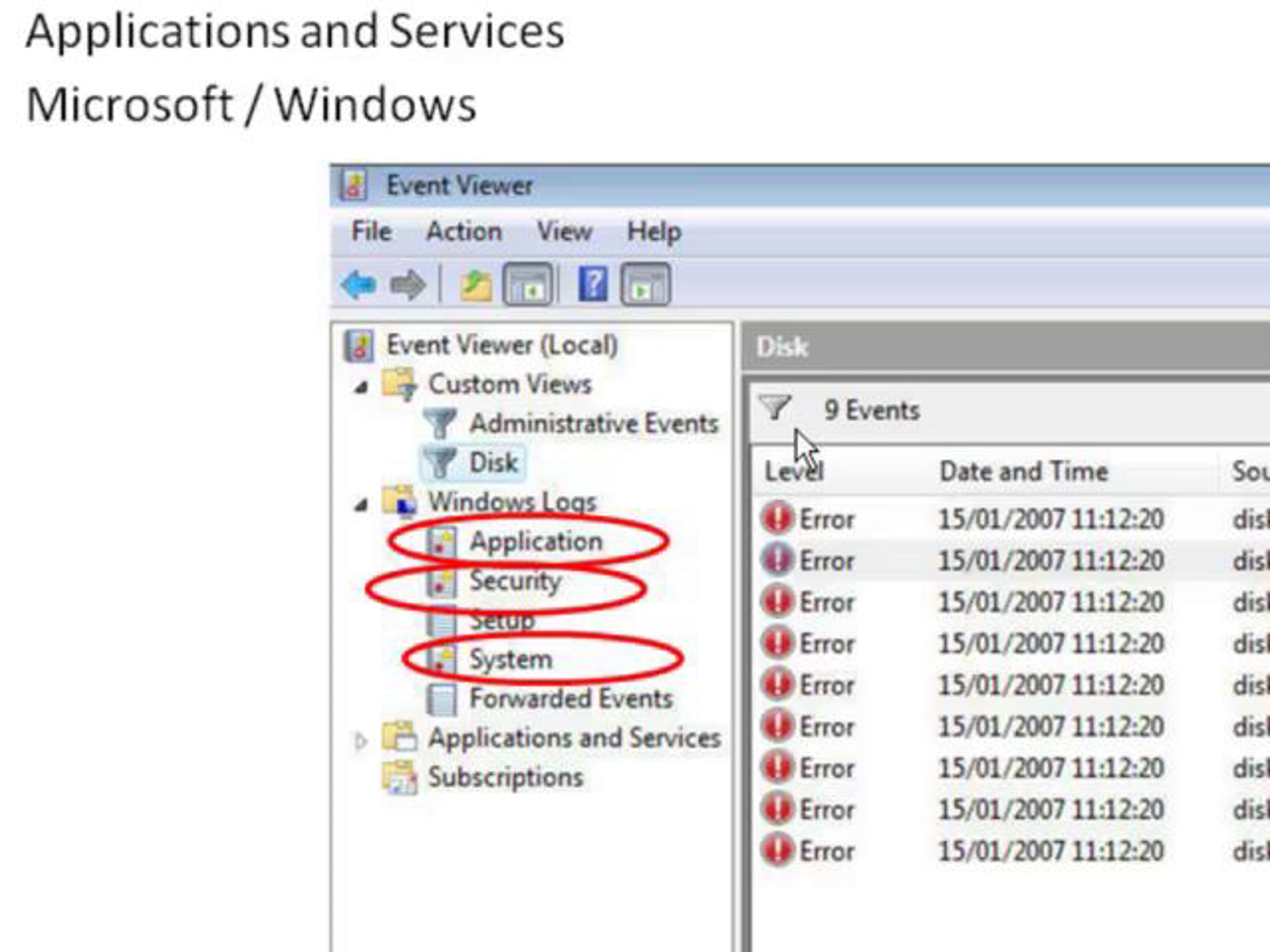
c. Event Viewer
d. Performance Monitors, Counters and Objects
14. Organizational Security
a. Create Organizational Policies
b. Identify Educational and Training Needs
c. Proper Disposal or Destruction of IT Equipment
d. Password Management
15. Remote Access Security
a. Compare RADIUS, TACACS, 802.1x Authentication Systems
b. Examine VPN Technologies and Tunneling Protocols
16. Wireless Security
a. Configure a Wireless Router for Security
b. Configure Mobile Devices for Security
17. Vulnerability Testing
a. Conduct Risk Assessments and Scan for Vulnerabilities
b. Compare HIDS and NIDS and Install an NIDS
c. Investigate the Computer Forensics Process
18. Business Continuity
a. Create a Redundancy Plan and Prepare for Natural Disasters
b. Create and Store Backups / Backup Methods
c. Fault Tolerant Systems / RAID
d. Explain the Importance of Environmental Controls
Likes: 0
Viewed:
source







Gloss