ComboJack malware steal your cryptocurrency wallet through the clipboard
iSpeech
Palo Alto Networks’ Unit 42 threat research team recently discovered a new type of malware named “ComboJack” that detects when a target victim copied a cryptocurrency wallet address to the Windows clipboard and replaced this address with Steal money for the wallet address held by its developer.
In June 2017, the CryptoShuffler discovered by Kaspersky Lab became the first malicious software to use this strategy, and at the time successfully obtained Bitcoin worth at least $150,000. The biggest difference between ComboJack and CryptoShuffler is that ComboJack supports multiple cryptocurrencies, not just Bitcoin.
According to Unit 42, the cryptocurrencies targeted by ComboJack include Litecoin, Monero, and Ethereum in addition to Bitcoin. In addition, it also targets some popular digital payment systems such as Qiwi, Yandex.Money and WebMoney.
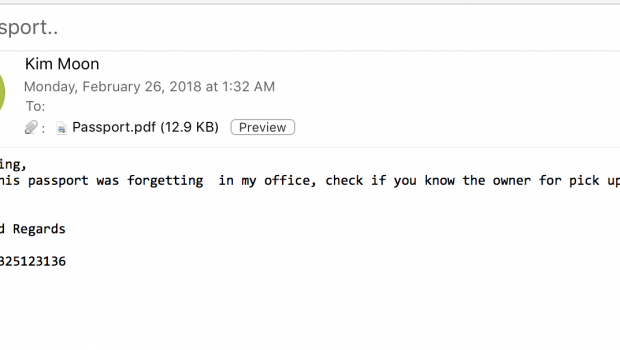
Unit 42 said that they discovered the malware early last week and it appeared together in a phishing campaign against computer users in Japan and the United States. The phishing email was titled “Lost Passport”. The attachment contained a PDF file called a passport scan.

Similar to the technique used by Dridex (Bank Trojan) and Locky (ransomware), this PDF file contains an embedded RTF file containing an embedded remote object (an HTA file) that attempts to exploit the DirectX vulnerability (CVE-2017 -8579 ).

Upon successful use, the HTA file runs a series of PowerShell commands to download and execute a self-extracting file (SFX). Of course, the entire infection chain did not end here. This SFX file will later download and run another password-protected SFX file, and finally the final payload ComboJack installation.
After the installation is complete, the ComboJack will enter an infinite loop of command execution mode. It is configured to scan the Windows clipboard every 0.5 seconds to confirm if the victim copied the wallet address. Once confirmed, it will replace this address with a hard-coded wallet address, which will allow the victim to send money to the wallet address held by the ComboJack developer without verifying the correctness of the wallet address.
[adsense size='1' ]
Perhaps you would think that this “stealing” strategy that relies on the victim not checking the correctness of the wallet’s address before completing the transaction would appear “serious.” However, in fact, few people will manually enter the wallet address during the cryptocurrency transaction, let alone perform character-by-character verification of the wallet address.
We all know that cryptocurrency wallet addresses are often a long list of numbers and characters. Whether it is manual input or character-by-character verification, it is cumbersome, and copying and pasting become the most commonly used method for cryptocurrency holders in daily transactions.
This is why malware like ComboJack or CryptoShuffler can simply use the clipboard to launch an effective attack. With the increasing popularity of cryptocurrencies and rising prices, we have reason to believe that such malware must be more threatening in the future.
Source, Image: paloaltonetworks







Gloss