Bitdefender GravityZone Ultra Product Review
Summary
Bitdefender’s GravityZone Ultra is a full-feature,
single agent console, SaaS endpoint protection solution. With more than 30
protection technologies, it effectively enables enterprises to protect their
assets and respond to threats even with limited resources and technical skills.
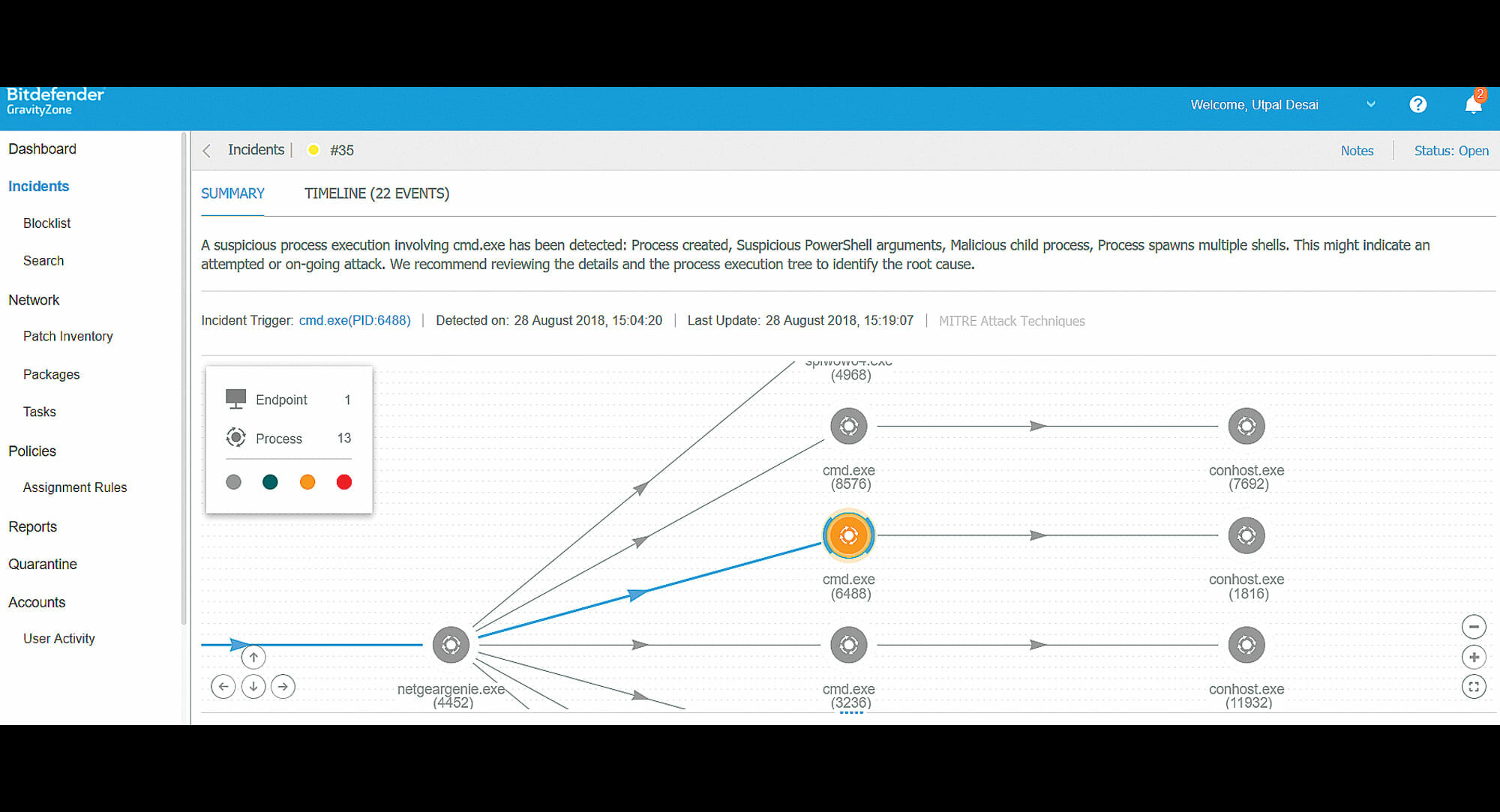
GravityZone was built from the ground up as a unified
solution, meaning Bitdefender built protection, detection and response into a
single agent that can be managed from a single console. Next-gen prevention
layers successfully limit the number of incidents requiring attention.Advanced
Threat Control constantly monitors processes, recognizing a change in process
as malwre, then taking action to remediate. GravityZone is fine-tuned to
monitor more than 300 behaviors, greatly minimizing false positives.
Hyper Detect is a tunable machine learning technology that
can enhance pre-execution and execution technologies, particularly important in
addressing advanced or targeted attacks. It will look at certain binaries more
aggressively using the predictive nature of machine learning to determine
whether something is malicious. We recommend leaving this feature in
report-only mode for a few weeks to determine that it is accurately flagging
problems. Once desired outcomes are reached, a shift from report-only to deny
or block mode will reduce false-positives.
If pre-execution layers
can’t determine that a binary is malicious with absolute confidence, it will be
sent to a cloud-based sandbox where a verdict on its maliciousness will be
rendered. The file is inaccessible until this determination has been made.
Security teams can disable and run this feature in monitor mode so objects will
still be accessible to the user.
Numerous types of pre-defined, highly developed reporting
capabilities can be exported as a PDF and CSV. A template included for security
audit purposes displays all blocked items in a single-pane dashboard.
The installers are
created from the portal, and once we figured out how to create a deployment
package, we were able to download the installation package onto test nodes. But
we ran into trouble with the actual installation process. Some of the machines
claimed they were installed, but didn’t show up on the dashboard, even after
running the installer several times and initiating multiple restarts. Following
testing, however, detected files were listed in the dashboard which has a clean
look, customizable widgets and easy to group assets.
We attempted to restore a file from the porttal’s
quarantine section and got stuck at “Pending Restore.” Drilling deeper into
quarantined files felt clunky, and we couldn’t figure out how to conduct an
investigation based on a quarantined file. This process could be more
intuitive.
Tested by Tom Weil







Gloss