TrueCrypt is Secure ; First Phase of TrueCrypt Audit Turns Up No Backdoors
TrueCrypt is a free, open-source and cross-platform encryption program available for Windows, OSX and Linux that can be used to encrypt individual folders or encrypt entire hard drive partitions including the system partition.
The program is also capable to do some amazing things, such as can create a hidden operating system on a computer, essentially an OS within an OS where users can keep their most secret files.
[adsense size='1']
TrueCrypt developers are anonymous and used the aliases “ennead” and “syncon”, perhaps to avoid unwelcome attention from their own governments. But when we talk about Privacy and Security, we can't trust anyone, especially when someone like NSA is out there.This is a major reason that security community has took an initiative to perform a public Security Audit of TrueCrypt in response to the concerns that National Security Agency (NSA) may have tampered with it.
iSec Research Lab was contracted to carry out public cryptanalysis and security audit of TrueCrypt by the cryptography community, Open Crypto Audit Project (OCAP) and they has found “no evidence of backdoors or otherwise intentionally malicious code in the assessed areas.”
[adsense size='1']
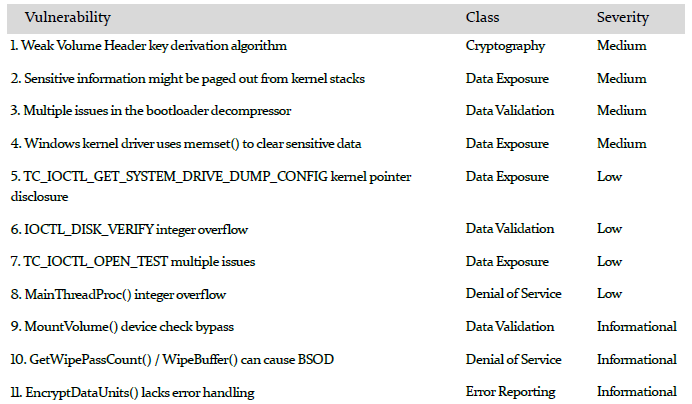
Auditors review more than 70,000 lines of TrueCrypt source code and architecture. Finally yesterday they have turned up 11 vulnerabilities in the full disk and file encryption software's source code, but no "high-severity" issues, which means nothing particularly found inappropriate and certainly nothing looks like a backdoor or intentional flaws.
According to the researchers, none of the vulnerabilities seems as an intentional flaw or immediate exploitation vectors, rather all of the identified findings appeared to be accidental.
“Overall, iSEC does think changes can be made to improve code quality and maintainability, and that the build process should be updated to rely on recent tools with trustworthy provenance. In sum, while TrueCrypt does not have the most polished programming style, there is nothing immediately dangerous to report,” reads the audit report [PDF released on April 14].
These results are from the first phase of the audit, focused on the TrueCrypt bootloader and Windows kernel driver; architecture and code review.
These results are from the first phase of the audit, focused on the TrueCrypt bootloader and Windows kernel driver; architecture and code review.
[adsense size='1']
Now, TrueCrypt is about to get a second phase exam that may hopefully give the software a clean bill of health too, because the project to audit TrueCrypt has raised tens of thousands of dollars to peer into TrueCrypt's deepest recesses. Second Phase test will include a thorough analysis of the various encryption cipher suites and implementation of random number generators and critical key algorithms.








Gloss