More than a million Android devices infected with Sophisticated bootkit trojan
Oldboot is a piece of Android malware that's designed to re-infect Mobile devices even after a thorough cleanup. It resides in the memory of infected devices; It modify the devices’ boot partition and booting script file to launch system service and extract malicious application during the early stage of system’s booting.
[adsense size='1']
Yet another alarming report about Oldboot malware has been released by the Chinese Security Researchers from '360 Mobile Security'. They have discovered a new variant of the Oldboot family, dubbed as 'Oldboot.B', designed exactly as Oldboot.A, but new variant has advance stealth techniques. Especially, the defense against with antivirus software, malware analyzer, and automatic analysis tools. "The Oldboot Trojan family is the most significant demonstration of this trend." researchers said.
Oldboot.B, Android Bootkit malware has following abilities:
- It can install malicious apps silently in the background.
- It can inject malicious modules into system process.
- Prevent malware apps from uninstalling.
- Oldboot.B can modify the browser's homepage.
- It has ability to uninstall or disable installed Mobile Antivirus softwares.
INFECTION & INSTALLING MORE MALWARE APPS
Once an Android device is infected by Oldboot.B trojan, it will listen to the socket continuously and receive and execute commands received from the attacker's command-and-control server.
[adsense size='1']
Malware has some hidden ELF binaries, that includes steganographically encrypted strings, executable codes and configuration file downloaded from C&C server, located at az.o65.org (IP is 61.160.248.67).
After installation, Oldboot Trojan install lots of other malicious android applications or games in the infected device, which are not manually installed by the user.
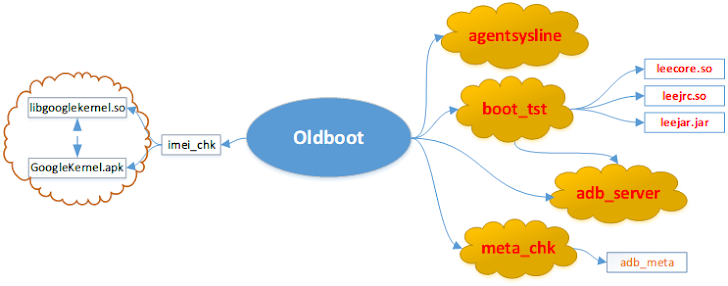
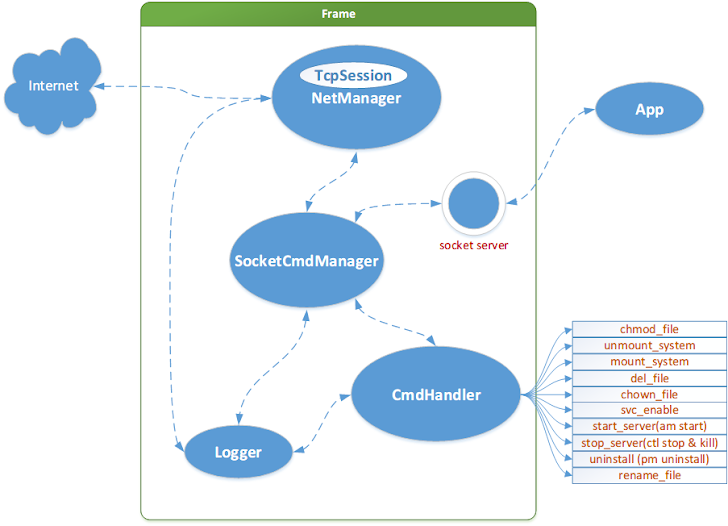
MALWARE ARCHITECTURE
Oldboot.B architecture includes four major Components, those automatically executes during the system startup by registering itself as a service in the init.rc script:
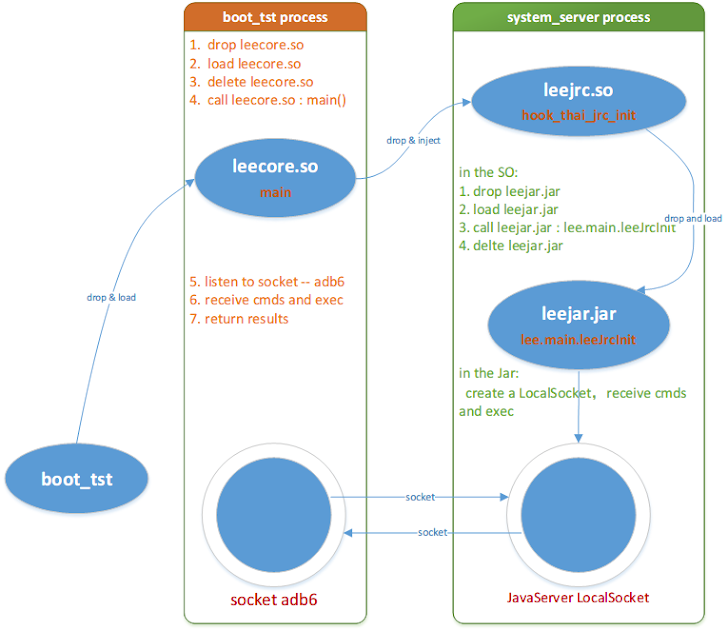
1) boot_tst - uses remote injection technique to inject an SO file and a JAR file to the 'system_server' process of the Android system, continuously listen to the socket, and execute commands sent.
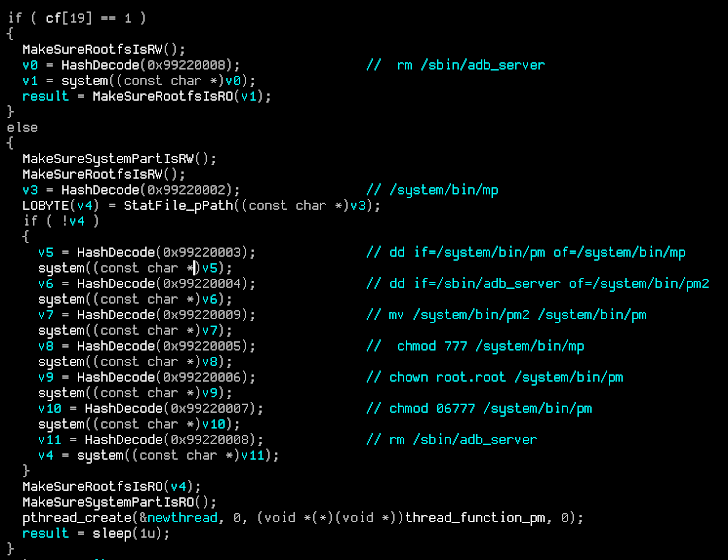
2) adb_server - replaces pm script of Android system with itself and used for anti-uninstallation functionality.
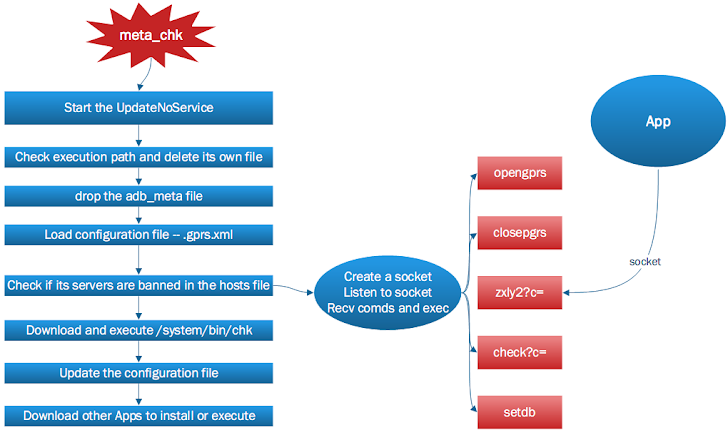
3) meta_chk - update the configuration file, download and install Android Apps promoted in the background. The Configuration file is encrypted, that greatly increases the time required to analyze.
[adsense size='1']
To evade detection, meta_chk destroys itself from the file system, and left with only the injected process. Android Antivirus software does not support the process memory scan in the Android platform, so they cannot detect or delete the Oldboot Trojan which resides in the memory.
4) agentsysline - module written in C++ programming language, run as a daemon in the background to receive commands from command-and-control server. This component can uninstall anti-virus software, delete the specific files and enable or disable network connection etc.
PROBLEMS FOR SECURITY RESEARCHERS
To increase the problem of malware analyzers:
- It add some meaningless code and trigger some behavior randomly.
- Check for SIM card availability in the device, and it will not perform certain behavior if there is no SIM card to fool sandbox or emulators.
- Check for the existence of antivirus software, and may uninstall the anti-virus software before doing anything malicious.
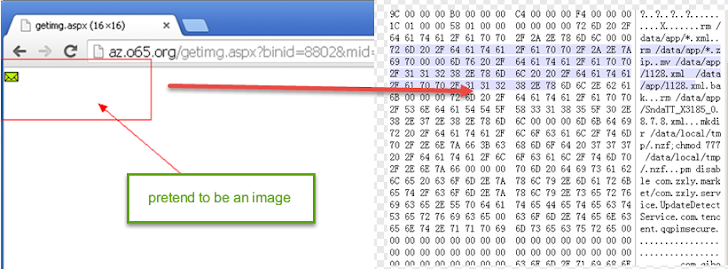
Malware uses the steganography techniques to hide its configuration file into images:
"But after some analysis, we found that the configuration of meta_chk is hidden in this picture, which contains the command will be executed by meta_chk and other information." researchers said. The size of this configuration file is 12,508 bytes.
"Depending on the commands sent from the C&C server, it can do many different things, such as sending fake SMS messages or phishing attacks, and so on. Driven by profit, the Oldboot Trojan family changes very fast to react to any situation."
[adsense size='2']
Oldboot.B is one of the most advanced Android malware that is very difficult to remove, but antivirus firm 360 Mobile Security also released Oldboot detection and removing tool for free, you can download it from their website.
To avoid infection, Smartphones users should only install apps from trusted stores; make sure the Android system setting 'Unknown sources' is unchecked to prevent dropped or drive-by-download app installs; don't use custom ROMs and install a mobile security app.








Gloss