Viber Security Vulnerabilities: Images, Doodles, Location and Videos sent over Viber is unencrypted
iSpeech
http://www.unhcfreg.com
http://cyberforensics.newhaven.edu
Interested in studying with us? http://www.newhaven.edu/engineering/get-information-about-computer-science-programs/
University of New Haven Cyber Forensics Research and Education Group Researchers, CT, USA find Serious Security Flaws in Viber
Vulnerability/Bug: Images, Doodles, Location and Videos sent over Viber is unencrypted
Posted by: Ibrahim Baggili (PhD), Jason Moore
Introduction
We recently discovered a serious security flaw in the way Viber receives Images, Doodles, Video files as well as the way it sends or receives location data. We also see potential issues in the way Viber stores data in an unencrypted format on their servers with no authentication mechanism for them to be retrieved from a client.
The main issue is that the above-mentioned data is unencrypted, leaving it open for interception through either a Rogue AP, or any man-in-the middle attacks. In the spirit of keeping the world a safer place, we felt that it is best to send this bug/vulnerability to the Viber team first, and then publishing our work. We notified Viber, but we have failed to receive a response from them. It is important to let the people know of these vulnerabilities, therefore, we chose to publish these results and the video in this post.
Finally, we would like to add that our team really values Viber as an application and we think it's a great communication tool, and we hope that these vulnerabilities will be fixed in Viber's next release.
Apparatus
HTC One (Android version 4.4.2)
Samsung Galaxy S4 (Android version 4.3)
Viber version 4.3.0.712
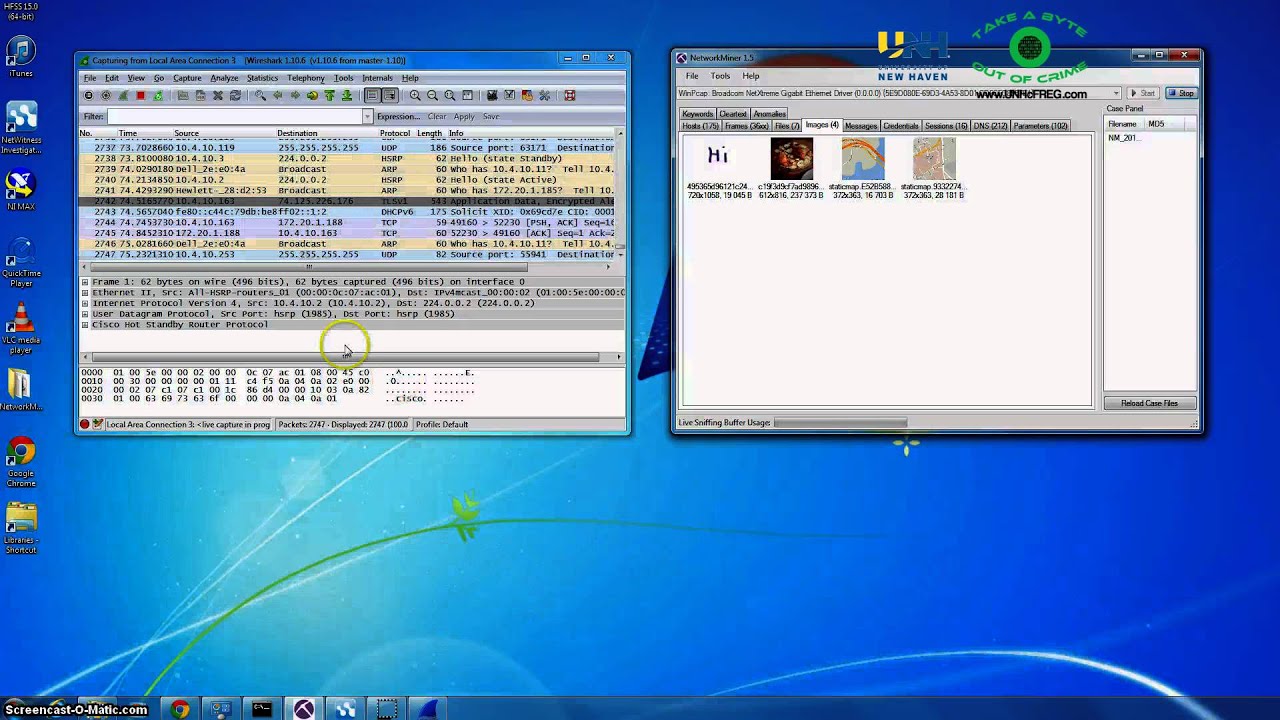
Network Forensics Experimental Setup
The mobile traffic was captured using the Windows 7 virtual wifi miniport adapter feature. The host computer was connected to the Internet via an Ethernet cable so that the wireless card was not in use. The Ethernet connection was set to share its Internet access with the virtual wifi miniport adapter - this information can be found in our WhatsApp video post if you click HERE.
We were now able to capture the traffic over the network test using various tools such as NetworkMiner, Wireshark, and NetWitness.
Results Summary
Images received are unencrypted
Doodles received are unencrypted
Videos received are unencrypted
Location images sent and received are unencrypted
Data is stored on the Viber Amazon Servers in an unencrypted format
Data stored on the Viber Amazon Servers is not deleted immediately
Data stored on the Viber Amazon Servers can be easily accessed without any authentication mechanism (Simply visiting the intercepted link on a web browser gives us complete access to the data)
Ramifications
Anyone, including the service providers will be able to collect this information -- and anyone that sets up a Rogue AP, or any man-in-the middle attacks such as ARP poisoning will be able to capture this unencrypted traffic and view the images and videos received as well as the locations being sent or received by a phone.
Solutions
Make sure the data is encrypted over a tunnel when it is sent. Also make sure the data is encrypted properly when saved, and authenticated when being accessed.
2014-04-23 04:10:50
source







Gloss