US utilities prepare for heightened cybersecurity risk from Russia
While the U.S. power grid is well-prepared to withstand potential cyberattacks, key vulnerabilities persist that could catch utilities off-guard if Russia retaliates against the economic sanctions that were imposed after it invaded Ukraine.
The U.S. Department of Homeland Security's Cybersecurity & Infrastructure Security Agency issued a "Shields Up" alert Feb. 12 in response to the growing Russian threat, indicating that "every organization in the United States is at risk from cyber threats that can disrupt essential services and potentially result in impacts to public safety." The alert said organizations should be ready to detect unusual network behavior as well as make sure all software is up to date and that all remote access requests are validated with multifactor authentication.
North American Electric Reliability Corp. said in a Feb. 28 statement that its "suite of Critical Infrastructure Protection Reliability Standards" is ready to address those additional security challenges. Scott Aaronson, senior vice president for security and preparedness at the Edison Electric Institute, the trade group for investor-owned utilities, wrote in an email that "member companies are closely monitoring the situation and are coordinating across the industry and with our government partners."
Berkshire Hathaway Energy, which partnered with Xcel Energy Inc., the U.S. Energy Department and the National Renewable Energy Lab to launch the Clean Energy Cybersecurity Accelerator, emphasized in an email that cybersecurity threats to critical infrastructure are "not new," and the power provider is "prepared to adapt our measures as new threat information emerges to protect our assets and keep our customers and employees safe and secure."
Security exercises
NERC's sixth grid security exercise in November 2021, dubbed GridEx VI, highlighted the electric utility industry's increasing exposure to risk through factors like its deep dependence on natural gas. Due partly to the Biden administration's persistence, gas utilities like Northwest Natural Holding Co. are looking to invest tens of millions of dollars in cybersecurity upgrades.
"This administration has been extremely active in getting the word out to U.S. critical infrastructure and ... getting helpful information disseminated so they can understand what indicators of compromise they ought to be looking for," Lisa Sotto, who leads the global cybersecurity practice at law firm Hunton Andrews Kurth LLP, said in an interview.
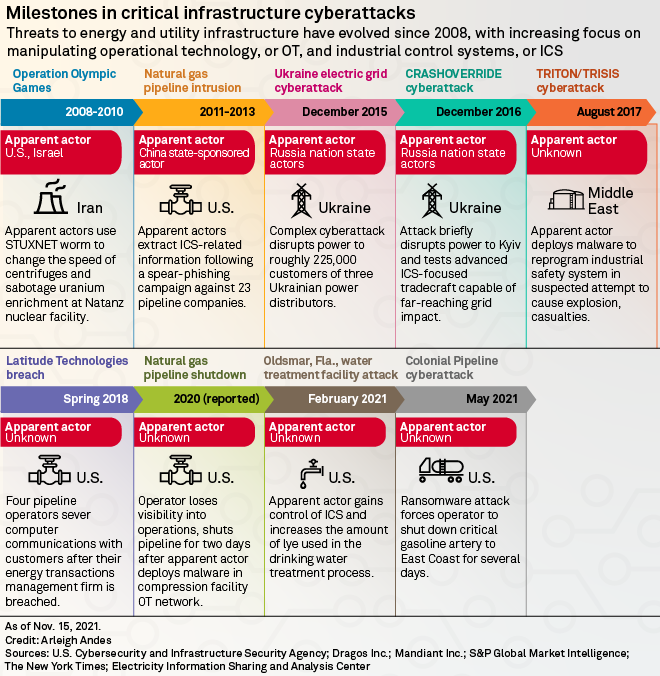
In April 2021, the DOE launched a 100-day plan to advance technologies and systems considered key to modernizing the electricity sector's cybersecurity defenses. Cybersecurity vulnerabilities exposed by the May 2021 attack on Colonial Pipeline Co., which transports petroleum products, have also spurred a new push on the critical infrastructure side.
"I think we've come a very long way," Sotto continued. "That's not to say that anything is bulletproof."
As the number of smaller renewable energy assets connecting to the grid ramps up around the world, potential entry points for hackers can significantly increase, according to Johan Vermij, a research analyst at 451 Research who specializes in the internet of things.
"Large utilities usually have a pretty good view on security, but across the globe, new utilities are emerging such as wind farm and solar park operators that are active in a highly competitive market with slim margins, and these may well be too small to have their security up to standard," Vermij said in an email. "These may be the largest risk to grid stability."
Russia also has cyberwar experience when it comes to shutting down critical infrastructure, Vermij added. Cyber experts think Russia was behind power outages in Ukraine in 2015 and a cyberattack on Georgia that preceded a Russian military invasion in 2008.
Operational technology exposure
While the power sector has made strides in information security by complying with standards set by the International Standardization Organization, Vermij said, the hardware and software that control infrastructure are only just beginning to catch up.
Operational technology, or OT, assets are managed through industrial control systems that feed information to control rooms where operators send commands to the equipment, known as control changes. Much of the OT asset base went into service decades ago and was not designed to continuously monitor for threats or accommodate other modern cybersecurity practices.
Several short-term measures are available to power providers if they remain exposed on the OT side, Nicholas Friedman, national managing partner and governance, risk and compliance strategist at Templar Shield Inc., said in an interview.
First, any companies not already doing so should subscribe to a threat intelligence service.
"It tells companies what types of attacks are happening, when they're happening and how," Friedman said. "It's a way for people to see around the corner ... that's one of the best things companies can do."
Additionally, power companies can purchase OT listen-only devices for control change authorization checks and prioritize employee training to combat phishing attempts like the one that likely infiltrated Colonial Pipeline, Friedman said.
S&P Global Commodity Insights produces content for distribution on S&P Capital IQ Pro. 451 Research is part of S&P Global Market Intelligence.







Gloss