Trap a Spam-Bot for Fun and Profit
https://www.ispeech.org
At DeepSec 2014 Attila Marosi (Sophos Lab) held a presentation about the use of honeypot systems in anti-spam and anti-virus research:
"The most of honeypot systems pretend that they are vulnerable or badly confirured systems in other to gather information about unkonwn attackers and the techniques they using during the attacks. In my research, I chaged this approach a little bit.
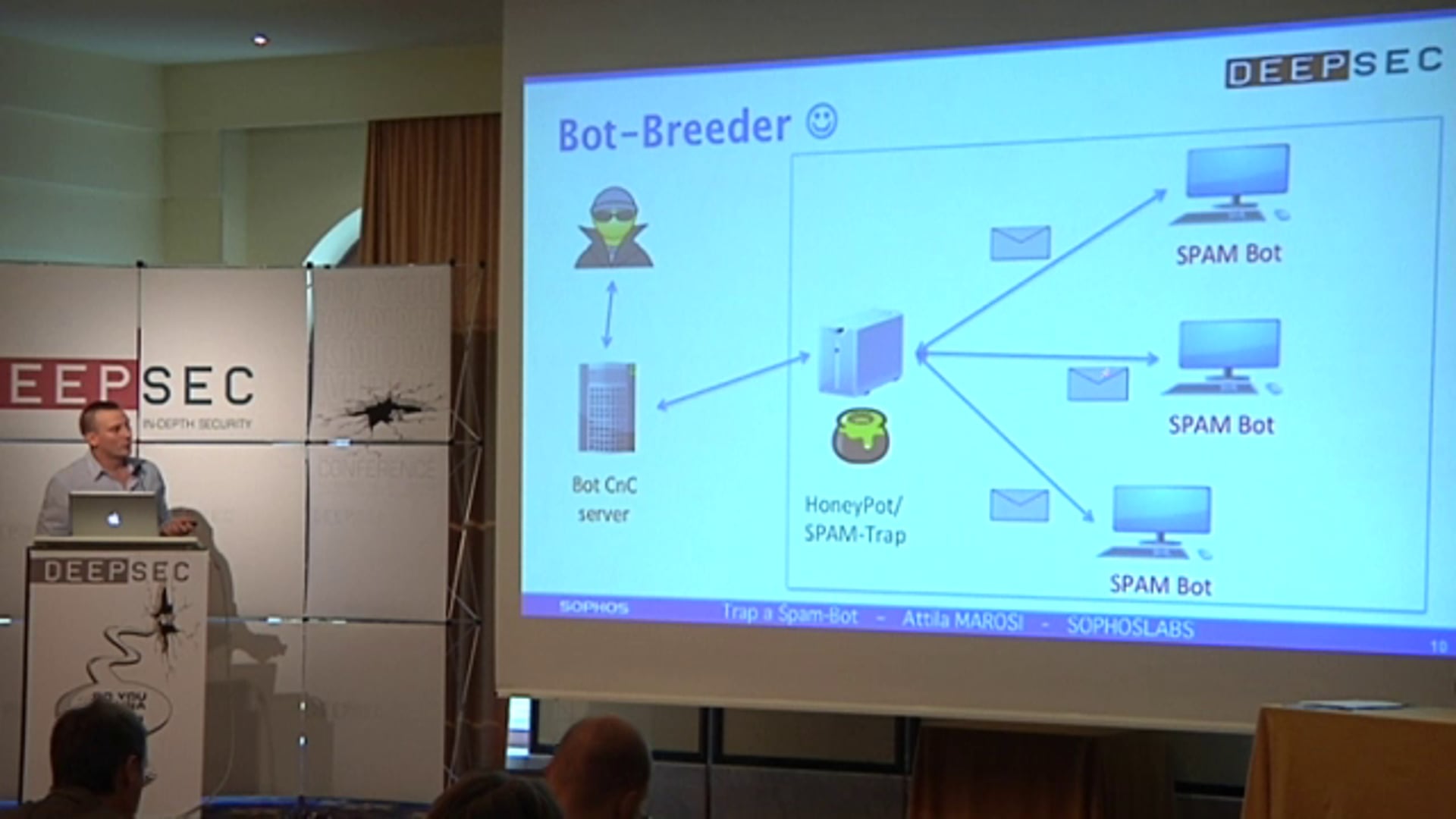
In my lecture I will share the result of my research which is about how to trap a botnet variant to collect valuable information directly for the bad guys. It is a kind of honeypot where the malware is allowed to run in a dedicate and carefully separated network (network sandboxing) to do its dirty job. The infected machine can communicate with the Command and Control (C&C) servers but the other network connections are absolutely just simulated. As a result of this “cheat”: the C&C servers and the bot think they have the ability to spread the spam emails. In real, all the messages, and any other network actions, are just emulated (not threaten the world) and the only result of their activities is that we will have all the spams and all the malware variants they try to spread during the champagnes.
With observation and monitoring a working botnets you can gain more knowledge and information about it. We will get everythink, not just the spam samples they are trying to send but, the C&C network they are using, and you are able to collect information about other victims (tipically, infected sites) which are used by the botnets. With this intel you can easily eliminate the damage of the botnet, and you could help others in the world – if you share the information with others. ☺
Most of the cases, a spam message has a link to somewhere but these links usually points not to the destination address directly but to a legitimate and (!)infected site to make the detection harder and the reaction slower. The spammers also use URL-sorter services to hide the real destination of the link. With analysing the spam messages (extract the link, follow the destination) we can disclosure the final destination, thus we can easily collect all the victim server URLs and all the malicious sort-links. With this information we can alert the victims and we can bolck the malicious addresses as well."
source







Gloss