[Tips] Testing common weaknesses ports
iSpeech.org
On your Penetration Testing, you usually need to conduct a port scanning for identify open ports and running services. On this topic, i am guide some weaknesses ports that you should test.
What is Ports?
Ports act as logical communications endpoints for computer and are used on the Transport layer of the OSI model by protocol. There are 65,536 ports altogether, numbering between 0 and 65,535.
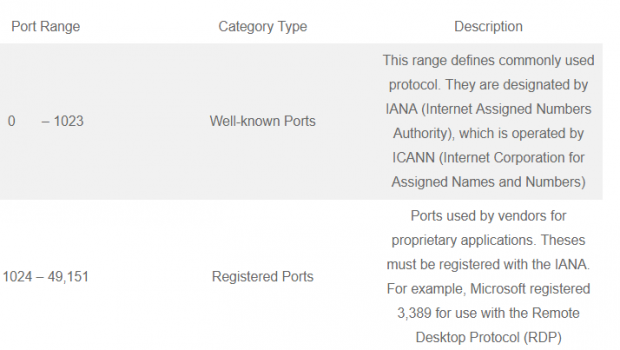
| Port Range | Category Type | Description |
| 0 – 1023 | Well-known Ports | This range defines commonly used protocol. They are designated by IANA (Internet Assigned Numbers Authority), which is operated by ICANN (Internet Corporation for Assigned Names and Numbers) |
| 1024 – 49,151 | Registered Ports | Ports used by vendors for proprietary applications. Theses must be registered with the IANA. For example, Microsoft registered 3,389 for use with the Remote Desktop Protocol (RDP) |
| 49,152 – 65,535 | Dynamic and Private Ports | These port can be used by applications but cannot be registered by vendors. |
These are two type ports:
- Inbound ports – used when another computer wants to connect to a service or application running on your computer. Servers primarily use inbound ports so that they can accept incoming connections and serve data.
- Outbound ports – used when your computer wants to connect to a service or application running on another computer. Client computers primarily use outbound ports that are assigned dynamically by the operating system.
Below is the list of common weaknesses ports
21 ftp
80 web
443 openssl
873 rsync
2601,2604 zebra
8128 squid
4440 rundeck
6082 varnish
6379 redis
8000-9000
9200 elasticsearch
11211 memcache
27017 mongodb
28017 mongodb
50070 hadoop
7001 weblogic
50000 SAP
8080 tomcat/WDCP
8888 amh/Lumanager
2222 DA
2082/2083 cpanel
3312/3311 kangle
8083 vestacp
7778 kloxo
10000 virtualmin/webmin
8089 jboss
8649 ganglia
Tips: You can scan all these ports by using Nmap:
nmap -sT -sV -p 21,80,443,873,2601,2604,3128,4440,6082,6379,8000,8008,8080,8081,8090,8099,8088,8888,9000,9090,9200,11211,27017,28017 –max-hostgroup 10 –max-parallelism 10 –max-rtt-timeout 1000ms –host-timeout 800s –max-scan-delay 2000ms -iL iplist.txt -oN result/port.txt –open







Gloss