This is why you sanitize user input: Chat hacked live by XSS/HTML code injection, hilarity ensues
https://www.ispeech.org
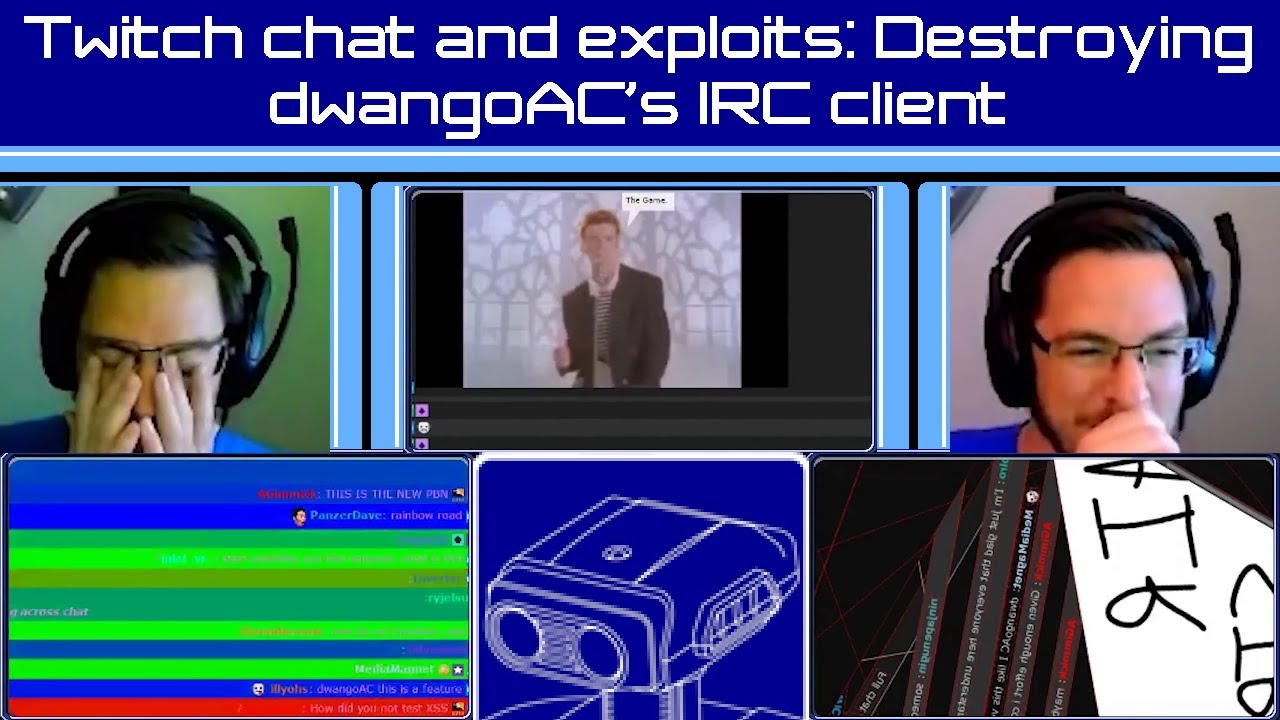
While TASBot was playing SMB3 a chat user named Hexxyr found an unsanitized input vulnerability allowing HTML and CSS to be injected in timeshifter's prototype alpha release filtered Twitch chat software that I (dwangoAC) recently started using to display chat inside OBS. What happened next was a live impromptu demonstration of my chat audience discovering new ways to take advantage of the exploit and a perfect example of why you should always sanitize user input to prevent raw HTML tags from being passed through.
It should be noted that allowing chat to continue to test the limits was inherently risky. A number of somewhat bad things *did* happen, but with only minimal consequences. The chat display tool only needs to know what Twitch channel to connect to (dwangoAC in this case) and did not have an auth token so there was no risk of that being stolen. Still, there were substantial risks from the perspective that chat could have displayed inappropriate images or otherwise could have caused far more damage than they did. While what happened here was hilarious I can almost guarantee that it will not be as funny for you if you ever make the same mistake and allow input which has not been sanitized in your own application.
This specific video is the complete and uncut hilarity of what happened when Twitch Chat figured out how to hack the living daylights out of the chat display tool I use. Twitch chat broke a number of things including mangling my microphone's audio pitch and turning me into "deepwango" by creating a mismatch between 44.1 kHz and 48 kHz audio. I even got rickrolled all through the power of raw HTML tags and CSS! The massive breakage ended up being insanely hilarious. In the strictest sense you could say it wasn't technically XSS (Cross-Site Scripting) because there was no second site, only unsanitized user input parsed as code. The chat text that was being displayed simply had raw tags embedded that were then rendered by the browser.
Credit for the discovery of the exploit goes to @VixusFoxy (Twitter, https://hackerone.com/vixus) who also goes by the name Hexxyr in Twitch chat as I spoke it in the video. The source code for the chat client including the HTML sanitization fix made by timeshifter toward the end of the video can be found at: https://github.com/timeshifter/twitch-filtered-chat
If you have no idea who TASBot is, he's a game-smashing robot that plays back Tool-Assisted Speedruns on real consoles and often does his own fair share of glitching. He's appeared at a number of Games Done Quick charity marathons and in this particular video he was attempting to play Super Mario Bros. 3. I, dwangoAC, am his keeper and as Ambassador on staff at TASVideos I attempt to console verify existing TAS runs that were originally made in an emulator.
Discord - http://Discord.TASBot.net
Live stream - http://twitch.tv/dwangoAC
TASBot home - http://TASBot.net
More TAS's - http://TASVideos.org
All TASVideos.org content used with permission under Creative Commons Attribution 2.0.
2018-11-09 23:02:07
source







Gloss