The Tick: a Persistent Stealth Firmware Rootkit
TTS
The Tick is a persistent firmware rootkit; it evades detection by forging one or more TPM PCRs.
Demonstrated as part of "BIOS Chronomancy: Fixing the Core Root of Trust for Measurement", presented at Black Hat Las Vegas 2013
Narrative: (for those watching offline)
- Shows how a stealth rootkit can evade detection by forging PCR0
- Bootup of a healthy E6400 laptop, with stock BIOS.
- Notice the original Dell splash screen. The module that contains this splash screen is measured by the SRTM and thus will trigger a change in PCR0 if it is modified.
Log in:
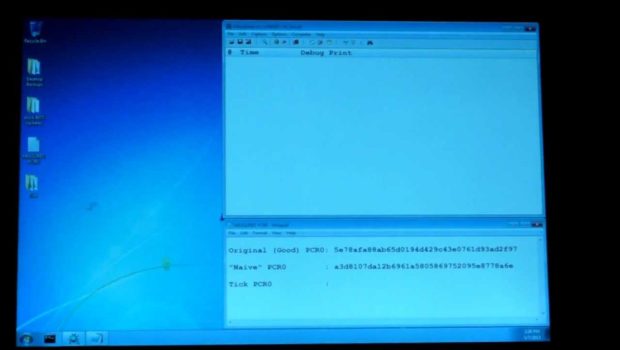
- Top right of screen will display our OpenTPM kernel driver debug output
- Bottom right text file will contain our read PCR0 hashes
- Run OpenTPM driver to read PCRs, save original (good) PCR0 in text file
- Install a custom BIOS containing a "naïve" firmware rootkit which will be easily detected by observing PCR0
- The splash screen has been modified, has no stealth capability
- Log in, dump PCRs, new PCR0 does not match good PCR0, record non-matching hash showing that the BIOS modification has been easily detected.
- Install a custom BIOS containing a "Tick" firmware rootkit
- Same as the naive rootkit, the Tick also mods the splash screen, does have stealth capability
- Log in, dump PCRs, new PCR0 does match PCR0.
- Tick is now free to modify any other portion of the firmware without ever being detected, even to insert itself into SMRAM. 😉
The Tick ascii art is from "
source







Gloss