June 7th, 2020 | 🕒
Free Text to Speech Click Here : https://autodownload01.blogspot.co.uk/?book=1138557110Single Case Research Methodology, 3rd Edition presents a thorough, technically sound, user-friendly, and
March 23rd, 2020 | 🕒
Powered by iSpeech Attacking the Cluster Remotely In our previous blog post “Kubernetes Pentest Methodology Part 1”, we wrote about
March 10th, 2020 | 🕒
iSpeech A Technical Deep Dive Into Insider Kubernetes Attack Vectors In part one and part two of our series on
March 2nd, 2020 | 🕒
https://www.ispeech.org Introduction Thick client applications have been around for many years and can still be found within a variety of
February 4th, 2020 | 🕒
iSpeech There have been patterns that have been found in AWS environment while exploring insecure S3 buckets, misconfiguration and compromised
January 27th, 2020 | 🕒
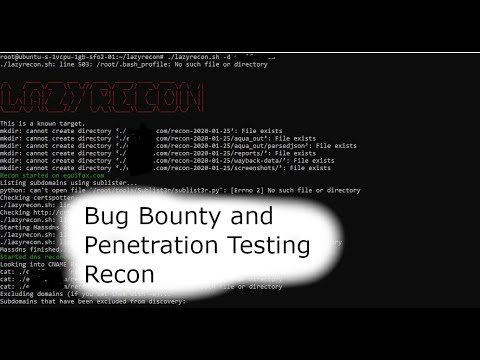
https://www.ispeech.org/text.to.speech Short Version: Links to tools: Hurricane Electric: bgp.he.net/ Masscan: https://github.com/robertdavidgraham/... Photon: https://github.com/s0md3v/Photon Webscreenshot: https://pypi.org/project/webscreenshot/ Shodan: https://shodan.io CVE Details: https://cvedetails.com/
January 26th, 2020 | 🕒
iSpeech.org Long Version: Links to tools: Hurricane Electric: bgp.he.net/ Masscan: https://github.com/robertdavidgraham/masscan Photon: https://github.com/s0md3v/Photon Webscreenshot: https://pypi.org/project/webscreenshot/ Shodan: https://shodan.io CVE Details: https://cvedetails.com/
January 24th, 2020 | 🕒
https://www.ispeech.org/text.to.speech In this video, Katie Paxton-Fear @InsiderPhD shares with me her methodology for bug bounty hunting. Full video: https://www.youtube.com/watch?v=pzv-Lu7TbFI Katie
January 24th, 2020 | 🕒
iSpeech.org In this video, Katie Paxton-Fear @InsiderPhD shares with me her methodology for bug bounty hunting. Full video: https://www.youtube.com/watch?v=pzv-Lu7TbFI Katie
December 1st, 2019 | 🕒
TTS Demo Hello everyone. In this video I will discuss in detail about the Blind SQL Injection attack, which is
November 23rd, 2019 | 🕒
TTS Bot detection over IP networks isn't easy, but it's becoming a fundamental part of network security practice. With the
November 22nd, 2019 | 🕒
https://www.ispeech.org/text.to.speech A Technical Deep Dive Into Insider Kubernetes Attack Vectors In part one and part two of our series on
November 12th, 2019 | 🕒
Free Text to Speech In this video I talk about a simplified approach to bug bounty hunting, a methodology that




















Gloss