Send fake mail to hack your friends
Social engineering is an trick to enter credentials on malicious web pages by manipulating human interaction with basic level of security. According to ethical hacking researcher of International Institute of Cyber Security (IICS), social engineering attacks are popular because everyone is not aware of basic level of security. Most of the attack contains social engineering methods. While investigating such cyber cases by cyber forensics team of International Institute of Cyber Security (IICS) attack cases, it is found that most of the attacks are done using social engineering tricks. These attacks are performed by gathering information of the target. Today while communicating over the internet, many of us rely on Email Communication. Email phishing is the most common attacks which are done now days. We will show you how you can generate fake phishing mails in couple of minutes.
- For testing we are using Kali Linux 2019.1 amd64. This tool we are testing on live boot of Kali Linux 2019.1 amd64.
Installation :-
- For cloning type git clone https://github.com/Dionach/PhEmail.git
root@kali:~/Downloads# git clone https://github.com/Dionach/PhEmail.git
Cloning into 'PhEmail'…
remote: Enumerating objects: 88, done.
remote: Total 88 (delta 0), reused 0 (delta 0), pack-reused 88
Unpacking objects: 100% (88/88), done.
root@kali:~/Downloads# cd PhEmail/
root@kali:~/Downloads/PhEmail# ./phemail.py
PHishing EMAIL tool v0.13
Usage: phemail.py [-e ] [-m ] [-f ] [-r ] [-s ] [-b ]
-e emails: File containing list of emails (Default: emails.txt)
-f from_address: Source email address displayed in FROM field of the email (Default: Name Surname name_surname@example.com)
-r reply_address: Actual email address used to send the emails in case that people reply to the email (Default: Name Surname name_surname@example.com)
-s subject: Subject of the email (Default: Newsletter)
-b body: Body of the email (Default: body.txt)
-p pages: Specifies number of results pages searched (Default: 10 pages)
-v verbose: Verbose Mode (Default: false)
Usage of Phemail :-
- After starting phemail. You can gather your target email addresses to send malicious email.
- Type ./phemail.py -S google -d example.com -F 1 -p 12
- -S is used to send query on any search engine. We have used google to search for the email addresses of target domain.
- -d is used to gather domain: of email addresses. NOTE: For security of the tested domain we have changed original domain name to example. The above generated list is used in sending malicious email.
- -F is used in format of email addresses. As phemail collects emails from internet using search engine, using this option it will gather email addresses in the form of firstname surname.@example.com
- -p is used to specify no. of mail addresses to be fetch from target domain. Here 12 mail addresses will be fetched.
root@kali:~/Downloads/PhEmail# ./phemail.py -S google -d example.com -F 1 -p 12
Gathering emails for domain: example.com
Google Query: example
./phemail.py:281: UserWarning: No parser was explicitly specified, so I'm using the best available HTML parser for this system ("lxml"). This usually isn't a problem, but if you run this code on another system, or in a different virtual environment, it may use a different parser and behave differently.
The code that caused this warning is on line 281 of the file ./phemail.py. To get rid of this warning, pass the additional argument 'features="lxml"' to the BeautifulSoup constructor.
html = BeautifulSoup(data)
100%
agus.kurniawan@example.com
anders.liliegren@example.com
andrea.wiseman@example.com
andrew.cavallaro@example.com
anna.faoagali@example.com
antonette.sullivan@example.com
ashfaq-ahmad.jan@example.com
ayman-al.maaraf@example.com
bernadette.oulton@example.com
bobby-esther.mak@example.com
carolyn.riley@example.com
danny.wilson@example.com
dinesh-varma.indukuri@example.com
doctor.example@example.com
- For testing we have used temporary mail id. Go to
https://temp-mail.org/en/ - Add the temporary mail in emails.txt
root@kali:~/Downloads/PhEmail# nano emails.txt
GNU nano 3.2 emails.txt
halevedopo@direct-mail.info
- Save file, press Ctrl + X Then press Shift + y & press enter.
- Type nano body.txt to create body of the phishing email. Write text which will display in phishing email.
root@kali:~/Downloads/PhEmail# nano body.txt
GNU nano 3.2 body.txt
need to talk right now
- Save file, press Ctrl + X Then press Shift + y & press enter.
- Type ./phemail.py -e emails.txt -f “Name Surname name_surname@example.com” -r “Name Surname name_surname@example.com” -s “Subject” -b body.txt
- -e is used to give list of email ids.
- -f is from_address: Source email address displayed in FROM field of the email.
- -r is reply_address: Actual email address used to send the emails in case that people reply to the email
- -s is used to write subject of email.
- -b is used to write body of email.
root@kali:~/Downloads/PhEmail# ./phemail.py -e emails.txt -f "Name Surname name_surname@example.com" -r "Name Surname name_surname@example.com" -s "Subject" -b body.txt
Domain: direct-mail.info
SMTP server: mail.direct-mail.info
./phemail.py:115: UserWarning: No parser was explicitly specified, so I'm using the best available HTML parser for this system ("lxml"). This usually isn't a problem, but if you run this code on another system, or in a different virtual environment, it may use a different parser and behave differently.
The code that caused this warning is on line 115 of the file ./phemail.py. To get rid of this warning, pass the additional argument 'features="lxml"' to the BeautifulSoup constructor.
html = BeautifulSoup(body)
Sent to halevedopo@direct-mail.info
Domain: outlook.com
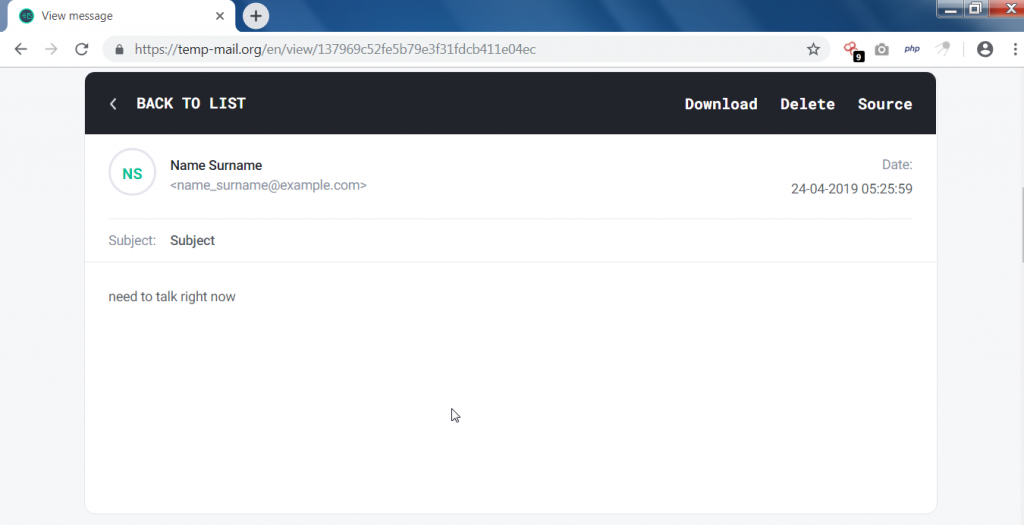
- Above query has sent the phishing link on target mail address. The same result is shown in ethical hacking classes of international Institute of Cyber Security
- Below is the testing mail box.

- The above mail box has received the mail.
Analyzing Temporary Mail Header :-
- Opening email header of temporary mail, shows same email address in from & reply:to.
Received: from 127.0.0.1
by node3 (Haraka/2.8.16) with ESMTP id 5055F1D0-04FF-4831-B67F-CC4EA11CFE35.1
envelope-from name_surname@example.com;
Wed, 24 Apr 2019 11:55:34 +0000
Content-Type: multipart/related;
boundary="===============1127976200482479669=="
MIME-Version: 1.0
from: Name Surname name_surname@example.com
subject: Subject
reply-to: Name Surname name_surname@example.com
to: josotese@emailapps.infoThis is a multi-part message in MIME format.
--===============1127976200482479669==
Content-Type: multipart/alternative;
boundary="===============1585715368107923823=="
MIME-Version: 1.0
--===============1585715368107923823==
Content-Type: text/plain; charset="us-ascii"
MIME-Version: 1.0
Content-Transfer-Encoding: 7bitThis is the alternative plain text message.
--===============1585715368107923823==
Content-Type: text/html; charset="us-ascii"
MIME-Version: 1.0
Content-Transfer-Encoding: 7bit
need to talk right now
--===============1585715368107923823==--
--===============1127976200482479669==--
- Above shows same email id in from & to.
Tracing Email ID :-
- Further we have traced above header using online email tracer. Go to : https://www.iplocation.net/trace-email

- Email tracer has found location from where mail has send.







Gloss