Rekall – Memory Forensic Framework
Text to Speech Voices
Rekall is a memory forensic framework that provides an end-to-end solution to incident responders and forensic analysts. From state of the art acquisition tools, to the most advanced open source memory analysis framework.
It strives to be a complete end-to-end memory forensic framework, encapsulating acquisition, analysis, and reporting. In particular Rekall is the only memory analysis platform specifically designed to run on the same platform it is analyzing: Live analysis allows us to corroborate memory artifacts with results obtained through system APIs, as well as quickly triage a system without having to write out and manage large memory images (This becomes very important for large servers where the time of acquisition leads to too much smear).
The team also ensures the memory analysis tools are stable and work on all supported platforms (For example Rekall features the only memory imaging tool available for recent versions of OSX, that we know of – and it is open source and free as well!).
[adsense size='1']
Rekall is the only open source memory analysis tool that can work with the windows page file and mapped files. Rekall also includes a full acquisition solution (in the aff4acquire plugin) which allows the acquisition of the pagefile and all relevant mapped files (Rekall does this by executing a triaging routine during acquisition).
Support
Rekall should run on any platform that supports Python.
Rekall supports investigations of the following 32bit and 64bit memory images:
- Microsoft Windows XP Service Pack 2 and 3
- Microsoft Windows 7 Service Pack 0 and 1
- Microsoft Windows 8 and 8.1
- Linux Kernels 2.6.24 to 3.10.
- OSX 10.7-10.10.x.
Rekall also provides a complete memory sample acquisition capability for all major operating systems (see the tools directory).
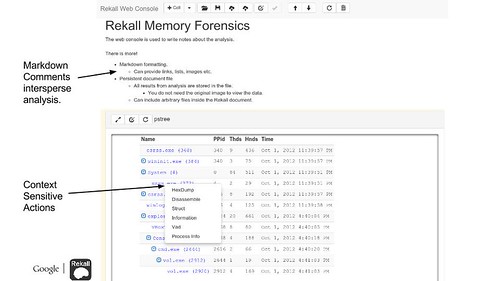
Additionally Rekall now features a complete GUI for writing reports, and driving analysis, try it out with:
|
1
|
rekall webconsole --browser
|
History
In December 2011, a new branch within the Volatility project was created to explore how to make the code base more modular, improve performance, and increase usability. The modularity allowed Volatility to be used in GRR, making memory analysis a core part of a strategy to enable remote live forensics. As a result, both GRR and Volatility would be able to use each others’ strengths.
Over time this branch has become known as the “scudette” branch or the “Technology Preview” branch. It was always a goal to try to get these changes into the main Volatility code base. But, after two years of ongoing development, the “Technology Preview” was never accepted into the Volatility trunk version.
[adsense size='1']
Since it seemed unlikely these changes would be incorporated in the future, it made sense to develop the Technology Preview branch as a separate project. On December 13, 2013, the former branch was forked to create a new stand-alone project named “Rekall.” This new project incorporates changes made to streamline the codebase so that Rekall can be used as a library. Methods for memory acquisition and other outside contributions have also been included that were not in the Volatility codebase.
Rekall strives to advance the state of the art in memory analysis, implementing the best algorithms currently available and a complete memory acquisition and analysis solution for at least Windows, OSX and Linux.
You can download Rekall here:
– Apple OS X – Rekall_1.4.1_Etzel_OSX.zip
– Windows 64-bit – Rekall_1.4.1_Etzel_x64.exe
– Windows 32-bit – Rekall_1.4.1_Etzel_x86.exe
Or read more here.








Gloss