Potential cyberwar begins as Iran takes down US government website
A hacking group that claims to be working for the Iranian government today hacked a U.S. government website in what may be the first strike in a new cyberwar between the two countries.
The hack, which targeted the U.S. Federal Depository Library Program, was claimed by those behind it to be a revenge attack for a drone strike in Iraq Jan. 3 that killed Iranian Maj. Gen. Qassem Soleimani.
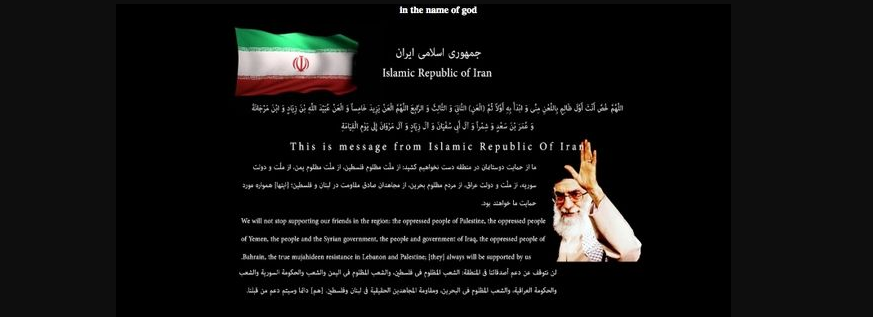
“This is message from the Islamic Republic of Iran,” the hackers wrote on the website. “We will not stop supporting our friends in the regions, the oppressed people of Palestine, the oppressed people of Yemen, the people, and the Syrian government, the people and government of Iraq, the oppressed people of Bahrain, the true mujahideen resistance in Lebanon and Palestine.”
The hackers added that “this is only a small part of Iran’s cyber ability. We’re always ready. To be continued.”
The hack was confirmed by the U.S. Department of Homeland Security Cybersecurity and Infrastructure Agency. The agency added, however, that “at this time, there is no confirmation that this was the action of Iranian state-sponsored actors.”
Iran has vowed to retaliate for the drone strike, and cyberwarfare is one path the Islamic republic is expected to take. The threat is considered real, with the Financial Times reporting that both the U.S. public and private sectors are on high alert. Government officials are said to expect attacks to be focused on disrupting anything from corporate and municipal information technology systems to transit, logistics, healthcare or U.S military facilities.
“Iran will retaliate. There is no doubt about this,” Hank Thomas, chief executive officer at venture capital firm Strategic Cyber Ventures told SiliconANGLE. “However, they will be looking for a way to appear both powerful and credible militarily at this pivotal point, without appearing to be a regional bully that traditionally relies on two-bit terrorist actions because they lack a robust advanced military response capability that could challenge the U.S. head-on.”
Thomas added that “whowing off their offensive cyber capabilities and the reach it provides them beyond the region could very well be a part of their most likely course of action. A most dangerous course of action includes a combination of cyber and kinetic strikes both inside the region and beyond.”
Chris Morales, head of security analytics at cybersecurity firm Vectra AI Inc., noted that Iran identified cyberwar capabilities as part of its attack strategy a decade ago and has gradually been building up capabilities since the country’s nuclear centrifuges were hit by the Stuxnet virus in 2010.
“Cyber offensive actions have been ongoing and instigated by both sides through that time period,” Morales said. “Iran is not as sophisticated in its cyber capabilities as it primarily leverages black market malware as opposed to the customer built malware used by U.S. and Israel cyber command. I do think Iran would prompt a cyberstrike, but they also would measure that response with the threat they know they face from a US ongoing offensive.”
Rick Holland, chief information security officer and vice president of strategy at digital risk protection firm Digital Shadows Ltd., countered by warning that Iran is not the minnow some suggest.
“Iran’s offensive cyber capabilities have grown significantly since the 2012 days of banking sector denial of service attacks and Saudi Aramco/Shamoon destructive malware,” he said. “In 2019, both the U.S. and U.K. governments released multiple public alerts regarding Iranian cybersecurity threats.”
That’s likely to escalate as a result of Soleimani’s death,” he noted.
“The good news for defenders is security controls like multi-factor authentication can mitigate against account takeover attempts,” Holland said. “Email security controls like ‘defanging’ email attachments by creating PDFs of them can mitigate malicious attachments in spear-phishing emails. Up-to-date anti-malware protection can help reduce the risks of wiper malware. The benefit of these controls is that they protect against a multitude of threats, not just Iranian attackers.”
Image: U.S. Federal Depository Library Program
Since you’re here …
Show your support for our mission by our 1-click subscribe to our YouTube Channel (below) — The more subscribers we have the more then YouTube’s algorithm promotes our content to users interested in #EnterpriseTech. Thank you.
Support Our Mission: >>>>>> SUBSCRIBE NOW >>>>>> to our Youtube Channel
… We’d like to tell you about our mission and how you can help us fulfill it. SiliconANGLE Media Inc.’s business model is based on the intrinsic value of the content, not advertising. Unlike many online publications, we don’t have a paywall or run banner advertising, because we want to keep our journalism open, without influence or the need to chase traffic.The journalism, reporting and commentary on SiliconANGLE — along with live, unscripted video from our Silicon Valley studio and globe-trotting video teams at theCUBE — take a lot of hard work, time and money. Keeping the quality high requires the support of sponsors who are aligned with our vision of ad-free journalism content.
If you like the reporting, video interviews and other ad-free content here, please take a moment to check out a sample of the video content supported by our sponsors, tweet your support, and keep coming back to SiliconANGLE.







Gloss