Microsoft Outlook Critical Vulnerability Allows Hackers to Easily Obtain Windows Passwords
Powered by iSpeech
Microsoft released the Patch Tuesday update to address 67 vulnerabilities multiple Windows and software. One of them is a vulnerability in Microsoft Outlook. It was discovered by Will Dormann of the CERT Coordination Center (CERT/CC).
CVE-2018-0950 is a vulnerability in Microsoft Outlook that may allow an attacker to steal sensitive information (including Windows user’s computer login credentials). All the attacker needs to do is the victim to use Microsoft Outlook and preview the email without any other user interaction.
Dormann said remote attackers can exploit this vulnerability by sending RTF emails to target victims, which contain remotely hosted image files (OLE objects) and are loaded by an attacker-controlled SMB server.
Because Microsoft Outlook automatically renders OLE content, it will use SSO to initiate automatic authentication of the attacker’s server through the SMB protocol. The victim’s username and password will be sent to the attacker in the form of an NTLMv2 hash. It may allow an attacker to enter the victim’s system.
[adsense size='1' ]
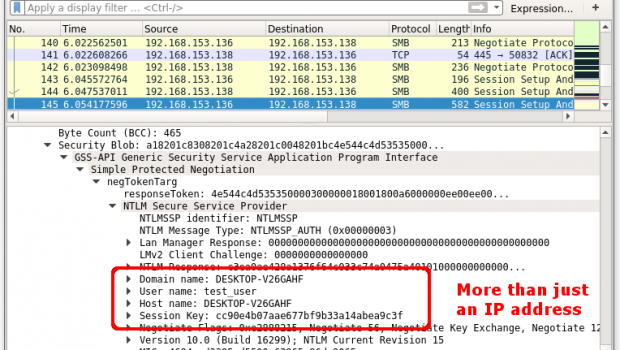
Through Dormann’s test, the following content will be revealed:
- IP address
- Domain name
- Username
- Hostname
- SMB session key
Dormann first reported this vulnerability to Microsoft in November 2016. As mentioned at the beginning of the article, Microsoft has released a fix to resolve this issue on the Patch Tuesday this month.
However, Dormann pointed out that although Microsoft spent nearly 18 months to develop fixes for this vulnerability, this patch only prevents Microsoft Outlook from automatically launching SMB connections when previewing RTF emails, which does not prevent all SMB attack.
Dormann said that on the Windows platform, there are many ways that Microsoft Outlook clients can initiate SMB connections. Regardless of the method, as long as the SMB connection is initiated, the Microsoft Outlook client’s IP address, domain name, username, hostname, and SMB session key may all be compromised.
To this end, Dormann suggested that Windows users, especially corporate network administrators, can mitigate the security risks associated with this vulnerability through the following steps:
- Installed Microsoft fix for CVE-2018-0950, This update prevents automatic retrieval of remote OLE objects in Microsoft Outlook when rich text email messages are previewed. If a user clicks on an SMB link, however, this behavior will still cause a password hash to be leaked.
- Block inbound and outbound SMB connections (eg 445/tcp, 137/tcp, 139/tcp, 137/udp and 139/udp);
- Disables NT LAN Manager (NTLM) Single Sign-On (SSO) authentication;
- Persist in using a relatively complicated password, even if the hash value of the password is stolen, it can not be easily hacked;
- Most importantly, don’t click on any of the suspicious links provided in the email.







Gloss