Lab of a Penetration Tester: Hacking with Human Interface Devices
Kautilya has the ability to do interesting and useful stuff using a Human Interface Device. But sometimes, nothing beats a simple reverse shell. Recently, I added some new payloads to Kautilya which are useful for getting reverse shells using different protocols.
This post describes the payloads which give us the capability of having reverse connect PowerShell shells from Windows targets. With these payloads, Kautilya now has improved capability to provide us with a foothold machine in penetration testing engagements where use of Social Engineering techniques is allowed. Those who follow my other tool Nishang, I did a five part blog series on that.
Lets see the payloads in action.
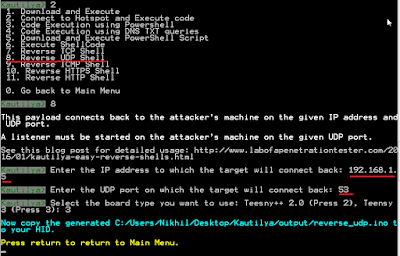
Reverse TCP and Reverse UDP
Both of the payloads can be used with a standard netcat listener both on Windows and Linux. On Windows, Powercat can also be used. We just need to provide the IP to which the target connects back and the port to use. Upload it to a HID and send it to a target.
When a target connects the device, this is how it looks like at the listener.
Neat! An intercative reverse PowerShell shell.
Reverse ICMP
My favorite one for bypassing network restrictions, a reverse shell completely over ICMP. This payload needs a listener, icmpsh_m.py, from the icmpsh suite. Run the command "sysctl -w net.ipv4.icmp_echo_ignore_all=1" and start the listener. This is how it looks like on a successful connection:
This one has been useful in so many penetration tests.
Reverse HTTPS and Reverse HTTP
Reverse HTTPS is proxy aware and uses valid HTTPS traffic for reverse PowerShell shell. Its target part (typing done on the target machine) is very small and this makes it very useful. Currently, a listener on Windows is required. Run Invoorke-PoshRatHttps.ps1 in the extras directory of Kautilya from an elevated shell. The listener script adds exception to the Windows Firewall for incoming requests on the specified port.
Awesome, isn;t it?
Hope you liked the post! As always I look forward for feedback and comments.
Learn penetration testing of a highly secure live Windows network with me in PowerShell for Penetration Testers Training at:









Gloss