Investing In Secular Trends: Hacking And Cybersecurity
Black_Kira/iStock via Getty Images
As our digital footprints grow at an exponential rate and become more accessible from anywhere on Earth, and on multiple platforms, it is more important than ever to protect our data. Businesses and individuals alike are becoming more vulnerable to outside and nefarious actions by those that can exploit private and sensitive information for financial gain or to cause disruptions. I believe that this activity will continue for the foreseeable future (measured in years and decades) and is likely to become more top of mind for corporate America as well as individuals.
Cybersecurity is not a new term or new concern by any means, but I believe that the prevalence of hacks and need for robust protection will be a secular trend, driven by the exponential growth in data. I characterize a secular trend as one that continues despite business cycles, political environments, interest and inflation rates, and other factors, including most exogenous shocks. Companies experiencing secular growth provide pockets of opportunity during the current period of stock market uncertainty, rising interest rates, commodity volatility driven by supply/demand imbalances, and logistical issues. Clearly, there are limits to this description. Another pandemic or world war would certainly be expected to derail most trends, cyclical or secular.
Growing Vulnerabilities And Opportunities
Economic disruptions, logistical challenges, and supply chain bottlenecks contributed to the creation of new vulnerabilities for adversaries (i.e., hackers) to exploit. The growing number of leaks and attacks in recent years supports the thesis that adversaries place a high value on data, control of assets, and collecting ransoms when possible. Attackers are increasingly avoiding the use of malware to breach systems and steal information, instead seeking legitimate administrator credentials to gain access to target assets and data. This strategy helps the adversaries avoid detection by legacy antivirus products that are ill-equipped to prevent or stop this activity. In 2021, there was a 45% increase in “interactive intrusion campaigns” according to CrowdStrike’s (CRWD) 2022 Global Threat Report, with state-sponsored and financially motivated attacks representing about two-thirds of this activity.
Cloud computing providers are an especially attractive target for would-be hackers. If these parties are able to gain access to administrator level credentials, then they may be able to move from one cloud “tenant” to another, placing the data of numerous entities at risk from one breach. Undoubtedly, this is of the utmost importance for firms like Microsoft (MSFT) and Amazon (AMZN) as Azure and AWS continue to experience rapid growth.
According to the CrowdStrike report, the number of adversaries continues to grow around the world, both named (and possibly state-backed) and grassroots organizations. In 2021, there was an 82% increase in ransomware-related data leaks. While the attack on the Colonial Pipeline was well-publicized, there were at least 2,686 such ransomware-related data leaks in 2021.
For context, the Colonial Pipeline attack in May 2021 was one of at least two significant cyberattacks that occurred that month. Colonial provides gasoline, diesel, and jet fuel to the southeast and east coast of the U.S. The loss of control of this infrastructure to hackers caused a disruption in fuel supplies and drove prices higher. The attack ended once Colonial paid a ransom of 75 Bitcoins, which was valued at about $4 million at the time. The Department of Justice was subsequently able to recover the majority of this figure, but unable to do anything about the estimated 100 gigabytes of data that was stolen from the company’s servers.
Brazil-based meat processing firm JBS S.A., the largest producer of beef, chicken, and pork by sales globally, was also attacked in May 2021. As a result of the attack, the company’s facilities in the U.S. were rendered inoperative. Like with Colonial, JBS paid a ransom to the attackers using Bitcoin, this time in the amount of about $11 million.
Most critical infrastructure, both digital and real, is connected to the internet, making it vulnerable to attack. Similar to the Colonial Pipeline assets, electrical power and other critical assets that support our often-underappreciated way of life are vulnerable to destruction, loss of control, and ransom, among other potential risks.
Some of these risks could be mitigated by making the infrastructure and processes themselves more analog and separate from internet connection. For example, disaggregation of power generation and distribution would limit the ability of hackers to take down large swaths of the grid, but we are nowhere near what is required for that. Despite rapid growth in recent years, only a small percentage of U.S. homes are powered completely or in part by solar, according to the U.S. Energy Information Administration.
The growing number of attacks, coupled with the potential financial risks, means that countermeasures will grow in importance and value. Firms offering protection and solutions to these issues are positioned to benefit for years to come. Furthermore, the demand for these products and services would be expected to be inelastic as no competent management with vulnerable data or real assets would ignore these risks. This inelastic demand means firms operating in this space should be able to maintain healthy gross margins, and long-term growth.
Capturing Opportunity
Because of the long runway and importance of cybersecurity, there will be companies that benefit by experiencing significant growth for years to come. While I believe that analog systems, disconnecting from the internet, and disaggregation of power generation would be powerful countermeasures, I do not see that becoming a reality anytime soon (or ever). Because of this, I will focus on companies that are already operating in the cybersecurity space.
CrowdStrike, mentioned above, is a relatively new company, having gone public in 2019. The company has seen rapid growth in subscription customers and recurring revenue over the last five years. Customers include 65 member of the Fortune 100 and more than half of the Fortune 500.
Crowdstrike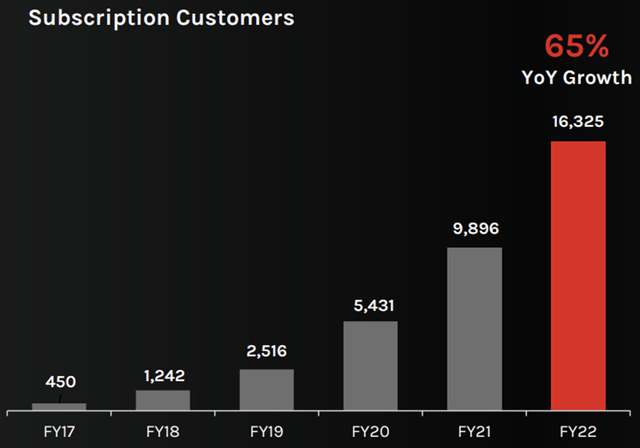
Other significant players in the space include Palo Alto Networks (PANW), Check Point Software (CHKP), and Fortinet (FTNT). Firms in this space have experienced double-digit revenue growth (Check Point being an exception) in recent years while maintaining gross margins of more than 70%.
Like with most investment suggestions I make, I prefer not to attempt to pick individual winners and losers. Instead, I like to gain exposure through the use of low cost and liquid ETFs. Fortunately, there is a cybersecurity ETF, the Global X Cybersecurity ETF (BUG), which holds shares in about 31 companies operating in the space, with the ones mentioned above representing some of the largest positions. The fund is allocated about 77% to U.S.-based companies with the remaining 23% split between the UK, Japan, and Africa/Middle East. The expense ratio for BUG is 0.50%.
Recent performance has been strong on a relative basis, with the fund outperforming the SPDR S&P 500 ETF Trust (SPY) and Invesco QQQ Trust (QQQ) year-to-date as well as over the last three- and five-year periods.
Morningstar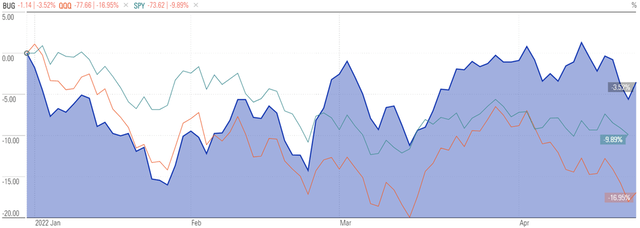
Year-to-date
Morningstar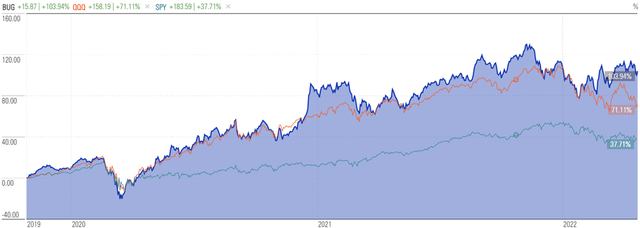
Trailing three years
Final Thoughts
The threat to our data and critical infrastructure is real and unlikely to disappear anytime soon. The number of adversaries and their actions against corporations and governments is growing at an alarming rate. It will require significant resources to combat these threats, and to protect our data and way of life. Companies that provide sophisticated solutions to these issues will benefit in the long run as their services become increasingly necessary and valuable. Because of the nature of these threats, and the opportunities that they create for cybersecurity businesses, it is reasonable to expect this area of the tech sector to succeed regardless of business cycles and politics. I look forward to your feedback in the comment section below.








Gloss