Introduction to LFI/RFI vulnerabilities and their mitigation – Local and Remote File Inclusion hack
https://www.ispeech.org/text.to.speech
Take the complete LFI/RFI course (3 more videos) on Duckademy.
Check out the course: https://www.duckademy.com/course/LFI-RFI
Local File Inclusion and Remote File Inclusion (LFI/RFI) attacks are popular amongst hackers. It mostly affects web applications written in PHP, so a great majority of websites could be exposed to it.
DOWNLOAD this lfi/RFI tutorial and the virtual machine from here: http://www.duckademy.com/course/LFI-RFI
This LFI hacking tutorial is the 2nd tutorial of the Local File Inclusion and Remote File inclusion hacking course at Duckademy.
What we will do in this LFI hacking and RFI hacking tutorial:
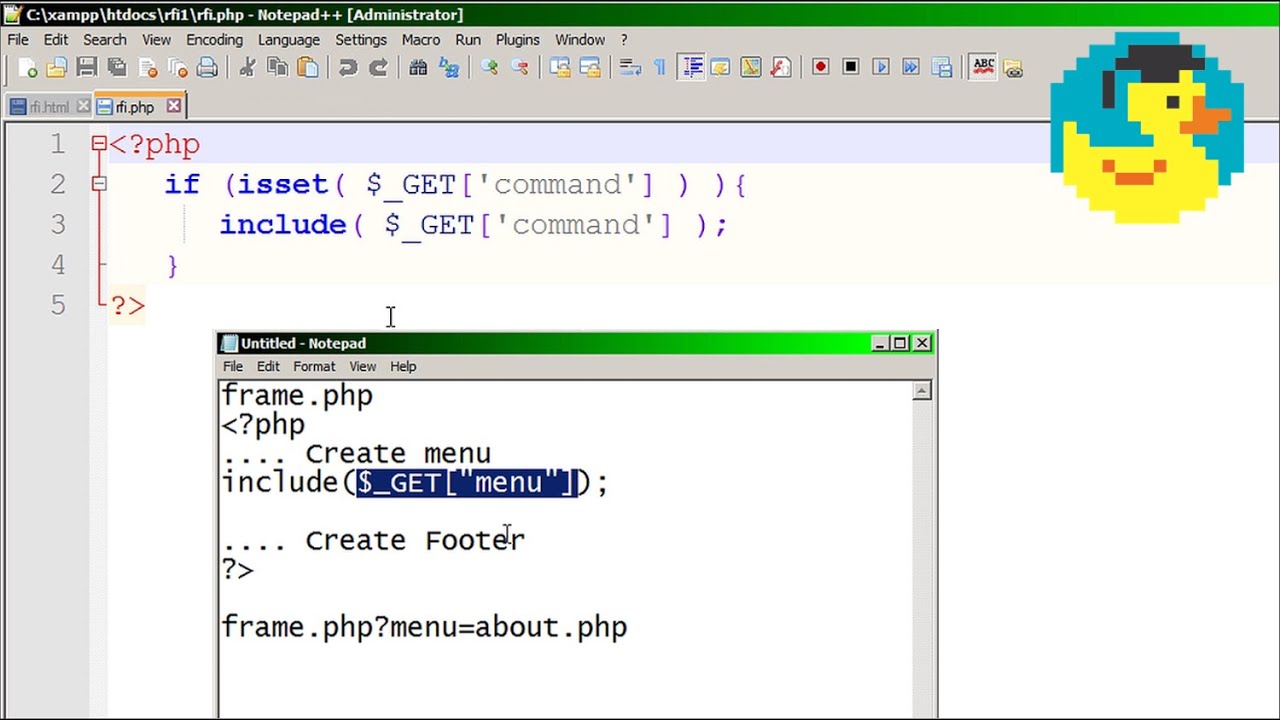
1. We will look for a local file inclusion and a remote file inclusion and you will understand the reason behind these kind of vulnerabilities.
2. We will cover the countermeasures against these attacks as well.
Here is the 1st LFI hacking tutorial (Setting up the test environment for LFI/RFI): https://youtu.be/W5Bw_zAQub4
The goal of this minicourse is to teach you how to audit websites against local file inclusion and remote file inclusion (LFI hacking and RFI hacking) attacks.
These kind of attacks and hacks are very often overlooked because they are not as well known as SQL injection or XSS attacks. However these hacks can cause lots of problems and can be very harmful.
Please note that this local file inclusion and remote file inclusion (LFI/RFI) hacking tutorial is for educational purposes only.
SUBSCRIBE NOW FOR NEW FREE IT TUTORIALS!
https://www.youtube.com/c/DuckademyITcourses?sub_confirmation=1
SUBSCRIBE TO OUR EMAIL LIST!
https://www.duckademy.com/#dialog-newsletter
FOLLOW US!
Facebook ► https://www.facebook.com/duckademy
Twitter ► https://twitter.com/duckademy
Google+ ► http://gplus.to/duckademy
Linkedin ► https://www.linkedin.com/company/duckademy
---------------------------------------------------------------------------------
2016-04-06 14:29:30
source







Gloss