Integrity Management: Computer Security Lectures 2014/15 S1
https://www.ispeech.org
This video is part of the computer/information/cyber security and ethical hacking lecture series; by Z. Cliffe Schreuders at Leeds Beckett University. Laboratory work sheets, slides, and other open educational resources are available at http://z.cliffe.schreuders.org.
The slides themselves are creative commons licensed CC-BY-SA, and images used are licensed as individually attributed.
Topics covered in this lecture include:
Integrity Management
Integrity: Prevent unauthorised changes (modification / deletion)
Protecting Integrity
Standard file (and directory) permissions
Network controls (firewalls) and services
Authentication
File attributes
Various filesystems support different attributes
Attributes can be used to make files
Immutable: cannot modify, link, or delete (even root!)
Append only: cannot modify except by adding to the end of the file (good for logs)
Read only filesystems
Read-only media
Detecting changes
Host-based intrusion detection system (HIDS)
Known good state
Diff and Rsync
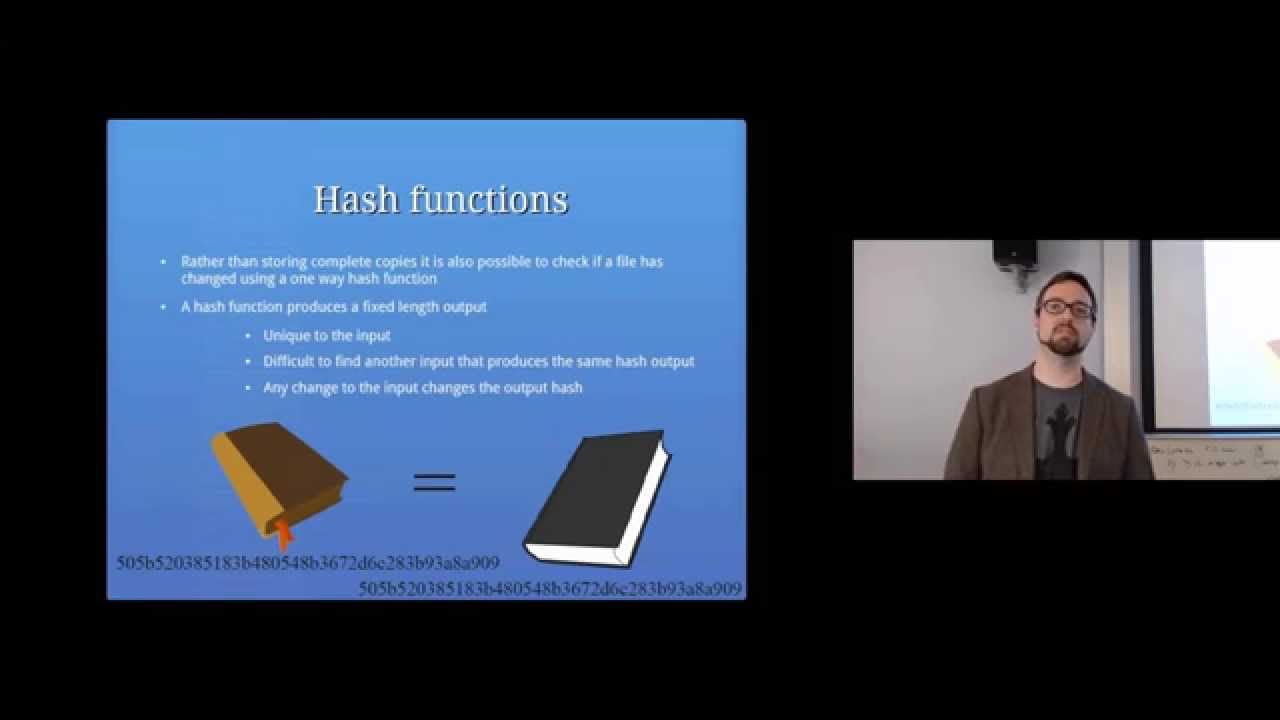
Hash functions
We can store a hash and when we recompute we can tell whether the file has changes (the hash is different), or it is exactly the same (the hash is the same)
Linux hash programs
For example: shasum (SHA1 by default), sha1sum, sha224sum, sha256sum, sha384sum, sha512sum, md5sum
Integrity checking tools
Shasum and md5sum can also do this
Linux examples of integrity checking tools include: Tripwire (there is the original open source program, and a proprietory version), Advanced Intrusion Detection Environment (AIDE), Samhain, and OSSEC
BSD systems include mtree
Some of these tools include other features, such as rootkit detection, log analysis, and stealth features to hide themselves
Example script
Packaging and integrity
Depending on the package management system used, may keep hashes to detect changes to files since install
RPM based systems (such as Red Hat, Fedora, and OpenSUSE, keep a hash in the database (rpm -V : verify)
rpm -Va
Limitations
Limitations of integrity checking
Other monitoring to consider
Conclusion
video, sharing, camera phone, video phone, free, upload
2015-01-05 14:50:22
source







Gloss