InnfiRAT Malware Steals Litecoin And Bitcoin Wallet Information

A remote access Trojan (RAT) dubbed InnfiRAT comes with extensive capabilities to steal sensitive information, including cryptocurrency wallet data. Zscaler's ThreatLabZ team took a closer look at its inner workings, although the malware has been in the wild for a while.
The earliest this RAT was spotted is November 2017, according to security researcher James_inthe_box, but this is the first time it was analyzed more seriously.
InnfiRAT is a .NET malware the ThreatLabZ team found, with anti-VM and process checks designed to help it detect when it's running in a sandboxed environment, typically used for malware analysis.
After infecting the target's computer, InnfiRAT will copy itself into %AppData%/NvidiaDriver.exe and will write a Base64-encoded PE file in memory that gets decoded to another .NET binary with the actual functionality of the malware.
FYI #Innfirat has been rolling around since 2017:https://t.co/VR5zBLQKIK
— James (@James_inthe_box) September 13, 2019
Persistence and anti-analysis measures
If the RAT discovers that it's running in a sandbox, it will automatically terminate itself, otherwise, it would collect the compromised machine's HWID and country.
InnfiRAT will also terminate itself if it discovers the processes of tools used for process monitoring such as Process Hacker, Process Explorer, and Process Monitor.
The processes of several web browsers will also be enumerated (i.e., Chrome, Yandex, Kometa, Amigo, Torch, Orbitum, Opera, Mozilla) and, if found, will get immediately killed on sight, potentially to unlock the user profiles for easier harvesting.
The malware will also create a scheduled task designed to execute the malicious %AppData%/NvidiaDriver.exe executable on a daily basis just in case the RAT is discovered and killed.

Stealing crypto and cookies
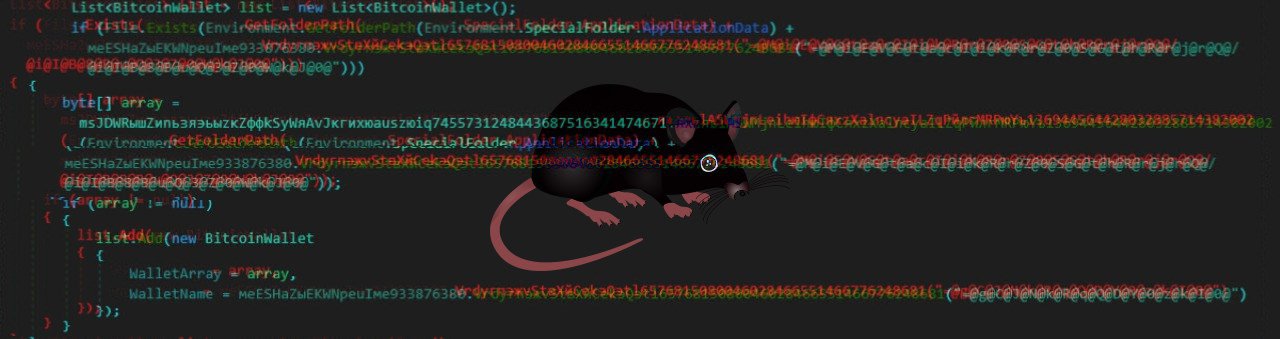
While InnfiRAT's command and control (C2) servers can send it 11 types of commands, the most interesting are those that instruct it to search for and steal Bitcoin and Litecoin wallet data, as well as cookie information from the web browsers that got killed in the reconnaissance stage.
The RAT searches for wallet.dat files in the %AppData%Litecoin and %AppData%Bitcoin folders, with the immediately being collected, if found and delivered to the malware's C2 server.
"InnfiRAT also grabs browser cookies to steal stored usernames and passwords, as well as session data. In addition, this RAT has ScreenShot functionality so it can grab information from open windows," found the Zscaler ThreatLabZ team.
"InnfiRAT sends the data it has collected to its command-and-control (C&C) server and requests further instructions. The C&C can also instruct the malware to download additional payloads onto the infected system."

Text documents of less than 2,097,152 bytes are also collected by the RAT if they're stored on the victim's desktop and get sent to the same pile of exfiltrated data stored on the C2 server.
InnfiRAT's operators can also send it the following commands besides the ones already described above:
• SendUrlAndExecute(string URL) - download a file from a specified URL and executes it
• ProfileInfo() - collect and exfiltrate network, location, and hardware info
• LoadLogs() - write files into specific folders
• LoadProcesses() - get a list of running processes and send it to the C2 server
• Kill(int process) - command to kill a specific process on the victim machine
• RunCommand(string command) - execute a command on the victim machine
• ClearCooks() - clears browser cookies for specific browsers
Indicators of compromise (IOCs) including malware sampled hashes and domains used to drop the RAT and as C2 servers are available at the end of ThreatLabZ team's InnfiRAT write-up.
Last month, two new RATs were discovered by security researchers, one of them targeting several countries as part of a campaign operated by financially motivated threat actors who used a RAT payload dubbed BalkanRAT by the ESET researchers who spotted it.
The other undocumented RAT called LookBack was found by the Proofpoint Threat Insight Team researchers while being delivered via a spear-phishing campaign that targeted three U.S. entities from the utility sector.







Gloss