Initial Access with Evil Calendar Files and GoPhish – CYBER ARMS – Computer Security
Almost every time you sign up for an online event, you get one of those wonderful calendar reminders to set an appointment reminder. In this article we will take a look at using “evil” calendar .ics files in a pentesting or Red Team credential grabbing attack.
Crafting the E-Mail
The first thing we need to do is craft a Social Engineering e-mail to entice our corporate targets. Some may use cute puppy pics, or cat videos are always popular. As our pentesting target is a corporate environment, we will use what is near and dear to every worker – bonuses!
When I created this for a book chapter in my upcoming book, “Advanced Security Testing with Kali Linux”, I used GoPhish for the phishing management campaign. If you haven’t used it before, Gophish is a phishing framework that gives security professionals and pentesters the ability to perform live, real-time phishing attack simulations.
GoPhish is not necessary for our “evil calendar” test, but it is a perfect solution if you wanted to roll the test out to a large number of users. Honestly, you don’t need the calendar .ics file either, you could just used boobytrapped links or attachments in GoPhish for the same effect, but what is the fun in that?
Installing GoPhish
Installing and using GoPhish is very easy. Though I just used it in a local lab, in a corporate test you would need to install GoPhish on a Cloud, VPS or other system with access to an e-mail server.
Download the latest release of GoPhish, extract it, and make the main gophish file executable. Once you run gophish, you need to open a browser to connect to the Web GUI.
When you create a new phishing campaign, you first will create an e-mail template, target users & groups and a landing page, or the fake website that you will use to monitor who fell for the Phishing e-mail and who did not. Then setup your sending mail server in Sending Profiles. Lastly, start the e-mail campaign using the campaign menu.
E-Mail Template
Creating the e-mail template is where you will put your social engineering skills to the test. You want an e-mail that looks believable and have the greatest chance to have your target click on it. Some internal security testing teams may prefer to put a small hint in the e-mail that it is fake.
For the most part though, you want to make the e-mail as real looking as possible for a true test. Gophish allows you to import an e-mail to use as a template or you can use the HTML WYSIWYG editor included.

Good start, now we just need to add our evil calendar event. We can take a .ics calendar file and add a link to a non-existing server, as seen below:

As with any social engineering request, you would use wording that would entice the user to click on the link. I went with the totally innocuous “Evil Calendar Event”. Nobody would ever click on that. On second thought, trust me, yes, they would.
Now just add the Calendar File as an attachment to our E-mail in GoPhish. Again, you don’t need Gophish for this, it just makes it easier for sending large amounts of e-mails during a real test.
When we kick off the GoPhish campaign, our targets get an e-mail that looks something like this:
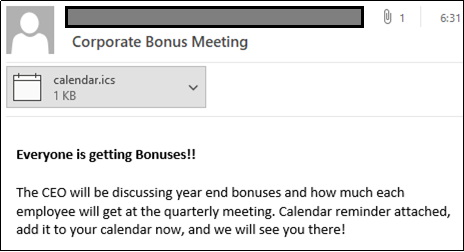
Now the trap is set, we just need to have something to respond to the bogus “corporate_serverjoin_now” link when people click on it. Responder will work perfectly!
Starting Responder
Responder is an LLMNR, NBT-NS and MDNS poisoner, that will answer service requests for multiple services. What’s nice about it is you can set it to prompt users for a login prompt, when they try to surf to a non-existent network resource. This is exactly what we are using in our evil calendar file.
In real life, Responder would have to be running on an internal system, one already connected to the target network – say running on a drop box.
- sudo responder -I eth0 -wb

This starts the responder service and it begins looking for service requests to poison. In our case, we want it to respond to any server request, where the server doesn’t exist, and prompt the user for “login credentials”.
Creds from Calendar Files
Now, back on the target desktop. When the calendar file is opened in Outlook, it looks like this:
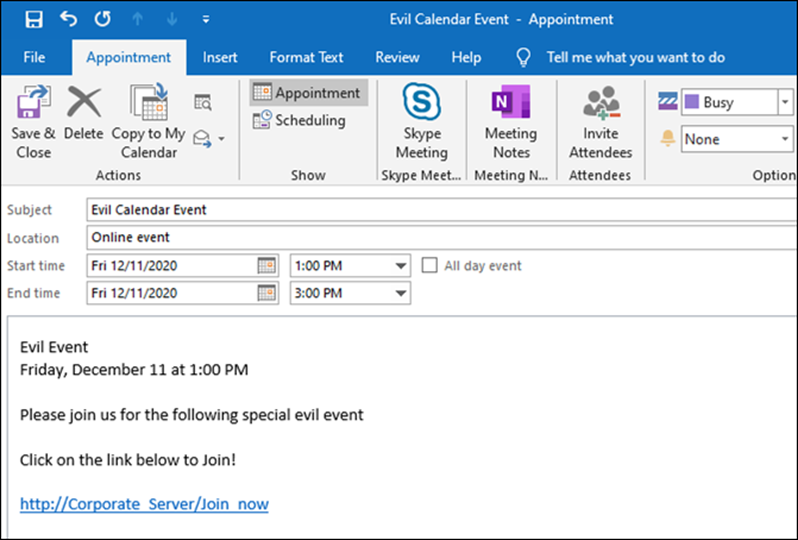
When they click on the “Join Now” link, they will be given a Responder login prompt:

If they enter the credentials, we get them in plain text!
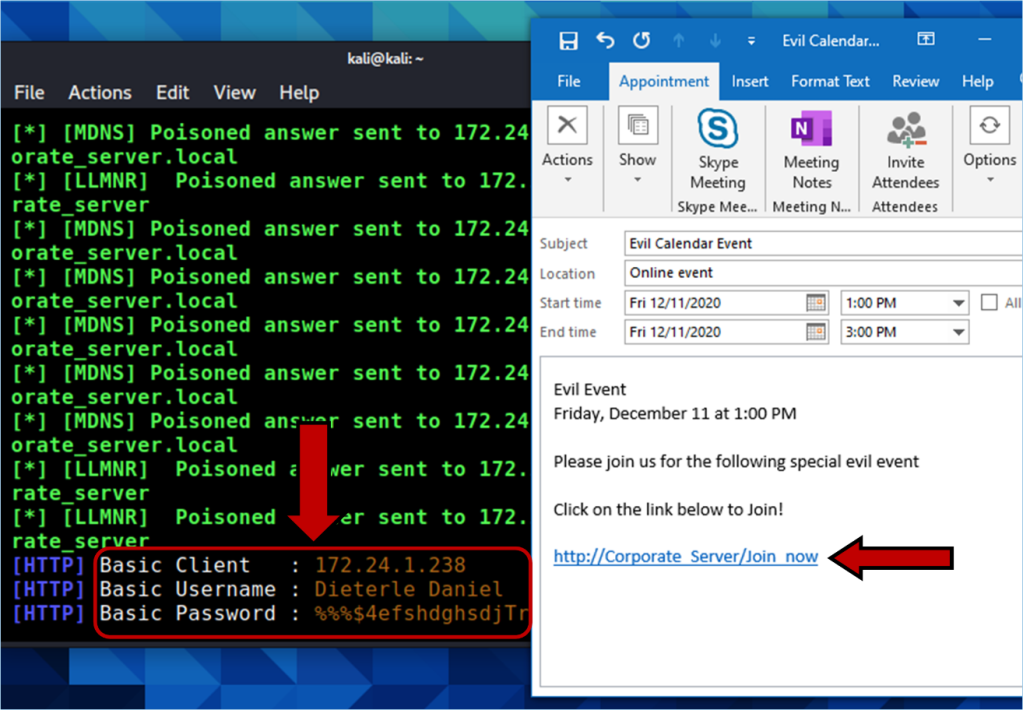
As seen below:
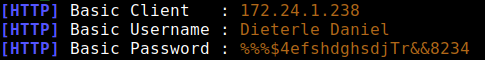
And that’s it! Our job here is done.
Conclusion
As mentioned, you do not need to use GoPhish for this, and you don’t really have to use a calendar event to do it. You could use any link, even one to the Browser Exploitation Framework (BeEF) if you wished.

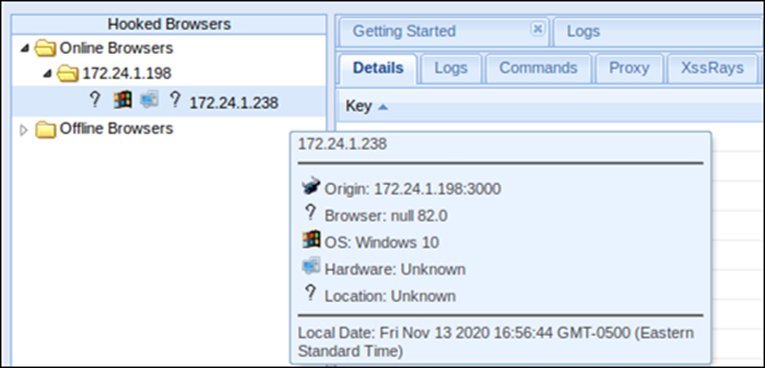
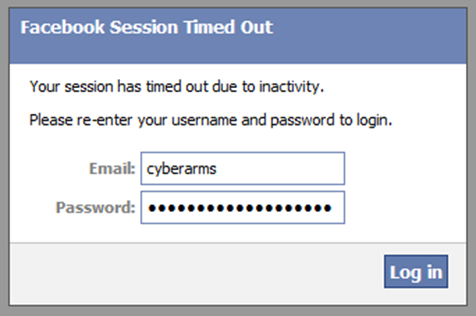
And prompt them for their Facebook Creds, using the BeEF Social Engineering attack:
Though using the Calendar technique is a nice way to get creds if you know you will be onsite or have onsite access on a certain day.
For a lot more information on using Kali Linux as a security testing platform, check out my “Basic Security Testing with Kali Linux” book. For more advanced techniques, keep an eye out for my upcoming book, “Advanced Security Testing with Kali Linux”, available soon!







Gloss