Information security experts are arguing over whether or not a researcher did the right thing in going public with two new serious "zero day" flaws in the Zoom video conferencing app, which has become increasingly popular as people and students work from home in COVID-19 lockdowns.
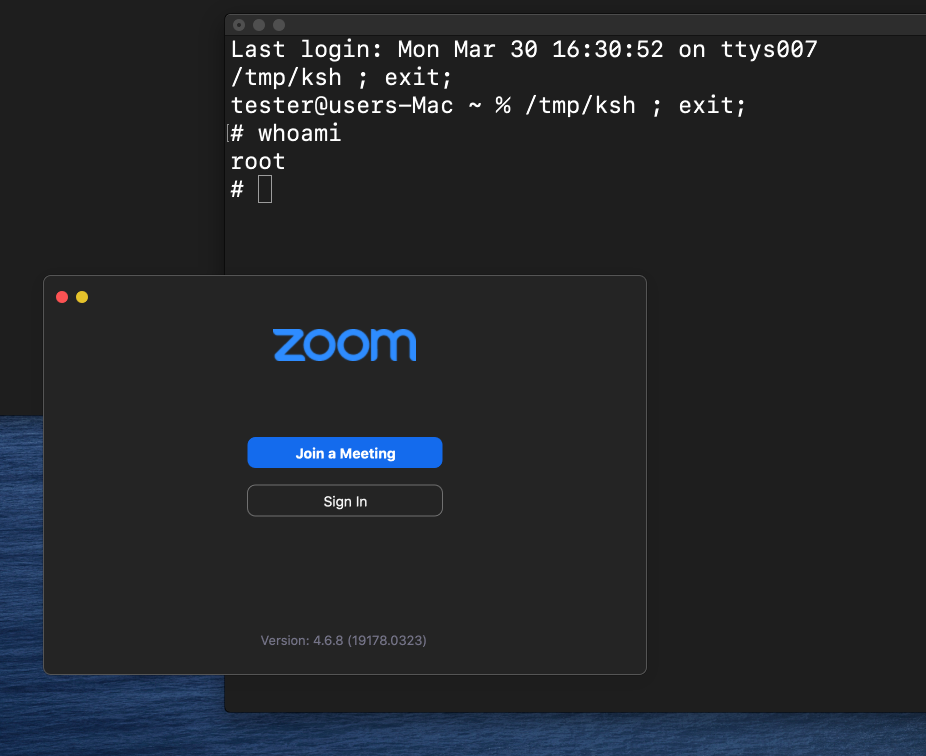
Earlier this week, security researcher Felix Seele first noticed Zoom's dubious installation technique for its Apple macOS client, which doesn't require users to click on install.
"Turns out they (ab)use pre-installation scripts, manually unpack the app using a bundled 7zip [an archiving utility] and install it to /Applications if the current user is in the admin group (no root needed)," Seele said.
Zoom founder and chief executive Eric Yuan thanked Seele and said the installer was designed that way to make video conferencing easier for Mac users.
Thank you for your feedback! We implemented to balance the number of clicks given the limitations of the standard technology. To join a meeting from a Mac is not easy, that is why this method is used by Zoom and others. Your point is well taken and we will continue to improve.
— Eric S. Yuan (@ericsyuan) March 31, 2020
Security researcher and former National Security Agency staffer Patrick Wardle took up the cudgel and published technical details on the installer, in a manner that Seele said was used by macOS malware.
Wardle found that Zoom achieved the consent-less installation by using an application programming interface that is deprecated by Apple meaning it should not be used by developers.
The API is considered dangerous as it performs no validation of what it executes as the macOS root superuser that has full access to all parts of the system.
With the installer, Zoom had created a serious privilege escalation vulnerability that Wardle labelled a zero-day that could be exploited by local, non-admin users to gain root access which is problematic in enterprise settings.
A second zero-day that Wardle documented allows malicious code to be injected into the process space that handles Zoom's access to the microphone and camera on Macs.
Zoom's programming choices here could allow malicious code to record users' video conferences, and surreptitously access microphones and cameras with people receiving no warning prompts.
Wardle's findings were reported in United States technology media, but he did not alert Zoom to them prior to publishing technical details on the vulnerabilities.
It is customary for security researchers to hold back publication of vulnerabilities until the vendor in question has had a chance to verify them and to develop and issue patches for users.
The decision by Wardle to not follow infosec industry responsible disclosure practice has led to criticism from his peers.
Google's director of security and privacy Heather Adkins were among those who in public questioned Wardle going public, followed by former Facebook chief information security officer and Stanford University Internet Observatory researcher Alex Stamos.
Surprisingly, Wardle found support from Google Project Zero researcher Tavis Ormandy who said the flaws had to be fixed now and not later.
Disagree, it's a problem with the installation, and installations are spiking *now*, not in six months. Now is the time to make sure people are aware of the risks, good work @patrickwardle. This is what real responsible disclosure looks like.
— Tavis Ormandy (@taviso) April 1, 2020
Ormandy said that holding off with publication until Zoom had patched the installer would only help future users, and not the massive amount of people who are downloading the video conferencing app onto their systems currently.
In Ormandy's opinion, Wardle had done nothing wrong and instad protected users from danger rather corporate reputations at any cost.
"The media can be a tool to inform; nobody promised it will only ever be flattering to business interests," Ormandy said.
Zoom told iTnews that it will take care of both vulnerabilties, but didn't provide a time frame for fixes.
“We are actively investigating and working to address these issues.
We are in the process of updating our installer to address one issue and will be updating our client to mitigate the microphone and camera issue,” a Zoom spokesperson said.







Gloss