How Can You Determine the Risk of a Threat Actor?
One of the primary goals of an intelligence team is to prioritize the threats that face an organization. This includes how a particular threat actor or campaign impacts the organization’s risk level. In information security, there are well-established models and matrices to categorize and identify threats from a technical perspective. However, what may be overlooked is a model to visualize the risk or impact score of the actual threat actor or group that may be behind the attacks. Including intelligence about the social aspects of cyber threats adds more depth and relevancy to situational awareness. In this post, we explore a model currently used by analysts and researchers at Optiv’s Global Threat Intelligence Center (gTIC) to address this potential gap.
Threat Actor Risk Score
The goal of gTIC’s threat actor risk metric was twofold: Be both expressive and concise. Expressiveness speaks to the fact that there are multiple different ways to measure a cyber threat. Technical risks like vulnerabilities have quantitative scoring metrics like the Common Vulnerability Scoring System (CVSS) while social attributes of a threat actor are more qualitative and ordinal. Having multiple measures provides a more expressive evaluation of the threat but can be complicated and messy. Conciseness attempts to combine these several measures into a smaller, simpler picture that is easier to understand at a glance and is more accessible to audiences not familiar with the ins and outs of cyber threat intelligence.
gTIC’s metric has two components that address the problems of both expressivity and conciseness. The first, and core, metric itself is six different measures of a threat actor, some comparable and some not. Hexagonal radar charts are useful in visualizing the measures together. The second component is a simple, scalar value that combines the six into a single summary.
Why have two measures when one is the product of another? Expressivity. There are multiple different ways that combinations of the six measures produce the same combined score. This creates the misleading perception that if two combined scores are the same, then the two different threat actors are identical. However, by including the radar graph along with the combined score, even untrained readers can compare the two shapes and see that they differ even if they are not able to fully express why. The three overarching capabilities are measured based off technical, operational, and targeting capabilities, each of which are further broken into two measurable attributes.
There are two threat actor attributes that describe its technical capabilities: acquisition and adaptability. Acquisition describes how an actor gets their tools with less sophisticated actors downloading free software and more sophisticated actors writing their own tools from scratch. Adaptability reflects how quickly a threat actor can adjust their Tactics, Techniques and Procedures (TTPs) in response to a changing defensive landscape. A highly-adaptive actor is quick to adopt new technology and abandon old techniques that might elevate their Operational Security (OPSEC) profile.
A threat actor’s or threat group’s operations value describes social aspects that revolve around a threat actor’s attacks. Publicity is how open a threat actor is with identifying themselves regarding attacks or campaigns, or how much they value their OPSEC. Inexperienced actors might brag openly on social media while savvy actors keep silent. The organization or structure of a threat actor group is difficult to infer but speaks to their capabilities. An individual working alone can achieve some measure of success, but a group can do more, and a well-organized and well-coordinated group much more yet.
The final two threat actor measures relate to their targeting of victims. Breadth of attack describes how focused a campaign (or series of attacks) is. Narrowly focusing a campaign requires more reconnaissance and patience on the part of the attacker. The duration measure is the typical length of an attack carried out by this actor. Some attackers are satisfied with quick, flash-in-the-pan attacks while others plan lengthy deployments that demand increased OPSEC and stealth.
Figure 1 and Figure 2 demonstrate the final graphical output of this method of viewing and comparing threat actors’ risk scores based of Optiv gTIC’s calculation.
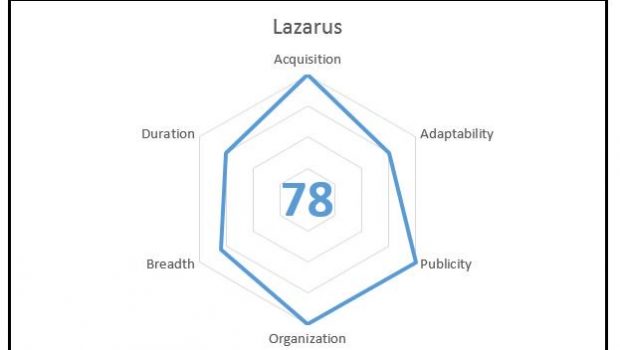
Figure 1: Threat actor metric radar chart of Lazarus, a threat actor group attributed to the North Korean government.

Figure 2: Threat actor metric radar chart for IsHaKdZ, a lone cybercriminal and hacktivist assessed to be of Algerian descent
Concluding Remarks
Scoring intelligence analyses is not a hard score. Any intelligence analysis may be incomplete and/or contain qualitative descriptions that do not map well to quantitative measures. Even Sherman Kent, widely considered the father of intelligence analysis, was unable to succeed in establishing a quantifiable process for intelligence analysis. These shortcomings push current threat intelligence analysts to prioritize the concrete, technical indicators of cyberattacks in their reporting. While analysis based on technical indicators is important in determining a risk, incorporating intelligence about the social aspects of cyber threats can add new dimensions in situational awareness. This improved sense is useful for organizations looking to focus their attention on the most relevant threats, or cyber threat analysts who want to provide advance warnings of future cyber threat activity.







Gloss