#HITBCyberWeek D2T2 – The Sum Of All Fears, When ICS/SCADA Are Compromised – Mars Cheng
iSpeech.org
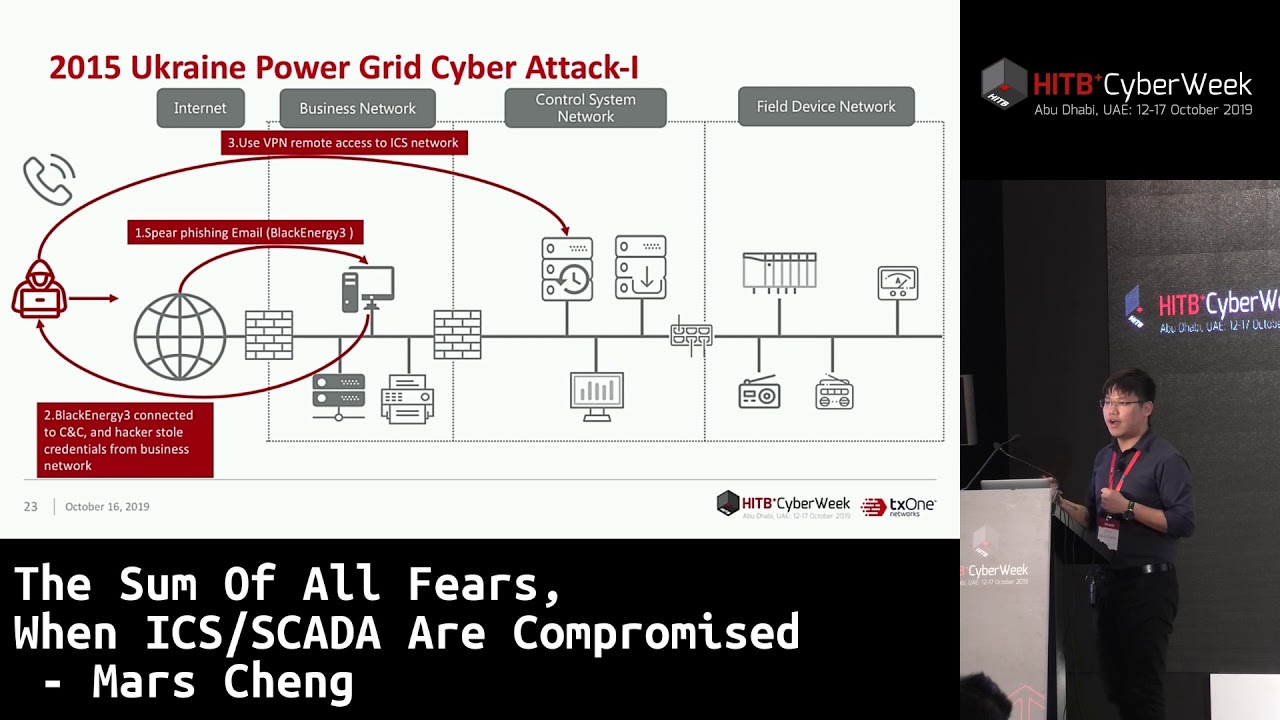
In the past, the cybersecurity issues of Industrial control systems (ICS) are neglected. However, ICS/SCADA connects with people’s lives which consists of power, water, traffic, manufacturing and multiple industry. In the past 10 years, more and more ICS/SCADA cybersecurity incidents are happened which may cause loss of life and property, and if we live without power, water, communication, traffic. That is a terrible thing. That is why we need to care about ICS/SCADA cybersecurity issues, and make sure we are in a security environment.
In this presentation, we first talk about the background knowledge of ICS/SCADA, and what kinds of security threats and attack vectors in ICS/SCADA. And then, we analyze an Industrial communication protocol, and write Lua plugin for Wireshark and exploit code as a hacker. In this part, we provide demo which shows hackers hack LC with Industrial communication protocol and PLC’s service to compromise ICS/SCADA. After hacking demo, we demonstrate the rotection strategy to secure ICS/SCADA. When we know how hackers attack ICS/SCADA, we know how to defend and deploy our protection strategy to achieve the most effective results.
===
Mars Cheng is a Cyber Threat Researcher with TXOne Networks’s IoT/ICS Security Research Labs and Trend Micro. His research interests include ICS/SCADA security, threat hunting for IoT and ICS/SCADA, cryptography, and Web/IoT/Mobile/ICS/SCADA penetration testing. Before joining TXOne, Mars was a security engineer at National Center for Cyber Security Technology (NCCST) in Taipei, Taiwan. Mars has given several talks at ICS Cyber Security Conference (USA), HITCON CMT, TWISC@NCHU, and etc. Moreover, he was also lecturer at HITCON Training, Ministry of Education (Information Security Incubation Program, ISIP), Ministry of National Defense in Taiwan, and etc. Since 2018, he delivered more than 7 + CVE-IDs, and 3 SCI top journals about cryptography.
source







Gloss