Five Eyes countries issue best practices for cyber incident response
A week after Canada’s intelligence allies issued a joint advisory to organizations on cyber incident response, this country has yet to publish the document on its website.
The Five Eyes intelligence co-operative of Canada, Australia, New Zealand, the United States and the U.K. last week announced a Joint Advisory on Technical Approaches to Uncovering and Remediating Malicious Activity, a lengthy playbook for network and infosec pros for incident investigation.
However, while the document is available online on other nations’ cyber information websites, it can’t be found on the site of the Canadian Centre for Cyber Security. “We are currently having the advisory translated in French and expect to post it on our website by mid-week,” Evan Koronewski, a media spokesperson for the centre, said in an email to IT World Canada this morning.
According to a news release, the joint advisory highlights technical approaches to uncovering malicious activity and includes mitigation steps according to best practices. “These are long-standing challenges we’ve observed when organizations are responding to cyber incidents, and we’re pleased to join our partners in raising awareness about these critical measures,” said, Scott Jones, head of the centre, in the press release.
Here’s a link to the English version of the advisory on the site of the U.S. Cybersecurity and Infrastructure Security Agency (CISA).
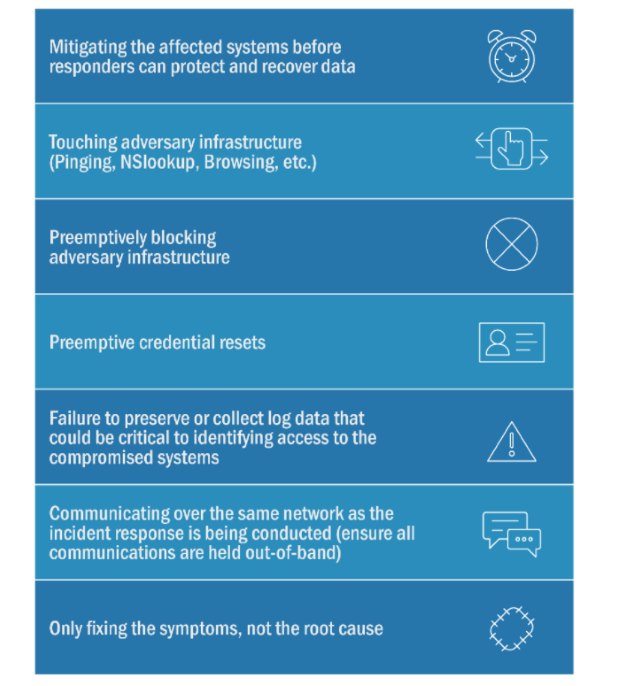
Among the most interesting parts of the advisory is a section on common mistakes made in incident response.
“After determining that a system or multiple systems may be compromised, system administrators and/or system owners are often tempted to take immediate actions,” says the advisory. “Although well-intentioned to limit the damage of the compromise, some of those actions have the adverse effect of modifying volatile data that could give a sense of what has been done; and tipping the threat actor that the victim organization is aware of the compromise and forcing the actor to either hide their tracks or take more damaging actions (like detonating ransomware).”
When addressing potential incidents and applying best practice incident response procedures, the advisory says network and security pros should:
- First, collect and remove for further analysis of relevant artifacts, logs, and data;
- Next, implement mitigation steps that avoid tipping off the adversary that their presence in the network has been discovered;
- Finally, consider soliciting incident response support from a third-party IT security organization to provide subject matter expertise and technical support to the incident response, ensure that the actor is eradicated from the network, and avoid residual issues that could result in follow-up compromises once the incident is closed.
The advisory also reminds the professionals that lots can be done before an incident. “Properly implemented defensive techniques and programs make it more difficult for a threat actor to gain access to a network and remain persistent yet undetected. When an effective defensive program is in place, attackers should encounter complex defensive barriers. Attacker activity should also trigger detection and prevention mechanisms that enable organizations to identify, contain, and respond to the intrusion quickly.
“There is no single technique, program, or set of defensive techniques or programs that will completely prevent all attacks. The network administrator should adopt and implement multiple defensive techniques and programs in a layered approach to provide a complex barrier to entry, increase the likelihood of detection, and decrease the likelihood of a successful attack.”
Related Download  Sponsor: CanadianCIO
Sponsor: CanadianCIO
Cybersecurity Conversations with your Board – A Survival Guide
A SURVIVAL GUIDE BY CLAUDIO SILVESTRI, VICE-PRESIDENT AND CIO, NAV CANADA
Download Now







Gloss