Dead System Analysis: Computer Security Lectures 2014/15 S1
iSpeech
This video is part of the computer/information/cyber security and ethical hacking lecture series; by Z. Cliffe Schreuders at Leeds Beckett University. Laboratory work sheets, slides, and other open educational resources are available at http://z.cliffe.schreuders.org.
The slides themselves are creative commons licensed CC-BY-SA, and images used are licensed as individually attributed.
Topics covered in this lecture include:
Dead System Analysis
Why do offline analysis?
Prevent further harm
May not trust live analysis (Rootkits and Trojanised software)
Analysing the evidence
Collecting the evidence
Creating a “disk image” of the hard disk drive or partition
Or just accessing the HDD contents directly
Accessing the evidence
Write blockers
Read-only mounting, advantages and disadvantages
Disk image-based analysis
View and search contents via a graphical interface
Hex views
Support for viewing certain file formats
Support for certain evidence identification, and using hash sets
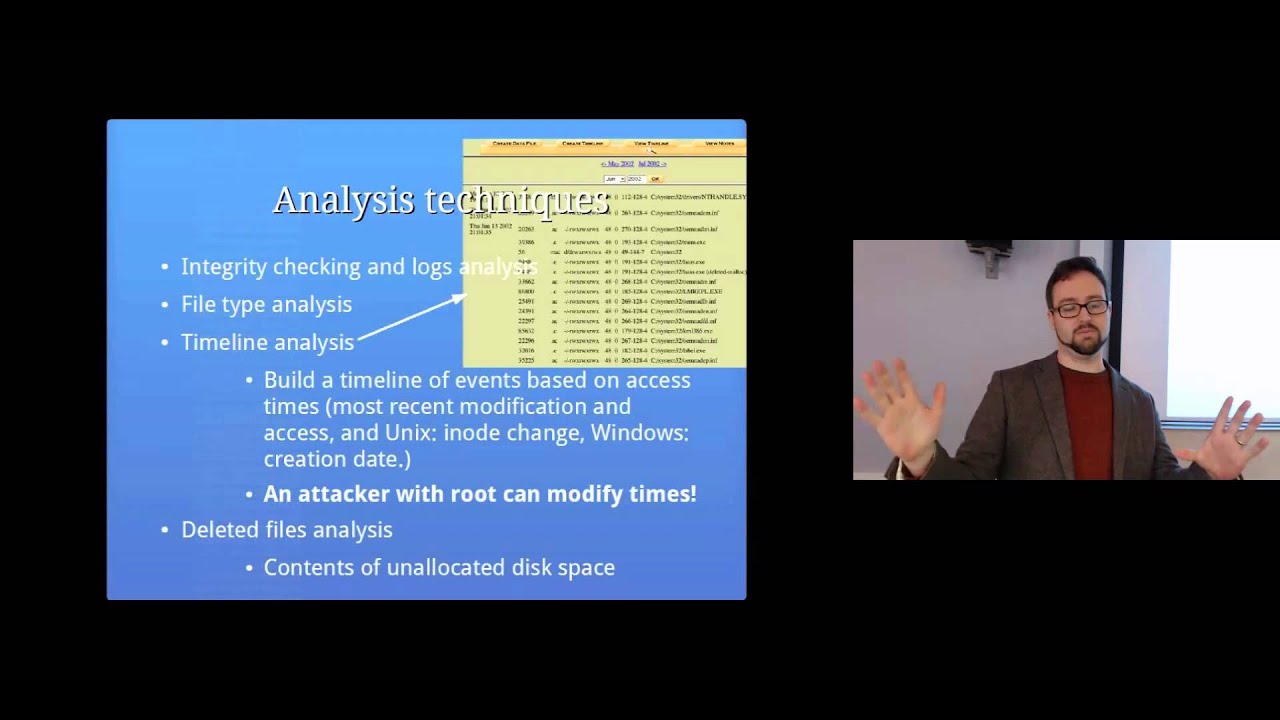
Analysis techniques
Integrity checking and logs analysis
File type analysis
Timeline analysis
Deleted files analysis
Contents of unallocated disk space
Some software tools: Autopsy / the Sleuth Kit™ (TSK)
Helix incident response
Conclusion
video, sharing, camera phone, video phone, free, upload
2015-01-05 14:26:38
source







Gloss