Cybersecurity incident response: Lessons learned from 2021
SecureWorks announced the themes and trends of cybersecurity incidents recorded in 2021 so you can better protect your business in 2022.
Huge incident response services providers have a unique view on threats and trends in computer attacks. They can see attackers’ modus operandi evolve through time and can provide a unique view.
SEE: Security incident response: Critical steps for cyberattack recovery (TechRepublic)
SecureWorks covered more than 450 security incidents in 2021 and published its feedback on it. Incident responses always provide food for thought on increasing security and are a great source for knowing what the current threats are.
Most incidents were financially motivated
A large 85% of incidents handled by SecureWorks in 2021 were financially oriented, while government-sponsored threat attacks only represented 5% of the activity. About 9% remaining consists of deliberate or accidental actions from employees that caused security incidents (Figure A).
Figure A

Initial compromise
Forty-three percent of the initial access was gained by threat actors by exploiting vulnerabilities in internet-facing devices. Credentials theft came second with 18% of observed initial access. Credential theft englobes credential stealing, but might also refer to credentials bought on the Dark Web or to initial access brokers, or obtained via brute-force attacks or password spraying attacks.
This is a real shift from what SecureWorks observed in 2020: Credential-based access was the most common way of getting an initial compromise on a targeted company (Figure B).
Figure B
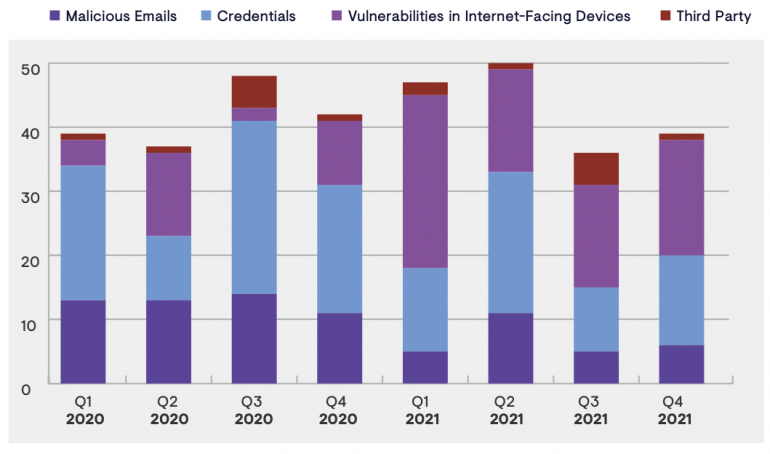
Several reasons might explain that situation, according to SecureWorks. For starters, the increased use of multi-factor authentication might have led to attackers avoiding credential theft and looking instead to exploit vulnerabilities that do not require any authentication. Another reason might be that it is pretty easy to exploit proof-of-concept code published shortly after the public disclosure of vulnerabilities. That possibility of quickly having code that exploits a vulnerability, coupled with bulk scanning for targets, can quickly bring an attacker to conduct widescale exploitation of vulnerable devices in several companies at the same time.
Finally, publicly released proof-of-concept code for exploiting a vulnerability on internet-facing devices can also generate more incident response cases, as happened with the ProxyLogon vulnerability in March 2021.
Trends in threats
Here are the latest trends noticed by SecureWorks in cybersecurity threats.
Ransomware is here to stay
As observed by all the computer security in 2021, ransomware is a very active threat and will probably stay that way. SecureWorks incident response data does not indicate any reduction in ransomware activity, despite the U.S. government putting ransomware at similar priority as terrorism and several ransomware attackers being caught in 2021.
Misconfigured MFA and user behavior are concerns
Credential theft and abuse is the second most used method to gain access to a targeted company, yet most of these accesses are successful because the victim organizations did not implement MFA and only relied on single-factor authentication.
MFA can significantly lower the abuse of valid credentials obtained by the attackers, yet it has to be implemented properly.
Attackers do find ways to bypass MFA to get to their objectives. One method consists of exploiting legacy authentication protocols such as IMAP and SMTP for example. These protocols might be in use in companies or may not have been disabled, which is a major concern regarding MFA, as these protocols cannot enforce it.
Even if MFA is properly implemented, user behavior might be a problem and help attackers. Successful attacks in the wild have been witnessed with MFA being bypassed by attackers because of multiple MFA push notifications which brought users to eventually approve one of the push notifications.
Bad knowledge of the MFA authentication might also help attackers. The “notification fatigue” phenomenon brings users to accept whatever application asks for MFA. Using MFA notifications that request a code from the user instead of a one-click choice (accept or refuse) is one way to mitigate that risk.
Be extra careful with cloud solutions
While it sounds attractive to shift resources into managed cloud solutions, which provide security controls offered by the cloud provider, it must be done properly.
A careful inspection of all the security components and controls offered by the provider needs to be done. The fundamentals of security must be there, starting with controlled accesses and logging of activities done on the cloud service.
How to prevent cyberattacks in 2022
SecureWorks provides a top 20 recommendations in its report.
- Performing regular vulnerability scans. Exploiting vulnerabilities has been the most used initial access method for attackers. Audits of internet-facing web systems and content should also be done frequently.
- Monitor for newly registered spoofed domains on the internet. A careful monitoring of all new domains impersonating or trying to abuse a company and its brands might help discover attack attempts even before they actually start.
- Control access carefully, and make IP address allow lists. Network segmentation should also be done in the company’s IT infrastructure, so that an attacker gaining access to a part of the network will not be able to access another.
- Improve backup strategies and procedures. Ransomware attackers generally try to render backups useless in addition to encrypting the company’s data, so good backup strategies and storage out of the network is a must have. SecureWorks also raises the problem of restoring backups of known-clean data: if done too quickly, it might destroy evidence needed for good incident response.
- Implement MFA properly, and fully disable and remove default or generic accounts.
- Implement DKIM and SPF authentication for email. This is to avoid fake emails sent by attackers impersonating the company.
General recommendations apply as usual: Keep your systems and software up to date, implement an endpoint detection and response solution and apply the principle of least privilege to account access.
Disclosure: I work for Trend Micro, but the views expressed in this article are mine.








Gloss