Cryptography Lesson #2 – Adversaries and Games
iSpeech
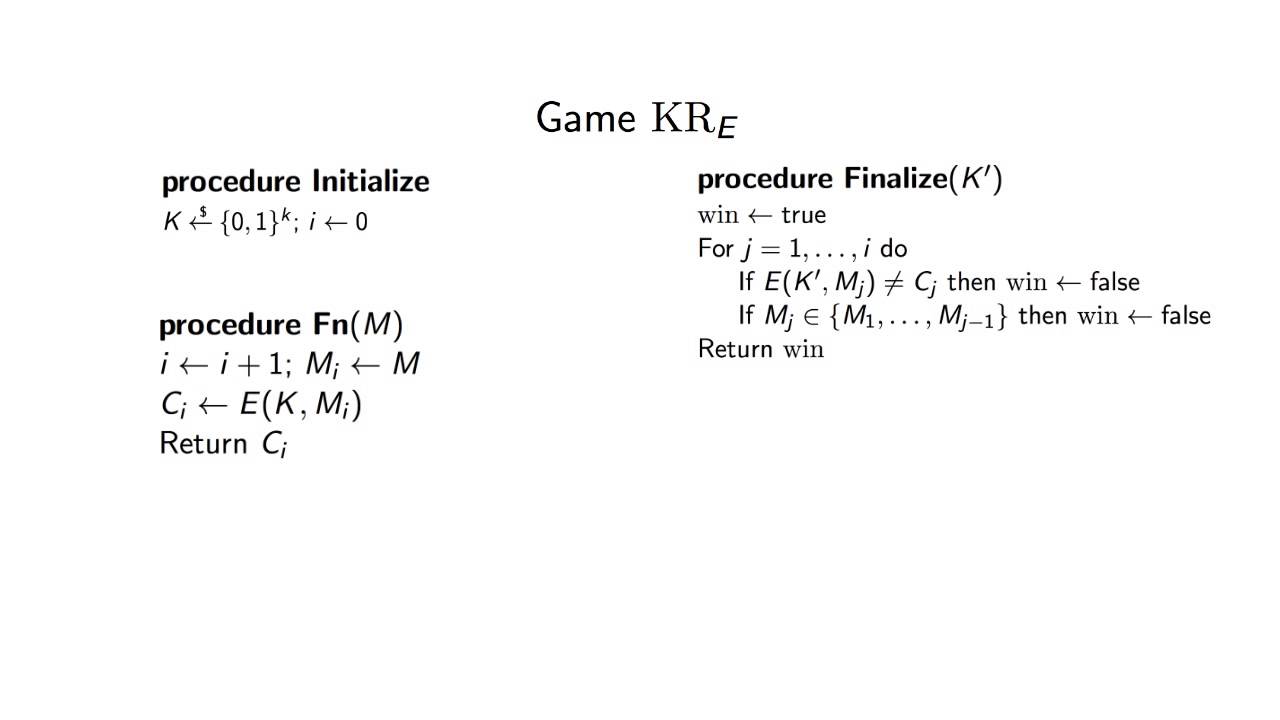
In this tutorial, we will give an overview of how games and adversaries are used to evaluate cryptographic schemes. We will focus on how games are structured, and give an example of how an adversary might play a game.
2015-06-11 07:41:05
source







Gloss