Client-Side Protection Against DOM-Based XSS Done Right ™
iSpeech
by Martin Johns & Sebastian Lekies & Ben Stock
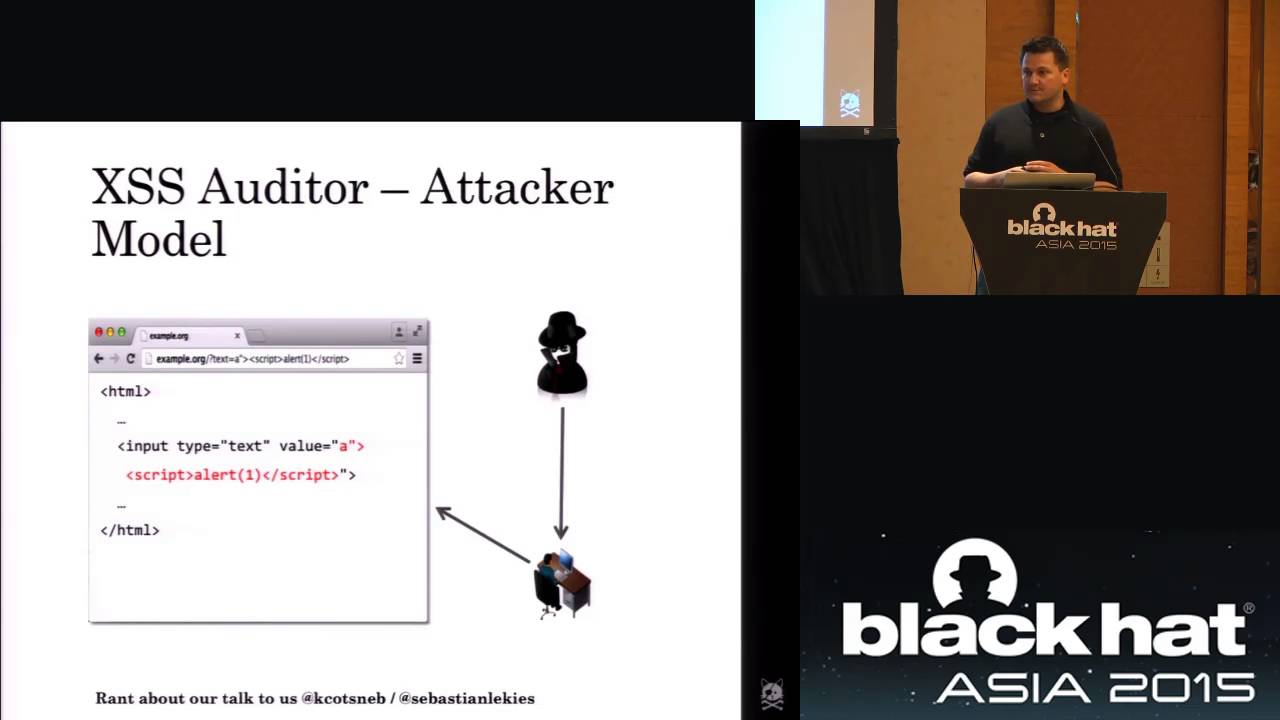
Cross-Site Scripting (XSS) is one of the most severe security vulnerabilities of the web. With the introduction of HTML5, the complexity of web applications is ever increasing and despite the existence of robust protection libraries, Cross-Site Scripting vulnerabilities are nowadays omnipresent on the Web. In order to protect end users from being exploited, browser vendors reacted to this serious threat by outfitting their browsers with client-side XSS filters. Unfortunately, as we had to notice, the currently provided protection is severely limited, leaving end-users vulnerable to exploits in the majority of cases. In this talk, we first present an analysis of Chrome's XSS Auditor, in which we discovered 17 flaws that enable us to bypass the Auditor's filtering capabilities. We will demonstrate the bypasses and present a tool to automatically generated XSS attacks utilizing the bypasses. Furthermore, we will report on a practical, empirical study of the Auditor's protection capabilities in which we ran our generated attacks against a set of several thousand DOM-based, zero-day XSS vulnerabilities in the Alexa Top 10.000. In our experiments, we were able to successfully bypass the XSS filter on the first try in over 80% of all vulnerable Web applications. Thus, it appears safe to state that the current client-side defenses against DOM-XSS are insufficient to protect end-users. However, unlike general XSS, in the DOM-based variant, all significant information is readily available. Hence, we present an alternative XSS filter design that reliably detects successful XSS attacks via client-side taint tracking in the JavaScript engine. Unlike the current approach, our filter does not rely on coarse approximation but on precise data flow information that allows us to robustly stop DOM-XSS for good.
2016-08-29 17:38:35
source







Gloss