Building a Successful Internal Adversarial Simulation Team – Wild West Hackin’ Fest 2017
Powered by iSpeech
Wild West Hackin' Fest 2017
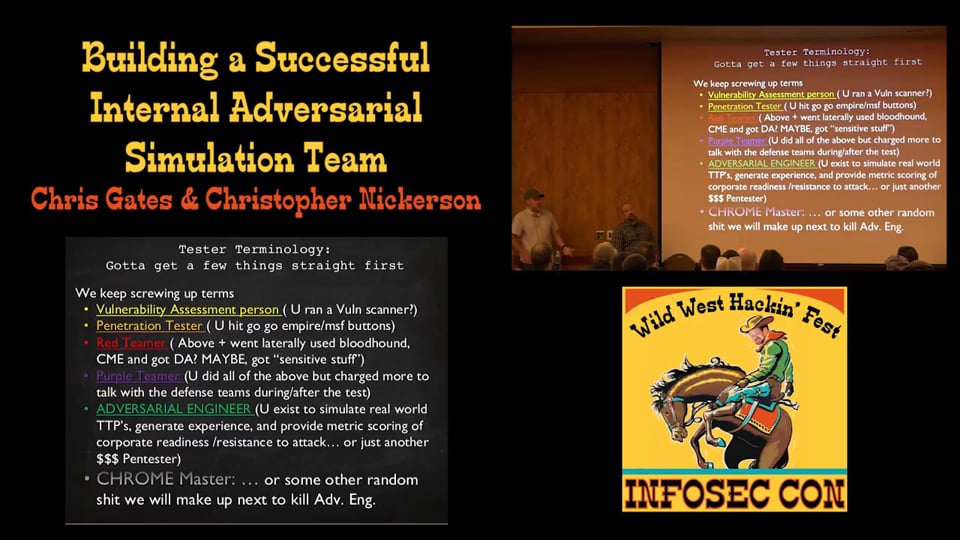
The evolution chain in security testing is fundamentally broken due to a lack of understanding, reduction of scope, and a reliance on vulnerability “whack a mole.” To help break the barriers of the common security program we are going to have to divorce ourselves from the metrics of vulnerability statistics and Pavlovian risk color charts and really get to work on how our security programs perform during a REAL event. To do so, we must create an entirely new set of metrics, tests, procedures, implementations and repeatable process. It is extremely rare that a vulnerability causes a direct risk to an environment, it is usually what the attacker DOES with the access gained that matters. In this talk, we will discuss the way that Internal and external teams have been created to simulate a REAL WORLD attack and work hand in hand with the Defensive teams to measure the environments resistance to the attacks. We will demonstrate attacks, capabilities, TTP’s tracking, trending, positive metrics, hunt integration and most of all we will lay out a roadmap to STOP this nonsense of Red vs BLUE and realize that we are all on the same team. Sparring and training every day to be ready for the fight when it comes to us. This is an update to our 2016 Brucon talk. We plan to discuss what have we accomplished regarding the above in the last year. We plan to show how we have progressed with the automation of attacker activities and event generation using MITRE’s Cyber Analytics Repository & CAR Exploration Tool (CARET) along with pumping these results to Unfetter (https://iadgov.github.io/unfetter/) for aggregation and display in a useful format.
source







Gloss