Bug in Anesthesia Machines Allows Changing Gas Mix Levels

A vulnerability in the firmware of some anesthesia machines used in hospitals could be abused to change normal functionality up to the point of adjusting the level of inhalational substances.
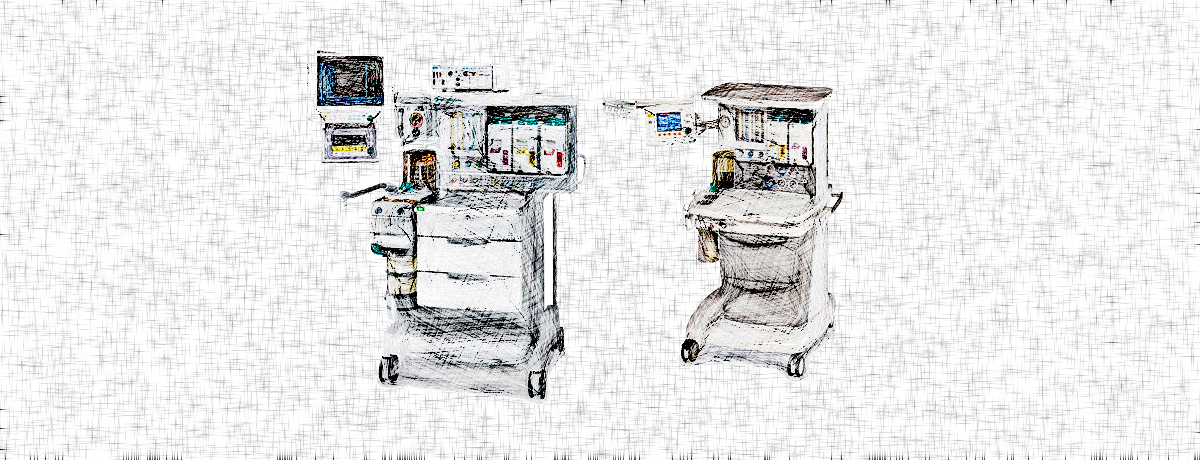
The flaw affects GE Aestiva and GE Aespire anesthesia systems, models 7100 and 7900, from GE Healthcare (part of General Electric Company) and permits sending them commands over the local network.
A threat actor would need to be on the same network as the vulnerable machines and there is not need for special privileges. If the system is connected to a terminal server, knowing the IP address of the targets is not necessary.
No authentication or special privileges needed
Elad Luz, Head of Research at CyberMDX, a cybersecurity company focusing on medical devices, discovered that an attacker could force a vulnerable device into using a less secure version of the communication protocol it uses.
This downgrade attack would allow not only remotely adjusting the composition of the anesthetic gas mixture but also suppressing alarms, changing the time and date on the system, and modifying the barometric pressure.
According to the researcher, the attack is possible with no user interaction and the machine "does not require or use authentication."
The concentration of anesthetic substances may differ from one patient to another depending on the physiological side effects they have, individual conditions, and duration of their effect. All this is governed by procedures and protocols that ensure the correct dosage for each individual.
A change in the concentration of the anesthetic gas may have a negative impact on the patient. For this reason, the anesthesia systems are typically connected to the network for constant monitoring of their current state.
“The potential for manipulating alarms and gas compositions is obviously troubling. More subtle but just as problematic is the ability to alter timestamps that reflect and document what happened in surgery," - Elad Luz
Luz further explains that the integrity of time and date settings also alters trust in an audit's conclusion, an issue of utmost importance in medical centers. According to the researchers, exploiting this bug could enable commands that would affect the following:
- Gas composition input: sets concentration of inspired/expired oxygen, CO2, N2O and anesthetic agents; also capable of setting barometric pressure and selecting the anesthetic agent type.
- Silence alarms: the machine's alarm is designed to generate a continuous loud noise until drawing someone's attention and having the underlying patient/device conditions attended to. (Exploiting the vulnerability in question can allow a bad actor to send commands to silence the alarm so that the noise is only briefly heard.)
- Date and time set.
CyberMDX calculated a moderate severity score of 5.3 out of a maximum of 10 for this vulnerability. This may seem like a low risk, but every security failure in a medical device can have drastic consequences.
The company validated these possiblities by running partial tests on real machines. To avoid potentially dangerous conditions that would last for a longer period, the team verified only the command for silencing the alarrm.
In a report today, CyberMDX says that "adjustments to settings for chemical constitution and time can have complicated and potentially long-lasting consequences that were best to avoid in a real hospital environment."
Affected customers should expect from GE Healthcare updates that fix the vulnerability along with additional security information on this page.
In mid-June, another CyberMDX and ICS-CERT published details about vulnerabilities in the firmware of Alaris Gateway Workstation, which allowed taking ful control of any devices that connected to them.
All vulnerabilities have been released to the public in coordination with ICS-CERT with recommendations for mitigation possibilities.
Update [7/9/2019, 17:30 EST]: The department of Homeland Security, through ICS-CERT, published an advisory about the vulnerability in Aestiva and Aespire anesthesia machines, providing recommendations from the vendor to mitigate the risk.
Using secure terminals to connect the anesthesia systems to the network via serial ports offers a swath of security features that would prevent unauthorized, remote access. Secure terminals come with encrypted communication, VPN service, user authentication, network controls, and the posisblity of logging the activity. There is also audit capability and secure device connection and management options.
Additional steps include:
- minimizing exposure through network segmentation
- device isolation
- system access restrictions
- disabling unnecessary accounts, protocols and services







Gloss