Backups, Redundancy, and the Cloud: Computer Security Lectures 2014/15 S1
iSpeech
This video is part of the computer/information/cyber security and ethical hacking lecture series; by Z. Cliffe Schreuders at Leeds Beckett University. Laboratory work sheets, slides, and other open educational resources are available at http://z.cliffe.schreuders.org.
The slides themselves are creative commons licensed CC-BY-SA, and images used are licensed as individually attributed.
Topics covered in this lecture include:
Backups and Redundancy
confidentiality, integrity, and availability
Objectives
Recover from events
Prevent problems
Data Backups
Backups can help mitigate various risks
Backup plans
The plan should meet any Recovery Point Objectives (RPO) and Recovery Time Objectives (RTO)
Specifies: Who, how, and how often backups occur, How and for how long backups are stored, Where backups are stored, What data is backed up, How to recover backed up data
Backup plan considerations: Value of data, vs cost of backup, how fast does recovery need to happen?
Backup media
Types of backup: Direct attached storage, Network-based, Internet/cloud, Network attached storage (NAS)
Networked systems and filesystems
Backup levels
Epoch (full) backup: Everything is copied
Differential backup: Only changes since the last full backup
Delta encoding: stores the differences between versions, rather than complete copies
Incremental backup: Only changes since the last backup (including differential backups)
Multilevel backup involves levels:
Level 0 = Full backup
For example, monthly
Level 1 = Changes since level 0 backup
Multilevel differential
Multilevel incremental
Restoring a file from three-level backup
Restoring an entire system
Other backup methods
System images
Continuous data protection: Real-time backup, saves every change to a backup storage
Version control: Commits versions of files to a repository, Preserves entire history, Eg: Git, Subversion
Storage considerations
Security of backups
Physical security
Encryption (esp. if stored off-site)
File permissions, if stored on servers
Data retention laws
Backup software
Lots of backup tools available, including free and proprietary solutions
Software considerations
Many provide a graphical front-end to standard Linux/Unix tools (for example ark)
cp, tar (tape archive), dd (data dump), cpio, dump/restore, rsync - copy differences, over a network, rcp: insecure copy across network (don't use this), scp
Redundancy
Data redundancy, such as RAID
Hardware redundancy
Power redundancy
Server redundancy
Redundancy advantages and disadvantages
Redundant array of inexpensive / independent disks (RAID)
Hardware-based RAID
Software-based RAID
Choosing Hardware or software RAID
Firmware-based RAID
RAID levels
Data striping: Segments sequential data and places it across drives
Parity: Error detection, and in the case of RAID, error correction
Mirroring: disks containing the same data
RAID levels
RAID 0: striping, no redundancy
RAID 1: mirroring
RAID 3: striping, dedicated parity disk
RAID 5: like 3, but parity is stored along with data across all disks
RAID 6: like 5, but two parity blocks
Hot spare: An extra disk, not used until a failure, may automatically rebuild onto the spare
Capacity
RAID and Linux
Need to monitor the logs for disk failures
Log shipping
Log shipping AKA warm standby
Load balancing: distribute workload to redundant hardware
Failover: a load balancer can stop sending requests to hardware that is not available
Redundancy is not backup
Backups can go wrong
Backups can help
Cloud computing: a network of remote servers providing services:
Infrastructure as a Service (IaaS) – hosts VMs, such as servers or desktops (VDI)
Platform as a Service (PaaS) – hosts access to a managed server to host software
Software as a Service (SaaS) – use remote software
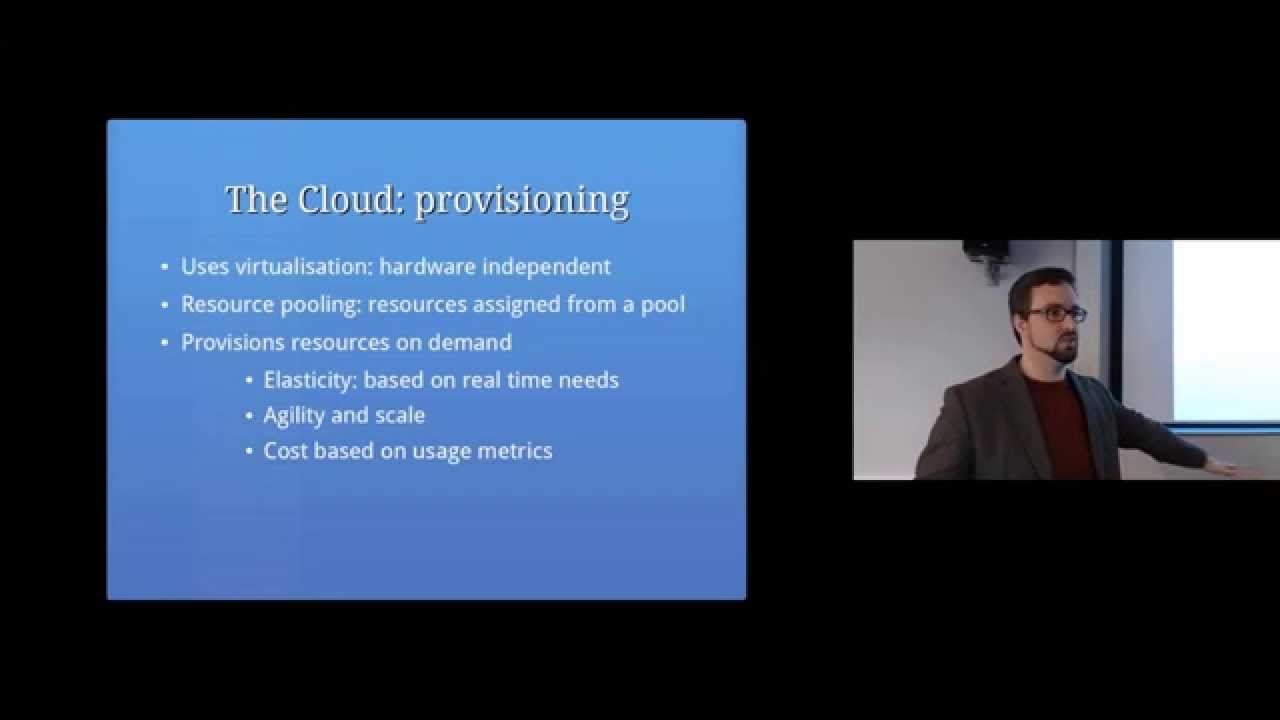
The Cloud: provisioning uses virtualisation: hardware independent
Resource pooling: resources assigned from a pool
Elasticity: based on real time needs
Agility and scale
The Cloud: deployment - Public/Private/Hybrid cloud
Redundancy and the Cloud
Failover to a caching service
Backups and the Cloud
SaaS data storage services
Consumer storage: Google Drive, Dropbox, Amazon Cloud Drive
Online backups / data storage
Encrypted backup
Security and the Cloud
Multi-tenant
Many physical servers
OS, platform, database, virtual network, and app security
A single security breach can have wide reaching impact
Data is stored and processed on computers owned and operated by someone else
Privacy issues
Legal and compliance issues
Out of your control
Conclusion
video, sharing, camera phone, video phone, free, upload
2015-01-05 13:48:32
source







Gloss